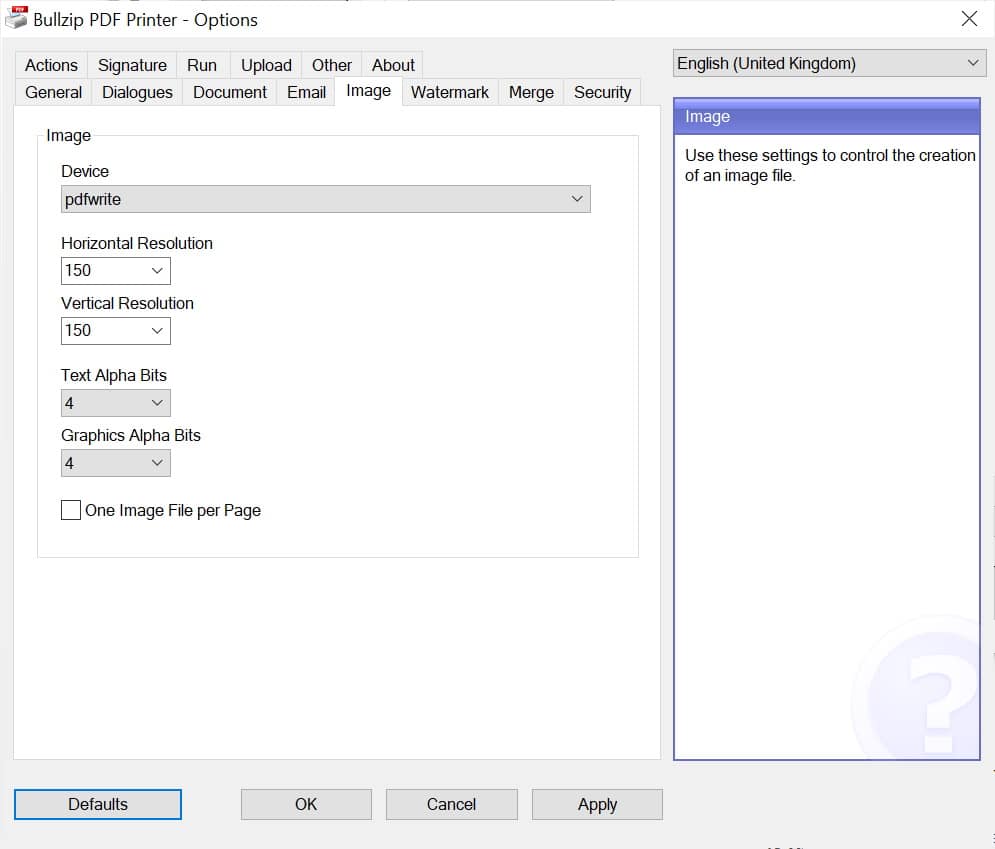
Bullzip PDF Printer 12 offers support for printing multiple documents at once
It used to be that creating PDF files required expensive software, but this is no longer the case. Things have changed so much that even Windows 10 includes the option to turn documents into PDFs and there are numerous other more feature-packed PDF printers out there as well.
One such free tool is Bullzip PDF Printer which is free for not only personal use, but also in commercial operations with up to 10 users. The newly released version 12 of the software now includes support for multiple printer ports, meaning concurrent printing of multiple documents is possible.

The fashion of the future: What will tech bring next?
Like many industries, the world of fashion has become intrinsically linked with technology. From the textiles used in garment manufacturing to creating a sustainable supply chain, technological advancements are set to innovate fashion in countless ways. For a long time, the processes used in the fashion sector have remained remarkably unchanged. In the coming years, however, we can expect big things.
As of 2020, fashion generates an estimated $664 billion revenue, making it one of the biggest industries in the world. Because of this, technological innovations within this sector are set to be nothing less than world changing. If implemented correctly, technology in fashion could make an unfathomable change in creating a greener, cleaner world. From big data to Blockchain technology, let’s take a look at the innovations that we can expect to see in the world of fashion over the coming years.

