Understanding common internet-facing footholds exploited by bad actors
Ransomware remains a persistent threat with real-world consequences, with the ability to halt business operations, and cause significant reputational and financial damage.
Ransomware incidents have gained the attention of the general public with attacks like the Colonial Pipeline that led to fuel shortages, and WannaCry that led to British hospitals diverting patients. Despite an increased level of awareness at the board level, ransomware attacks continue to plague organizations.
One reason why the threat of malware in general is so hard to eradicate is that cyber criminals find new pathways to deliver malicious code. An organization’s digital supply chain is a prominent example of these newer attack vectors, leveraging the vendors, suppliers, and other third-parties with network access as footholds. As organizations’ own internal networks become more secure, a third-party may have weaker security and thus provide an easier attack vector for cyber criminals. If compromised, the attackers can spread to connected networks, leaving behind malware to enable a ransomware attack. Even if an organization isn’t ransomed itself, having a critical supplier facing an attack can hurt business operations.
RDP is a primary vector for ransomware
Another common attack vector is Remote Desktop Protocol (RDP), which was exploited in the aforementioned WannaCry attack. Given the rise of remote and hybrid work, more organizations are looking for external remote access for employees but may not always consider all the security risks of their setup as robustly as they should.
RDP is the proprietary protocol that allows a user on one computer to connect to and control a remote computer and is commonly used by admins to fix issues on a remote system. In recent years it has become popular in cloud computing to assess and/or manage virtual machines. Unfortunately, it is very easy to expose RDP unintentionally by leaving the RDP port open to the internet, including on a forgotten system, cloud instance, or network segment. The protocol is easily detectable and a brute force attack can be launched even by unskilled attackers.
Recently, according to BlueVoyant’s threat intelligence analysis, threat actors have more frequently probed for open RDP ports as an easy-access attack vector.
It is therefore an almost foregone conclusion that RDP will be targeted sooner rather than later if left open on a network. In fact, open port and vulnerability scanning continue to be key footholds for cybercriminals, both within the organization and the vendor ecosystem. Open ports are being probed almost instantly after being exposed to the Internet and continuously by multiple actors.
According to CISA, in 2021, RDP was one of the top-three initial attack vectors for ransomware events, often involving either brute force or stolen credentials for access. Analysing a sample of 15,000 companies throughout 2022, we found that one fifth of the vulnerabilities within their ecosystem were RDP-related. Whilst attackers need credentials to bypass the authentication of RDP weak passwords, poor operational security and increasingly effective harvesting campaigns make the acquisition of these credentials easier than it should be.
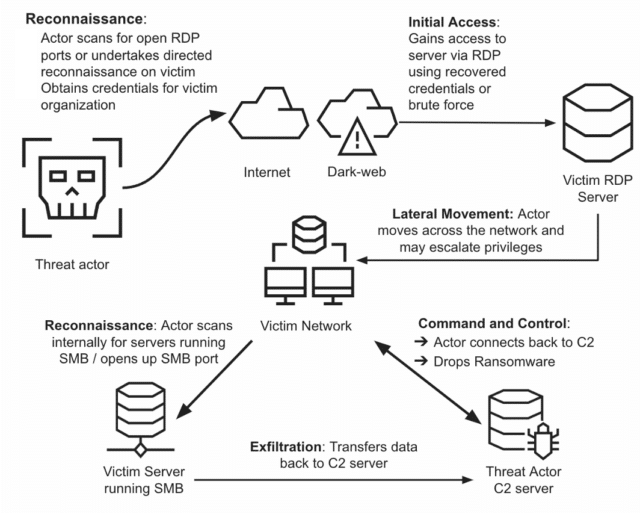
Typical RDP exploitation flow to deploy and operate ransomware
The race to patch
Zero-day vulnerabilities or emerging vulnerabilities (EVs) are another common foothold that bad actors utilize and are one of the most notable threats to organizations due to their unforeseen and time-sensitive nature. These new vulnerabilities are disclosed every week and companies across the world need to be constantly vigilant over which can affect them.
One of the major challenges in reducing risk in an extended ecosystem is ensuring that all organizations and their suppliers do not have open, unpatched instances of vulnerable software, especially when considering that the average time for a newly disclosed Zero-day vulnerability to be compromised is two weeks or less. When an EV is disclosed publicly, a race starts between attackers who are actively searching for this foothold in organizations, and IT teams trying to patch the vulnerable systems. Yet the patching rate of EVs remains remarkably low, months after disclosure.
For example, vendor Atlassian announced on June 3rd 2022 that it had been made aware of an active vulnerability in its Confluence Data Centre and Server software. Only 30 percent of vulnerable organizations patched within the first 10 days, which meant that 70 percent remained exposed beyond the average time to exploitation, representing a major risk for these organizations, according to BlueVoyant’s threat intelligence.
Implementing preventative measures
What measures should organizations adopt to prevent the preventable?
To help mitigate the risk of ransomware attacks, organizations need to consider the security of their supply chain. They should know which vendors, suppliers, and other third-parties have network access and which are critical to business continuity. Organizations should then continuously monitor their supply chain so that if any signs of or compromise occurs, they can quickly work with third parties to remediate the issue.
When it comes to RDP, organizations need to be aware of the risks. Most importantly, ports should always be closed unless there is a valid business reason for them to be open. Any remote access should be regularly audited by security teams to ensure nothing is unnecessarily left open. For necessary access, organizations should require the use of VPN, multi-factor authentication, and limit login attempts.
And finally, organizations should patch or implement alternative risk mitigation strategies for all critical vulnerabilities as soon as possible, within the average time to exploitation (around two weeks or less) and encourage vendors to do the same. Supply chain risk management best practices, monitoring internal services and technologies and making thoughtful decisions on what data to share are all critical to ensuring that you can prevent the preventable and reduce the organization’s risk exposure.
Dan Vasile is Vice President, Strategic Cyber Advisory, BlueVoyant.