Phishing attacks for the COVID-19 era: What to look out for

Despite the devastating recent outbreak of the novel coronavirus, phishing attacks continue to drag us and our businesses down. So how exactly do COVID-19 related phishing attacks work?
Cybercriminals have taken it upon themselves to wreak havoc and feed off the fears people have about the virus. Emails are being sent that ask their targets to open attachments containing information about the latest coronavirus statistics or news. Or, they claim to be from legitimate companies offering information about COVID-19.
Most malicious emails contain attachments or links, which when clicked or opened, can contain malicious software or viruses which will attack your device.
Coronavirus has taken many lives and continues to be a topic of conversation as lockdown in many countries starts to ease. Although we can’t predict for how long this pandemic era will go on, it is possible to take steps to protect yourself against phishing attacks related to COVID-19.
Fake Emails
In late March there were reports of an email phishing scam that was designed to lure recipients into downloading malicious documents. The documents were attached to fake emails from sender posing as a hospital.
The emails used scaremongering tactics to inform people that they had recently come into contact with someone who had COVID-19. This, as you can imagine, caused anxiety and unrest, convincing people to download an Excel document containing details of the nearest emergency clinic where they could be tested for coronavirus.
The emails read "You recently came into contact with a colleague/friend/family member who has COVID-19 at Big Country, please print attached form that has your information prefilled and proceed to the nearest emergency clinic".
How to protect against fake emails
This kind of phishing attack preys on users’ fears during the coronavirus pandemic. Any email containing instructions to download software or documents, or click on links should be viewed with caution. Unless you know the sender, do not open attachments or follow embedded links.
If the email seems genuine but you are unsure, research out to the company it supposedly came from first and ask for further information.
Fake Ads
With talk of potential cures or vaccines doing the rounds, the fake ad market is rife with product-based phishing. Scammers have been posting adverts claiming to offer cures for COVID-19 and often create a sense of urgency by stating "limited supply" or "act fast".
Clicking on an advert like this can result in malware being downloaded to your device. Alternatively, cybercriminals can obtain personal information and data about you in order to appear like they are going to send you something.
In some cases, you may be sent something in the post but it won’t be what these scammers are claiming you’ll receive. By the end of it, they will have your name, address, and bank account information, whilst you are left in the dark feeling vulnerable.
How to protect against fake ads
The best advice we can offer here is to not click on an advert about coronavirus unless it has come from an authentic source. If you are using a personal computer, you can hover your mouse over adverts or images that contain links to identify the source URL. If you don’t recognise the source, don’t click on the ad.
Currently, there is NO cure for COVID-19. So any company offering one is sure to be fake. Though it is completely understandable that people want to seek refuge from this virus, it’s important to keep your wits about you and not be tempted by companies claiming to offer treatment.
COVID-related Domains
Pandemic based phishing attacks are making use of the latest trends. We’ve seen malicious campaigns targeting recent news surrounding unemployment, welfare benefits, financial relief packages, children returning to school, and second waves.
One of the common themes that researchers have noticed is the number of COVID-related domains being registered every day (around 1,200). Now, more than ever, it’s super simple to create your own website using a website builder. It requires little to no skill at all and domains are cheap, easy and often free to come by.
But in many cases, scammers are purchasing these domains with the intention of attaching malicious software that captures your information before the link even loads. More than 25 percent of COVID-related domains are malicious, a large portion of which is being used for phishing attacks.
After the World Health Organization (WHO) declared a pandemic on 9th March, there was a significant spike in malicious activity around the world. In Pro Privacy’s COVID-19 malicious domain report, they used natural language word segmentation to identify the most common terms used by malicious domains.
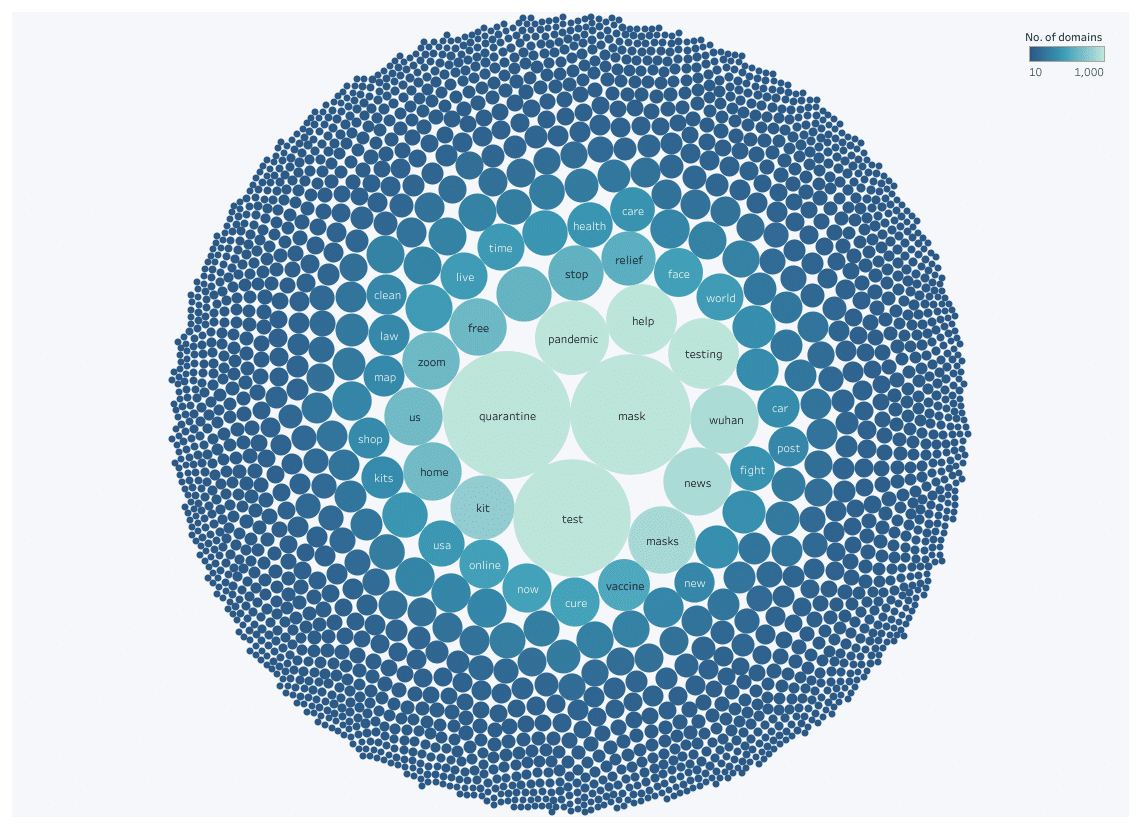
Conclusion
Phishing attacks are hitting individuals and businesses left, right, and center -- and no pandemic is going to put a stop to that. In fact, it’s become another baiting tool hackers use to scam people in a vulnerable situation.
It’s imperative that internet users treat all incoming emails and messages with caution. Emails creating urgency or encouraging individuals to share personal information are likely to be malicious.
As cybercrime continues to rise, we would encourage everyone to be vigilant -- even more so during the current global pandemic. If you’re ever unsure about an email or message, report it, question it and definitely don’t take it at face value.
Image Credit: Clokair / Shutterstock
Georgie Peru is a Content Contributor for UKWebHostReview. She is passionate about sharing her enthusiasm for technology through her content writing work, with a mission to help others learn and understand what makes the digital world so successful.