How to enhance security education, training and awareness for employees
Many organizations struggle to develop education, training and awareness initiatives that are impactful, engaging and resonate with the audience. Typically, a lack of funding forces organizations to run plain, dull, repetitive awareness campaigns, or they just do enough to meet regulatory requirements. This approach to changing security behavior is fundamentally flawed -- however, there are several cost-effective approaches that organizations can use to change, promote and sustain good security behavior.
Firstly, the idea of 'blanket awareness' is dead -- all content needs to be tailored and contextualized to specific role requirements. For example, a senior executive will not experience the same threats as a marketing manager, so why should they both have to complete the same training course? Each employee should be equipped with the necessary knowledge and skills to identify and respond appropriately to role-specific threats. Security mentor schemes are particularly helpful in upskilling movers and joiners, and a robust threat intelligence and incident management capability can help inform awareness campaigns of emerging and common threats that each role is likely to experience.
Technology in manufacturing: Why innovation must never stop
Technology’s grip on modern-day life has tightened over the last decade, especially in the world of manufacturing. Innovation, efficiency, safety and hygiene have been the order of the day for quite some time, with the latter gaining more spotlight due to the coronavirus pandemic.
With production lines in many industries, such as pharmaceutical, food and beverage to the automotive industry, needing to work around the clock to support the US economy and beyond, innovation -- and the use of technology -- in factories and warehouses must continue well past the point a vaccine is found for the virus. Today, we look at how the evolution of technology has benefited the manufacturing sector so far and what the future looks like in a post-pandemic world.

A practical guide to cloud migration
According to FLEXERA 2020 State of Tech Spend Report, the top three IT investments that organizations of all sizes are considering in the current scenario are digital transformation, cybersecurity, and cloud migration. Another report from Research and Markets says the global cloud computing market is expected to grow from USD 371.4 billion in 2020 to USD 832.1 billion by 2025. There are multiple reasons why organizations are considering and prioritizing cloud adoption. While cost optimization is one of the key reasons, it’s not the ONLY reason.
Businesses know that they’ll have to accelerate their digital strategy to ensure growth in the coming years. Moving to the cloud will provide them the much-needed elasticity, agility, flexibility, and security to achieve and sustain that growth. The COVID-19 pandemic has also brought to the forefront the need for a robust remote workforce -- and that’s another reason cloud readiness has gained additional importance.

Four steps to securing sensitive data in the cloud
For organizations across the globe, the journey to effectively manage, and extract value from, sensitive data in the cloud isn’t a new one. IT and security professionals have long struggled with challenges to the easy adoption of cloud technologies, and the question of how to ensure that data, including personal identifiable information (PII) or sensitive data, stays safe and compliant with regulatory requirements, without sacrificing data utility, remains a top challenge.
In 2020, the ongoing global pandemic increases this obstacle as remote work drives businesses to move more activity to the cloud quickly. A cloud usage survey released in May found organizations had already surpassed their 2020 cloud spend budget by 23 percent -- highlighting the question of how well data is being protected during this shift to home offices.

Is it time to retire your VPN?
Historically, one of the most popular tools used to connect remotely to a corporate work environment has been a virtual private network -- VPN for short. A VPN enables corporate users to send and receive data across public networks such as the internet through a secure encrypted tunnel, providing something akin to a direct, private connection to the corporate network.
However, VPN technology was introduced at a time when business IT environments reside on business premises, and did not include distributed elements that are now commonplace, such as cloud computing, mobile devices, and flexible remote work policies. Even as VPNs have adapted to stay relevant to some of the changes in how people now work, they have struggled to keep up with the modern threat landscape.

5 generations of SaaS: How the value proposition has changed, and why
SaaS, especially B2B SaaS, has 5 generations (so far) that don’t only show the growth of technology but also the changes in the market. I call them generations because they are not only built one on top of the other, but also co-exist simultaneously, each continuing to bring value as new generations come after them.
With each consecutive generation, SaaS has moved from full "hands free" automation towards greater customization and flexibility for the customer. Why has the value proposition changed? And what does it say about the market for SaaS today?

