
COVID-19 apps: Social responsibility vs. privacy
The growth of coronavirus cases in a number of countries has led to talk about a second wave of the pandemic. According to WHO, disturbing news is coming from China, the US, Israel, South Korea, Iran and other countries. At the same time, privacy problems are arising with new force in COVID mobile apps.
It is a common opinion that Android app users don’t know how exactly their personal data and the information transmitted by the apps are actually used. Alarm signals of privacy breaking are coming from different places around the world. If you add to that the shortcomings and even errors on the part of developers -- the threat of unauthorized access to personal information increases even more.

Microsoft updates Remote Desktop app for Android with Virtual Desktop support
Microsoft has released a key update to its Remote Desktop app for Android. The app, which allows for the remote use of computers running Windows 10 Pro and Enterprise, Windows 8.1 and 8 Enterprise and Pro, Windows 7 Professional, Enterprise, and Ultimate, and Windows Server versions newer, now features full support for Virtual Desktops.
The update also brings the Android app in line with the iOS and macOS version, so all three versions of the app now use the underlying RDP (Remote Desktop Protocol) core engine. The latest version of the app also brings support for Android TV devices, but there's even more to look forward to.
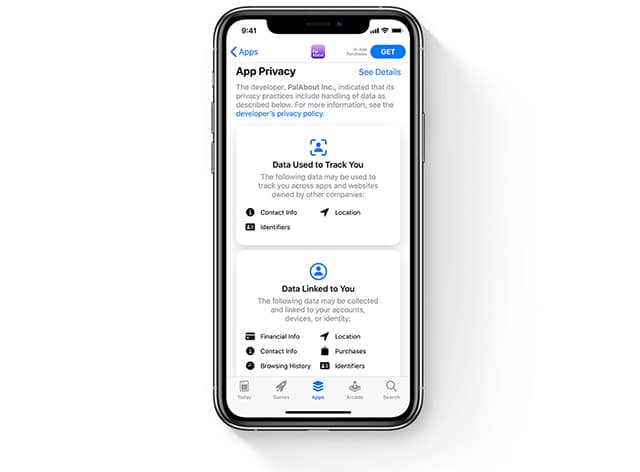
iOS 14 privacy labels are not enough
Apple pays more attention to privacy protection issues than its competitors. Well-defined privacy policies and rather severe restrictions on what user information an app or extension can get make Apple products more secure for users.
However, from the perspective of transparency, everything was not so obvious for Apple. The latest announcement shows that the corporation is ready to take a few more steps towards increasing transparency in the field of privacy protection.

e-voting can solve the voter fraud concerns plaguing US elections
In just four months, the United States will head into one of the most important Presidential election cycles of its history. Ensuring that eligible citizens are able to participate in the voting process will be critical.
Understandably, as COVID-19 continues to grip the nation and the world around us, American citizens are wary about turning out to vote in person, for fear of being in a crowd or lengthy line. Some startling facts drive home this point when you look at the state of Pennsylvania, for example. This year 1.8 million people have requested absentee votes, up from just 107,000 in 2016. This is further supported by a recent report commissioned by Okta, which found that 67 percent of Americans support mail-in voting to prevent the spread of COVID-19.

The power of enhanced WebRTC
With more digital communication tools available than ever before, enterprises and end users have started to demand more tailored options that can improve their experience and make it even easier to connect.
Web Real-Time Communication (WebRTC) is one such tool that can enhance deployment of voice and video and tools within browsers and apps.

Will automation rule over human interaction thanks to the coronavirus?
Thanks to advancements in technology, the need for human interaction -- when you shop for groceries, book a taxi, order a takeaway or watch the latest blockbuster -- has gone from necessity to nice-to-have, with self-service checkouts, apps to order cabs and kebabs, and streaming services all examples of automation that have everyday use.
Despite its influence on consumer behaviors, one of the perceived downfalls of automation is the limit it has on the reliance for humans to carry out certain tasks and jobs. A debate that has, and will, rage on for quite some time. But, with the current coronavirus pandemic, will automation become more of a necessity as we come to terms with social distancing and what life might be like in the future? Here we look at the role automation could play in the fight against COVID-19 and beyond.

