Implementing post-quantum cryptography (PQC) in modern systems

Most experts predict a quantum computer capable of breaking RSA and ECC encryption will be developed within the next decade. Virtually all of today’s security systems utilize RSA and ECC algorithms, which means the window to defend against quantum-powered attacks is rapidly closing.
The National Institute of Science and Technology (NIST) has developed new post-quantum cryptography algorithms that are secure against quantum computing attacks. These standards were released in August 2024. With new standards finalized, companies must act now to begin migrating to PQC.
Aligning with CNSA 2.0
Migrating to PQC will be critical to maintaining compliance with the Commercial National Security Algorithm Suite 2.0 (CNSA 2.0) requirements. CNSA 2.0 mandates the use of the following PQC algorithms:
- XMSS/LMS for code signing use cases
- ML-DSA (CRYSTALS-Dilithium) for all digital signing use cases, including code signing
- ML-KEM (CYRSTALS-Kyber) for general encryption and key exchange use cases.
These algorithms will replace RSA, Diffie-Hellman Key Exchange, ECDH, and ECDSA. In addition, CNSA 2.0 also defines timelines for adopting these algorithms, with deadlines beginning in 2025.
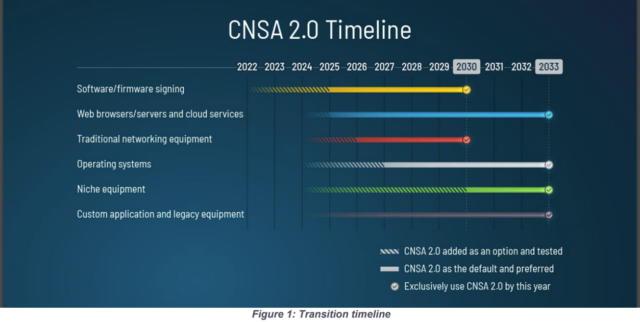
The urgency to adopt PQC algorithms is even more critical when you consider the design cycle for new devices. A system being designed today may not reach production for one to three years. That system may be produced for several years before a major redesign cycle. Once deployed, many systems will remain in operation for a decade or more. These devices are built to last, but their security is not. It is imperative to begin migrating to post-quantum cryptography for these devices.
Additionally, harvest now, decrypt later (HNDL) attacks are a major and immediate security concern. In HNDL attacks, hackers capture and record encrypted data now with the intent of decrypting it once quantum computers have advanced sufficiently to break today’s algorithms. For organizations with data that must be kept secure long into the future, these attacks are a serious threat. Companies must act now by implementing the Kyber (ML-KEM) PQC algorithm in their communication protocols to protect against these attacks.
Migration to PQC algorithms with FPGAs
With new PQC standards from NIST now available, developers can begin migrating to these new algorithms. However, implementing PQC algorithms is not without its challenges. Organizations face a learning curve on the adoption of new algorithms. The key sizes, signature sizes, and performance characteristics for PQC algorithms differ significantly from classical algorithms. They also differ significantly between various PQC algorithms.
Organizations must familiarize themselves with these new algorithms. Understanding the tradeoffs will help determine which algorithm to adopt for each use case. Organizations should choose a trusted partner that has experience and expertise with PQC algorithms and should begin implementing proof of concept solutions to gain the knowledge needed to begin migrating to PQC algorithms.
Field Programmable Gate Array (FPGA) technology will play a vital role in implementing PQC across broad range of applications including datacenters, networking systems, connected cars, and industrial robots. FPGAs are inherently flexible solutions. This enables them to be reprogrammed to implement PQC algorithms and to align with evolving regulations and standards. This flexibility also means that FPGAs have uncommon longevity, resulting in added cost savings.
The inherent flexibility of FPGAs makes them an ideal solution for real-time Hardware Root of Trust (HRoT) devices. FPGA-powered HRoT devices can be tailored to specific security needs to create a more robust HRoT environment suited to the unique security requirements of their applications.
Because of their flexible nature, FPGAs serve as ‘crypto agile’ solutions that are essential for transitioning to PQC standards. With innate programmability, they can streamline over-the-air firmware updates to enable developers to upgrade embedded hardware with PQC algorithms and patch vulnerabilities within existing systems.
As the cybersecurity landscape continues to evolve, FPGAs are poised to play a pivotal role in navigating this complex environment. Their unique capabilities directly align with the demands of emerging regulations that prioritize flexibility and resilience. In a world where security threats are constantly changing, FPGAs offer a powerful and adaptable solution for building secure systems that comply with evolving regulatory frameworks.
Image Credit: Justlight / Dreamstime.com
Mamta Gupta is Sr. Director of Strategic Business Development Security, Telecommunications & Data Centers, Lattice Semiconductor. She brings with her over 20 years of FPGA experience in product development with special focus on security, Aero-space and defense segments. Upon joining Lattice in 2019, Mamta has led various strategic initiatives to establish Lattice as the Trusted security solutions provider and to develop secure and flexible solutions for the telecom customers. Mamta holds a Master of Science degree in Quantum Physics from University Delhi, India and professional certifications in IC Engineering and Fabrication from UC Berkeley and Advanced Program Management from Stanford University.