The tech industry and recycling: The need-to-knows
The tech industry holds the trump card when it comes to innovation surrounding recycling -- considering they are, in fact, the innovators. As the world becomes more environmentally conscious and the EU sets targets to make all plastic packaging recyclable waby 2030, businesses across the globe are looking for innovative ways to reduce their own waste through the production process and have a more circular economic approach.
As the tech industry strives to become a role model for recycling, we discuss the approaches some tech companies have taken and the benefits of taking recycling seriously.
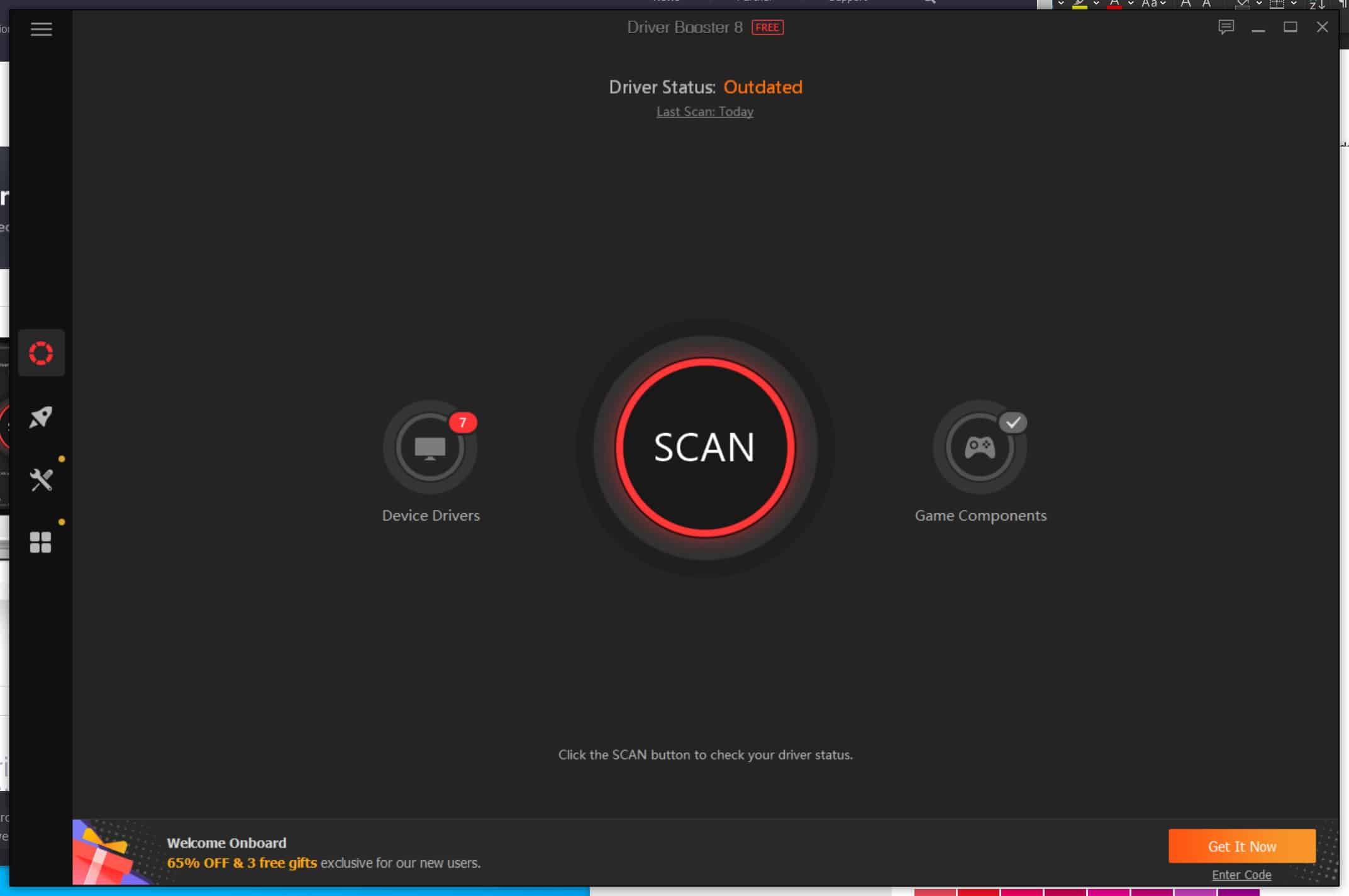
Driver Booster 8 keeps your drivers up to date even without an internet connection
Keeping drives up to date is an important part of system maintenance and optimization, and a recent update to Windows 10 removed a useful driver updating option. The newly released Driver Booster 8 is here to help, making it easy to keep all of your drivers up to date, even when you do not have an internet connection available.
