Log4j continues to be a problem for enterprises

It's now over three months since the Log4Shell vulnerability, affecting the Log4j logging framework, first appeared.
But new research from Randori shows that it's still giving headaches to enterprises and identifies the top 10 attackable targets.
VMWare Horizon tops the list, with 10 percent of large enterprises having an internet-exposed instance. If hacked, it gives a hacker downstream access. VMware Horizon was hit within a couple weeks of the vulnerability appearing and access brokers are selling access via Log4j exploits.
Next come Jamf and PingFederate which are being used by one to two percent of the enterprise market. Like VMware, they provide an attacker with additional downstream access to other systems -- authentication (Ping), automation (Jamf) mechanisms -- which provide an excellent opportunity for attackers to pivot and expand their operations.
Because Log4j is buried deep into layers and layers of shared third-party code, it's likely that there will continue to be instances of the Log4j vulnerability being exploited in services used by organizations that use a lot of open source.
Of course many suppliers, such as Jamf, have issued patches but security relies on them being applied. Jamf chief information security officer Aaron Kiemele says, "Jamf has not been impacted by the Log4j vulnerability since December. We issued a series of patches in December to address the CVEs that impacted Jamf at that time. We continue to closely monitor for any additional issues associated with Log4j to ensure the ongoing safety of our customers."
Businesses are advised to treat assets with a lot of access as being most attackable. Start looking at the things you most want to protect and work back from there. This means adding logging and monitoring around key applications as well as assets with a lot of access such as VPNs and remote access tools.
There's a full list of the most widespread and most attackable Log4j applications below, more information and the full report are available from the Randori blog.
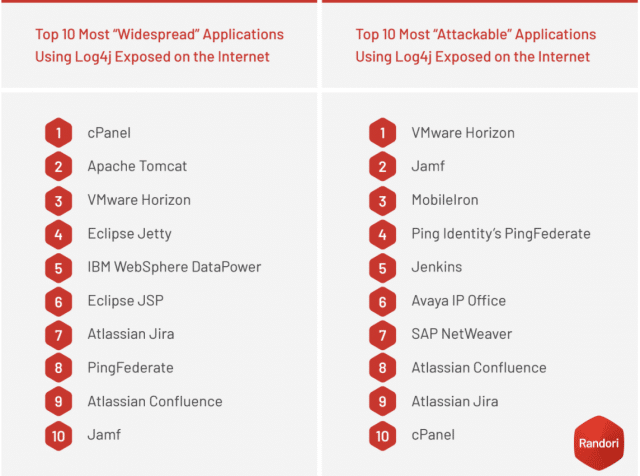
Image credit: billiondigital/depositphotos.com
