
6 techy ways to entice new talent during The Great Resignation
If you've been paying attention to the news lately, you know that many people are choosing to leave their jobs for various reasons. This period is being coined as "The Great Resignation."
Employers across all sectors are looking for new ways to gain the attention of potential employees -- but it'll take more than just posting a couple of positions on online job boards. Some recruiters are even turning to artificial intelligence (AI) to improve their recruiting processes and make them more efficient.

Ransomware remains a threat 30 years on
As our lives have become increasingly dependent on technology, virtually all personal and business data is kept on internet-connected platforms and in today’s digitized world this has become a gold mine for cyber criminals. In fact, we have seen cyberattacks grow exponentially in the last 12 months and in particular ransomware attacks increased by more than 485 percent in 2020.
Yet ransomware is nothing new. It is astounding to think that this attack technique has been around since 1989, when the first version was created by the "Father of Ransomware" Dr Joseph L. Popp. Disseminated via mailed floppy disks, the program demanded a hefty ransom of $189 to free victims’ data. Fast forward 30 years and still today whenever an organization thinks it has ransomware under control, another attack more sophisticated and effective than the last emerges.

The gaming industry's latest challenge: DDoS protection
Like moths to a flame, hackers always go where the action is. As the COVID-19 pandemic drove work away from the office, businesses have faced one cyberattack after another on their remote work infrastructure. Meanwhile, a boom in virtual entertainment has brought a surge of players to the gaming industry -- and with them, a rise in DDoS attack activity.
Cybercrime rings are launching triple extortion campaigns combining DDoS attacks with ransomware, and data theft, while ordinary gamers can rent a botnet easily and affordably to cheat or disrupt competition with a DDoS attack of their own. The highly popular Titanfall 2 game has already been rendered virtually unplayable -- perhaps by as few as one or two individual players -- and seemingly abandoned by its publisher, which is now focusing on defending a newer title from similar attacks.

Five signs your technology is enabling your business
We live in a world that's driven by technology. It has seeped into every part of our lives and the corporate realm is no exception. In fact, during the peak of the pandemic, the quick adoption of innovative technology helped many organizations survive. However, entities must invest in the right technology that will enable strategic, operational and cost impact. There are both quantifiable and intangible benefits in choosing the right technology stack for a company.
The right tech helps to facilitate a workplace that attracts and retains talent, increases employee engagement, lowers operational costs, raises revenues and even boosts organizational stability. And while technological solutions can have a tremendous impact on a company’s ability to meet its business objectives, they need to be deployed intelligently to address specific problems or pain points.

IObit releases Malware Fighter 9 with improved performance and protection
The internet remains a dangerous place to inhabit; if anything, the risks presented by viruses and other forms of malware are greater than ever. While Windows includes the Defender tool to help keep you safe, it does not offer complete protection, and this is where the newly updated IObit Malware Fighter 9.0 can help you out.
This latest version features full support for Windows 11 and an expanded protection database. IObit, however, points out that this is not just a case of "blindly increasing" the size of the database, but also optimizing it by tidying up invalid and out-of-date entries.

Double or bust? Cost management versus cloud innovation
Holiday season is upon us, and predictions are that online sales will hit an all-time high of $206.88 billion in the run up to Christmas. The growth in online demand has meant e-commerce operators, banks and logistics companies are increasingly reliant on cloud strategies and investments to rapidly scale, and remain resilient and secure. In retail, the cloud market is predicted to expand over 18 percent CAGR by 2025 driven by omnichannel experiences while the cloud supply chain management market is set to grow at a CAGR of 13.81 percent.
While retail is a cloud leader, other industries are following suit, and as such, we’re starting to see the trends influencing adoption. The recent 2021 Cloud Adoption Survey, explores the state of the cloud, microservices, distributed application development, and other critical infrastructure and operations technologies.