The driver database has been massively expanded, and IObit says that the software now provides access to more than 4.5 million drivers and game components. The updated version of the software also gives two possible routes for updating drivers depending on whether you like to live life on the cutting edge or not.
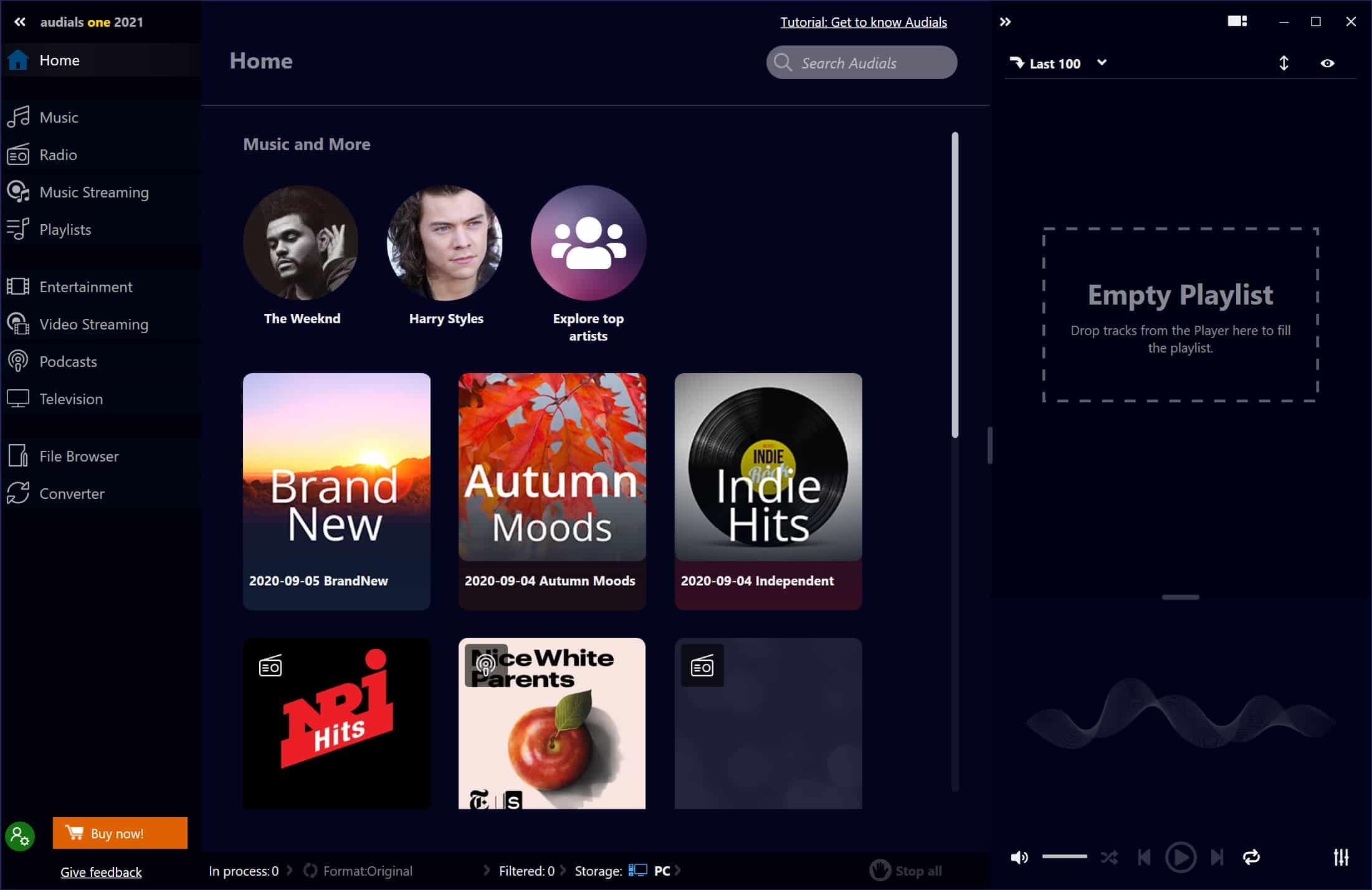
Audials One 2021 records audio and video streams faster than ever before
The updated Audials One 2021 not only enables you to watch movies and shows from a range of streaming video providers and listen to streaming music services, but also to record content from these streams so you can keep audio and video forever for offline viewing and listening. With this latest update, speed is the order of the day, but there have also been a number of important new features added.
On the audio front, Audials One 2021 lets you listen to a wide range of online radio stations, as well as streaming music from the likes of Spotify, Deezer and Tidal. Importantly, it is also possible to record individual tracks, entire shows, or anything that is played through your soundcard.

Hybrid cloud application delivery in financial services
The financial services sector is experiencing significant commercial disruption coupled with rapid innovation as established institutions strive to become more agile and meet evolving customer demand. As a result, financial services organizations are undergoing rapid digital transformation to meet changing customer needs and preferences, and to compete with a new generation of digital-native competitors. Hybrid cloud environments play a key role in this strategy, allowing greater speed, flexibility, and visibility over application delivery than on-premises data centers while also reducing costs.
But the move to hybrid cloud introduces new challenges as well. So, as financial services organizations plot their strategy for transformation, firms must make critical technical decisions about the clouds and form factors best suited to host their hybrid environment. They also need to consider how they will secure web applications against evolving threats such as ransomware, data theft, and DDoS attacks through measures such as DDoS protection and using a Zero Trust model. At the same time, they must also maintain regulatory compliance, governance, and auditability across complex, fast-evolving infrastructures.

