Cyberattacks and how they work

Cybercriminals in 2019 managed to expose more than 165 million records of confidential data across 1,365 known breaches.
But how do they get in, how long do they stay and what are they there for? The answers to these questions are in the 2020 Compromise Flashcard produced by compromise assessment company Lumu.
The infographic compiles recent industry research data to show how companies are being attacked, the types of data attackers are seeking, which industries are most frequently targeted, and the duration for which an attacker is able to dwell inside the network without being detected.
You can see the full graphic below.
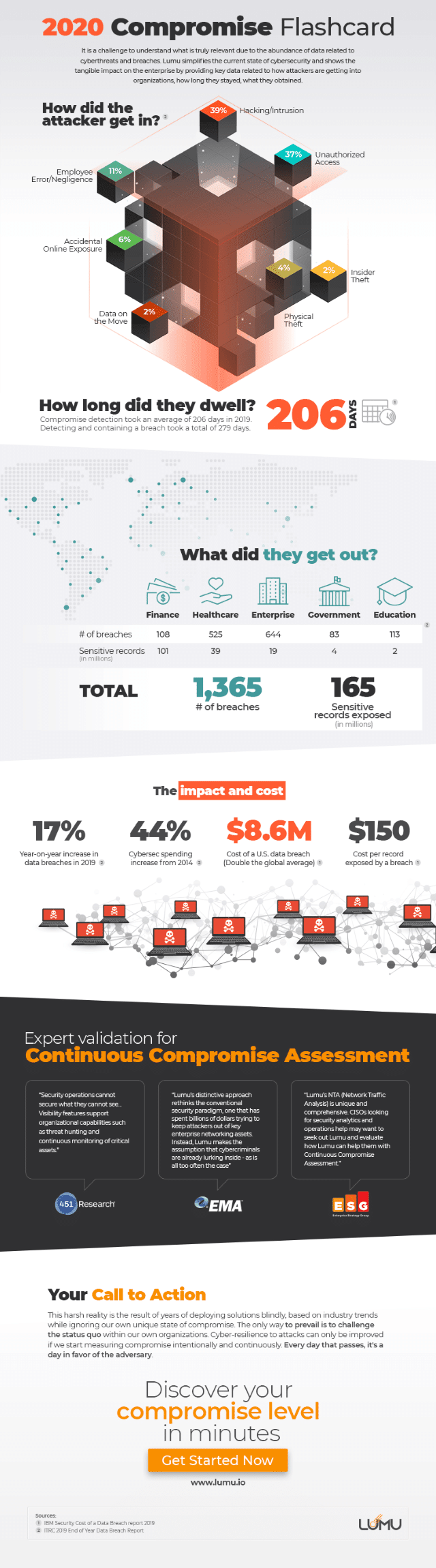
Photo credit: Tashatuvango/Shutterstock
