
3 secrets to boost user adoption
Analytics is a transformative tool for business. According to Hanover Research, four of every five users consider analytics integral to their business role. Three of four data pros claim they’d adopt a new analytics platform embedded into their existing workstream. As employees are relied upon to make more data-informed decisions more often, it’s imperative that they fully understand the insights that analytics provide. Equally critical is that those analytics contextualize data and bolster data literacy among everyone along the chain of command.
The desire for user-friendly data analytics in easily accessible formats is strong, and supplying them makes data analysis less overwhelming, more precise and, ultimately, profitable. To accomplish this, implement three key priorities to ensure the chosen analytics suit their purpose, are fully adopted and are continuously utilized.

Artificial intelligence and business: What will the future look like?
As per a study, 91.5 percent of the firms are reported to have an interest in investing in artificial intelligence technology. Growth in the use of automation, 5G, databases, cloud computing, and much more are driving the demand for artificial intelligence.
Various industries are incorporating AI in their processes to improve customer experience and business operations. Small and medium enterprises are utilizing this technology to optimize performance and functions at minimum costs.

How on-board internet access can encourage passengers to use public transport
It is fair to say that the internet plays a huge role in our lives. It keeps you company, offering you many options to kill time during moments of boredom. It provides you with all the information you want in a matter of seconds. It also allows you to search for feel-good music and ASMR videos to help you relax at the end of a busy day.
Therefore, it has become almost impossible to find a home that does not have an internet connection. Most pubs and restaurants have followed suit, with Wi-Fi codes in plain sight at the bar to invite guests to take advantage of the building’s free internet access. In this respect, public transport is adapting and upgrading too.

Designing security to mitigate growing ransomware threats
Ransomware has become a top-of-mind security concern for many organizations. High-visibility ransomware attacks have disrupted supply chains and inspired an Executive Order on Cybersecurity in the United States.
This is not surprising given that ransomware is a such a common and costly threat costing organizations millions.

Tech meets fitness: The revolution of fitness tracking apps
Gone are the days of measuring our heart rate by hand, to ensure we’re in optimal condition during our workout. Nowadays, there are many fitness tracking apps to provide us with comprehensive data about our health and fitness progress at the push of a button.
From fitness planner apps to wearables, there’s something for everyone who wishes to take their exercise routine further. But what’s the technology behind the fitness tracking apps revolution, and is there a market for it?

Crypto banks and emerging trends for 2022
Cryptocurrencies took the attention of investors and tech-savvy worldwide some time ago. Thanks to its rapid growth, the crypto industry has surpassed the $1 trillion market cap in 2021 and reached the all-time high of more than $3 trillion in the same year.
With regulations getting set in place, banks are getting more enthusiastic about including cryptocurrencies in their product offer.

Microsoft Word vs. Google Docs: Which is the best?
Microsoft Word vs. Google Docs: which one do you prefer? Many people grew accustomed to using Microsoft Word in school and now find it difficult to shift to Google Docs at the workplace. Notably, many businesses prefer Google Docs because it's web-based, so teams can collaborate in a document even though they don't work in the same office or department.
So, which is the best option? Below is a review of the features and benefits to help you decide on the right choice for you.

How retailers can beat the top four online shopping security threats in 2022
There’s an inevitable spike in online security threats accompanying the surge in online shopping over the past couple of years, mainly driven by the recent pandemic. As more and more retailers embrace and adopt e-commerce sites to expand their customer base, increased cybersecurity levels are a must to ensure a safe and positive customer experience.
As a business owner, the greatest threat that cyberattacks represent is loss of sales and unhappy customers, which can really make or break a business as a whole. Since many cyberattacks are executed in hidden and unsuspecting ways, identifying and battling them can become a challenge. Let’s take a look at the top four online shopping security threats and how to avoid them in 2022.