The weaponization of Information Technology raises the stakes for cybersecurity
As pressure grows on governments worldwide to take decisive legislative action to protect vital networks, data and infrastructure, there is a growing acceptance that despite its vital role, regulation alone cannot address the challenges posed by nation-state and criminal cyberattacks.
The pressure to act has been growing. Among the devastating attacks mounted on public sector IT infrastructure in countries around the world, the now infamous SolarWinds incident arguably did more than any other to push politicians into action. While both the US and UK governments blamed Russia’s Foreign Intelligence Service (the SVR) for the supply chain attack, the Russian government refuted the claims in an exchange of rhetoric reminiscent of the Cold War.
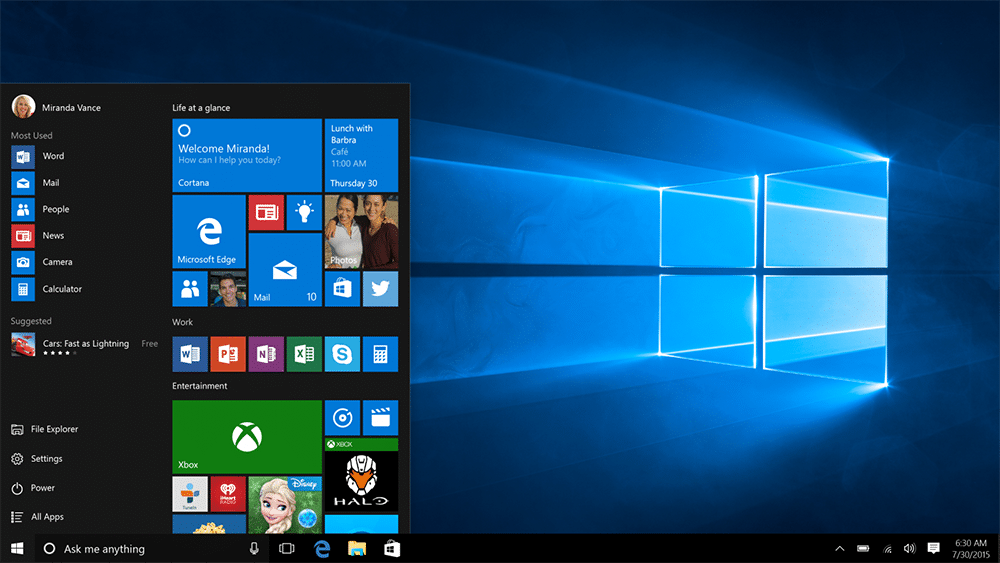
Download Windows 10 November 2021 Update (21H2) NOW! Includes great new pro features and a security boost
Microsoft has released the latest feature update for Windows 10, the November 2021 Update. Also known as Windows 10 21H2, this update boosts security with the addition of support for the WPA3 H2E (Hash-to-Element) protocol and more.
As is often the case with feature updates like this, Microsoft is performing a staged rollout meaning that if you wait for it to be offered to you, you might be waiting quite a while. You can, however, opt to manually download and install the November 2021 Update so you have the latest version of Windows 10 installed as soon as possible. Read on to find out what's new and how you can skip the queue and upgrade immediately.

Vaccination mandates, productivity uncertainty and how to operationalize eligibility
Due to the ongoing COVID-19 pandemic and the demand for employees to return to the workplace, the United States Department of Labor is acting on an executive order from the Biden administration which requires all companies with more than 100 employees to issue vaccination passports or agree to frequent COVID testing, as a part of their day-to-day business activities.
There is a workforce divide as to how vaccine mandates will be implemented across managers and employees. As it stands, and according to a recent study, only 30 percent of executives feel that their businesses should implement some level of vaccine mandate. This may be mainly down to anti-vaccination sentiment, which has caused issues throughout the economy and its workforce.
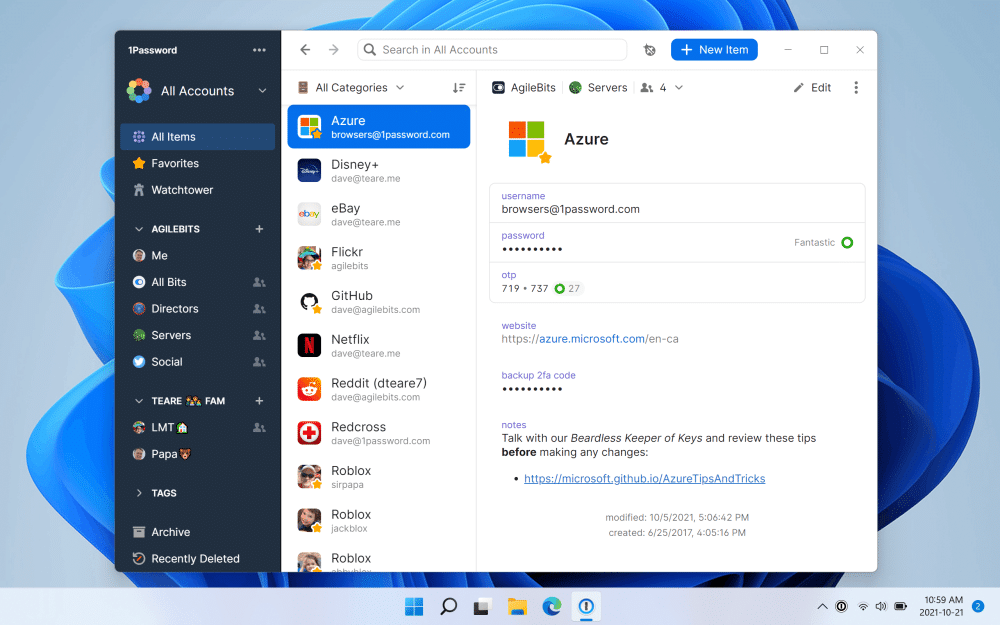
1Password 8 for Windows sports complete ground-up rewrite and new look
Toronto developer AgileBits has unveiled 1Password 8 for Windows, a complete rewrite of the program code with the promise of a "modern, first-class experience that feels right at home on Windows 11".
The new build has been developed using the lightweight Rust programming language using the Electron cross-platform desktop framework to facilitate future development across multiple platforms.