Not all workloads are created equal
Choosing a Disaster-Recovery-as-a-Service (DRaaS) provider can be an overwhelming task, especially if your organization is using DRaaS as a first step into cloud services. There are many solutions to choose from including large providers like Google, Amazon, and Microsoft, and also smaller or more focused providers.
The decision to work with a cloud provider for DRaaS can be clearly defined by classifying your requirements and confirming that the provider that you choose completely meets those requirements. Large cloud service providers, or "hyperscalers," may seem like the best choice for your cloud needs. However, choosing a provider based solely on the size of the organization is not always the best criteria. Hyperscalers do provide certain advantages, but keep in mind that there are also benefits to choosing smaller cloud providers that will offer individual attention and deliver more customized services. Doing your due diligence while investigating all of your options can benefit you in the following ways.

How unified XDR platforms enhance security protection for the enterprise
Credential theft and forgery are among the leading stealthy cyber threats. The 2014 eBay breach that exposed the personal details of 145 million users is one of the high-profile cases of such surreptitious cyber-attacks. Bad actors obtained the usernames and passwords of legitimate users to steal information and compromise the organization’s database.
What makes credential theft and forgery more serious than most other cyberattacks is that the illicit access to systems or databases usually remains unnoticed for a long time. A successful attack is difficult to detect and resolve. In the case of the 2014 eBay incident, the hackers managed to maintain complete access to the user database for 229 days.