Through a glass darkly: Nike sues Lululemon over mirror
In my bio below you'll see a picture of me sporting my new digital camouflage Lululemon Surge Warm Half-Zip that had arrived the night before writing this. Inside the box was a card trying to sell me something called Lululemon Mirror. The image on the card was very similar to what Lululemon has on their site (see image at the top).
My first reaction was "This looks like something Nike would make. I wonder if it'll claim to own the IP rights."
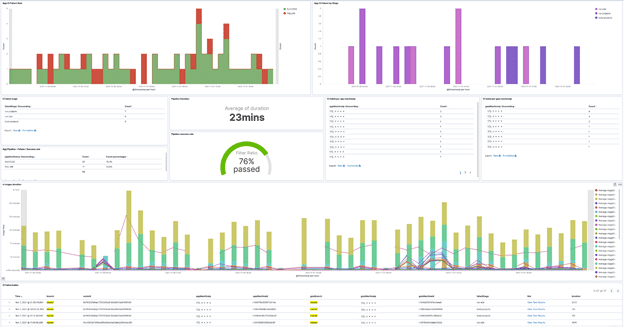
Overcoming observability challenges in the CI/CD Pipeline
When most companies monitor and analyze their software systems, they focus on the most obvious ones. But one essential service often slips through the cracks: the continuous integration/continuous delivery (CI/CD) pipeline. This poses three main observability challenges: pipeline investigation efficiency, pipeline performance, and the ability to access historical data.
Every time developers push out a new version, their pipeline run is triggered. A set of commands checks to make sure everything is valid, that the build process is all right, and that all tests have been passed. If everything checks out, the new service version is deployed to production.

Strengthen your company's security posture with risk quantification
Risk professionals work with uncertainty every day. They need to identify and prioritize which risks to address now versus later, consider many moving parts and rely on judgment and data to make informed decisions.
But how do they communicate those risks to stakeholders? Using "low, medium or high" classifications doesn’t always express the consideration risk requires -- especially since those terms don’t mean the same thing to everyone. If you told key stakeholders "there’s a possibility of rain tomorrow" before a company barbecue, how would they know whether to reschedule or put a few tents up? Is "possibility" enough information to make that decision, especially since not everyone equates possibility with the same level of probability?

To err is human, and that's what hackers are counting on
It's understandable if you've made thwarting ransomware your top cybersecurity priority for 2022. The number of successful ransomware attacks, which encrypt computers until victims pay the attackers to unlock their data, surged last year. Ransomware payments reported by banks and other financial institutions (PDF) totaled $590 million for the first six months of 2021, surpassing the $416 million for all of 2020.
When it comes to protecting your data center and endpoints (e.g., employees' laptops and mobile devices), ransomware should be top of mind. But when securing your cloud environments, don't worry about ransomware -- worry about the misconfigurations that lead to devastating data breaches.

Governing the ungovernable: Why cybersecurity must adapt to identity sprawl
You may remember the Colonial Pipeline ransomware attack. Launched in May of last year, DarkSide’s attack cost the Colonial Pipeline Company something on the order of $4.4 million dollars (though the FBI was able to claw some of that money back). The attack set the stage for President Biden’s Executive Order on cybersecurity, shut down pipeline production, and caused panic buying across the Southeast.
That’s how the Colonial Pipeline attack ended. It began far more simply: with hackers breaching the company’s networks through a virtual private network (VPN) account that was no longer actively in use.

Effective Contract Lifecycle Management (CLM) requires innovative, adaptable and knowledgeable solutions
As companies work to beat out the competition, taking a deeper look into contract management can be a driving force of success. When contracts accidentally expire or key milestones are missed, it can severely handicap business. Effective contract management improves workflow efficiency and leads to a more progressive and well-functioning organization.
Contract Lifecycle Management (CLM) is one of the fastest-growing and important innovations in business today. Spurred by the digital revolution advancing across virtually every key business sector, the CLM market is expected to grow over 13 percent annually for the next decade. But what is it, and why is it such an essential tool for businesses to utilize?

Reacting with confidence to a new Trojan horse cyber threat
It’s the sophisticated technology that enables the virtual assistant on your kitchen counter, the recommendation engines on your favorite streaming services, and so much more -- and there’s new evidence hackers can use it as a Trojan horse to deliver malware. Because this technology is increasingly embedded not just in your movie nights, but critical industries from healthcare to energy and banking, its newly understood vulnerability is grave news.
But do we tear it out by its roots? Isolate it? No. Artificial intelligence is too important for that -- particularly, ironically enough, in cybersecurity defense. We have no choice but to confront the Trojan horse gambit and block it.