Why a career in cybersecurity is more exciting than you might think
Back in 2019, I wrote an article about the talent shortfall in technology and cybersecurity. Unfortunately, since the pandemic and because of Brexit, that gap, particularly here in the UK, has only widened. As of 2021, the global talent shortage already amounts to40 million skilled workers worldwide. By 2030, the global talent shortage is predicted to reach 85.2 million workers.
This means that companies worldwide risk losing $8.4 trillion in revenue because of the lack of skilled talent. This gap is keenly felt in security and again there is currently a shortage of 350,000+ cybersecurity specialists in Europe alone.

Hybrid working: What does it mean for IT?
It’s almost impossible to escape the phrase "hybrid working" at present. The pandemic has brought about changes to the office environment and the way we work that few would have predicted a few years ago. In fact, remote and hybrid working models now look to be a permanent fixture, given the success that many businesses have seen in recent months.
Debate over the pros and cons of this change has dominated the media landscape, and there are undoubtedly challenges that come with this kind of transition. Offices that used to home hundreds of employees every day now lay either empty or with just a skeleton staff, creating a drain on resources and prompting plans to downsize office space.

77 percent of the UK employees experience this work-related syndrome
You may read the phrase "imposter syndrome" and be surprised that there’s a term for something you feel without realizing it’s a common thing. Have you ever felt like you’re not good enough for the career you have? Do you doubt yourself and feel like an imposter in the workplace? Do you have a nagging feeling that you’re winging it? You’re not alone.
A huge 77 percent of the UK experiences imposter syndrome.

How old, incomplete, and inaccurate data can hurt businesses
Across the board, from operations to finances to customer satisfaction, the wrong data -- old, incomplete, and inaccurate information -- sets business back. According to MIT, "The cost of bad data is an astonishing 15 percent to 25 percent of revenue for most companies."
The differences between these errant data are important. Also important is understanding that, strictly speaking, there is no "bad data." "Bad" makes data subject to the interpretation of a value judgment. A better, more descriptive term would be "technical debt." This is when engineers begin to indiscriminately start to modify code and introduce new features. Over time, features are layered one on top of another and, if unchecked, teams sacrifice long-term efficiency via a durable, hard-won solution for the sake of easier, short-term approaches that yield a quick solution.

How businesses can combat the challenges of cloud adoption
In recent years, cloud computing has become ubiquitous. So much so, that individuals rarely notice that they are using it to store documents and data instantly, despite the increasing importance that these technologies have in the remote arena. As many organizations continue to see their workforce scattered across different cities and countries, there is a clear urgency to access data safely, and without needing to do so in a physical workplace.
Beyond pandemic-incentivized cloud usage, other businesses will be motivated by the ease and flexibility that these technologies allow -- indeed, many find the ability to scale their operations up or down a very attractive prospect indeed.