Three industries benefiting from biometrics to fight COVID-19
The COVID-19 pandemic has accelerated the adoption of biometric technology across industries. From touchless payments at shops and restaurants to reduce the use of cash transactions to biometric-based contact tracing efforts, virtually every industry has had to readapt to meet the shift in customer and regulatory requirements.
The widespread adoption of biometrics was already underway when the coronavirus began to spread in early 2020. Now, companies are moving ahead with the installation of this technology to offer better safety, security, and efficiency to their customers. These three industries, in particular, are well-suite to see their operations advance as a result of biometric adoption.

The questions to ask to avoid cloud trade-offs
There is an old saying that there are no perfect solutions, only trade-offs. We have all experienced this trade-off situation in our lives at some point, when we must make a decision knowing that there is no perfect solution available and that we will be forced to compromise in some way.
This is one of the reasons why some people choose to put money in the stock market, they’re prepared to take a risk, while some people prefer to put money in savings accounts, where the payback is more predictable. The trade-off in this example is that you cannot put the same money in both places at the same time. You need to make your decision based on the existing trade-off of higher risk and return (stocks) or lower risk and return (savings account).

4 ways that HR teams can use Identity and Access Management (IAM) for secure remote working
As businesses start to take tentative steps out of the COVID-19 pandemic, we are still understanding what our 'new normal' is. In the backdrop of an ongoing pandemic, we’re taking a heightened risk-based approach to living our lives and working.
Businesses and departments that were unable to work remotely shutting down during the lockdown led to a negative impact on businesses, industries, and the economy as a whole -- you only have to look at the retail and hospitality sectors to see this. A paradigm shift has occurred, particularly with technology and its use in a post-pandemic world.

How to defend against hackers
As damaging as security threats can be, they’re also easily avoidable when you have the appropriate safeguards in place. For businesses in particular, investing in the right methods is essential.
Here are my top 7 tips for keeping your data secure.

Phishing attacks for the COVID-19 era: What to look out for
Despite the devastating recent outbreak of the novel coronavirus, phishing attacks continue to drag us and our businesses down. So how exactly do COVID-19 related phishing attacks work?
Cybercriminals have taken it upon themselves to wreak havoc and feed off the fears people have about the virus. Emails are being sent that ask their targets to open attachments containing information about the latest coronavirus statistics or news. Or, they claim to be from legitimate companies offering information about COVID-19.

All about quantum-safe certificates
The advent of quantum computers will render ECC and RSA encryption algorithms obsolete, requiring companies to migrate their computing systems and PKI infrastructure to new, quantum-safe cryptographic algorithms.
This migration of PKI solutions to quantum-safe crypto algorithms will pose many major challenges for many enterprises. All existing applications and systems will need to be updated to support the new quantum-safe algorithms now being developed in response to the threats posed by quantum computers. The process of updating to new algorithms requires significant engineering work and many systems will require extensive updates.

Can AI replace white collar jobs?
Let’s start with the definition of "REPLACE," from Merriam-Webster: To restore to a former place or position (e.g. replace cards in a file); To take the place of especially as a substitute or successor; To put something new in the place of (e.g. replace a worn carpet).
Now, let’s check the definition of "ENHANCE": To increase or improve in value, quality, desirability, or attractiveness (e.g. enhanced the room with crown molding); To increase or improve (something); To make greater or better (e.g. the products claim to enhance beauty).

How to securely comply with rising CCPA rights requests amid COVID-19
As California Consumer Privacy Act (CCPA) enforcement officially started July 1, affected enterprises (based on size, California customer base and business type) can no longer delay complying with the new law. CCPA grants California residents an array of new rights, starting with the right to be informed about what kinds of personal data companies have collected and why it was collected.
A June 2020 survey found that more than 20 percent of organizations were either somewhat unlikely to be, very unlikely to be, or didn't know if they would be fully compliant with CCPA by July 1. With only 14 percent of respondents CCPA compliant and nearly one-third of organizations just starting to plan for CCPA, enterprises need to be prepared for enforcement sooner than later to uphold the rights of California consumers and avoid non-compliance penalties, which can reach up to $7,500 per violation.

The importance of customer-centric digitalization in the next normal
Addressing the challenges brought about by COVID-19 should not be the only concern of businesses. It is equally important to look forward to the next normal or the situation after the pandemic. Nobody knows when the virus outbreak will end, but just like many other global health problems in history, it will eventually reach a conclusion.
The end of the pandemic does not automatically mean that all businesses will return to profitability. There will be improvements, but success is never guaranteed without the companies doing anything to secure it. Normalcy during and after the pandemic is unlikely to be the same as what people think it is. There’s the concept of the new normal. Then, there’s the next normal. Some are also floating the idea of never normal.