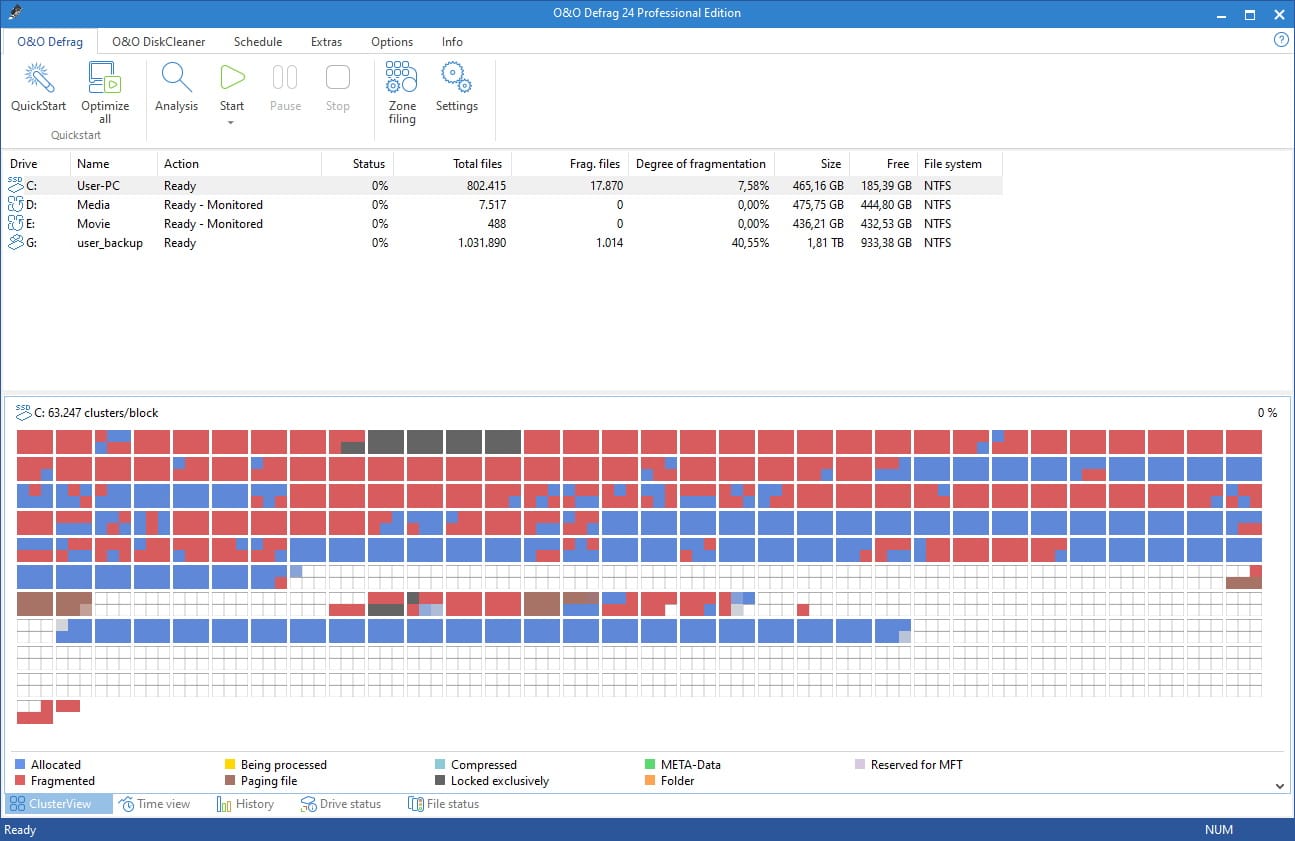
O&O Defrag 24 completely automates optimizing your hard drive
O&O Software has released the latest version of its hard drive optimization tool, O&O Defrag 24 Professional Edition. One of the key new additions to this version of the software is a unique "Install & That's All" feature.
This new feature aims to bring drive optimization to everyone, without the need for complex or time-consuming configuration. The idea is that you need simply install the software and it will immediately ensure that your drives are optimized at all times -- you may never have to open up the program! Of course, if you like the idea of manually tinkering with things, you can still do so.

