
How multi-cloud application delivery is impacting ecommerce providers as they prepare for major growth
Ecommerce continues to be one of the most fast-paced and competitive global industries, with industry-watchers estimating that online sales will constitute a fifth of all retail sales worldwide by the end of 2022. As vendors strive to capture their share of market growth, they need to offer exceptional customer experiences that build loyalty and repeat revenue. However, delivering omnichannel excellence puts considerable pressure on infrastructure as site traffic increases and consumer expectations rise.
At the same time, the sector is heavily targeted by cybercriminals seeking to disrupt, extort and damage online retail businesses. Consequently, striking a balance between operational efficiency, cost-control, security and customer satisfaction is a complex challenge.

Why VPNs make remote access less secure and what to do about it
Virtual private networks (VPNs) were introduced roughly a quarter of a century ago. The premise at the time was solid: Create an encrypted tunnel from a computer to a network so remote users could have secure access to company resources and communications. Although they were slow and time consuming for IT to administer, VPNs gained traction because they met the primary objective -- the connections were secure...or at least secure enough.
Today, it’s a different story. Where VPNs were uncommon 20 years ago, now they’re ubiquitous. But they were never intended to handle the scale of a massive remote migration, and the weaknesses are showing. Last spring, a report from Digital Shadows on Q1 vulnerability activity had cyber criminals targeting VPNs more than most other attack avenues to get into enterprise networks. Even prior to COVID-19, the National Security Agency (NSA) released a Cybersecurity Advisory about "malicious cyber actors leveraging VPN vulnerabilities."

Moving towards a seamless connectivity between fixed and mobile networks
Remote and hybrid working are key themes that businesses have had to shift their attitudes towards over the past 18 months. As part of this transition, many have embraced cloud-based technologies to enable their teams to continue working from home. But even after the country continues to recover from the after effects of the pandemic , businesses will still need to plan for the future and look more closely at how to meet the needs of their employees.
Flexibility is important for organizations who are still looking to keep their businesses running from anywhere -- whether that’s the traditional office, home office, or a mixture of both. If you look more closely at this new hybrid model of work, everybody needs a mobile device. It’s not something that you can really get away and with this fact in mind, it’s important that businesses recognize the infrastructure and investment required to enable a workforce that can work anytime, anywhere. So how can you securely implement reliable mobile communications for the long term?

The overpromise of technology
Last month on Twitter, tech writer Casey Newton posted the above pic, observing that he sees it all over San Francisco. "This ad is all over SF and I can’t decide what I dislike more: the wild overpromising or the total lack of information about what it does," he said.
I’ve noticed the same ad but it didn’t register as much with me as it did with Casey because these messages have finally exhausted me. It’s because the constant overpromise of technology has been going on for years. From a well-founded and ongoing skepticism about what AI actually is and can be, to the ill-founded hype that touches almost anything tech-related these days, both the perception and reality of technology need an adjustment.
IObit Advanced SystemCare 15 is here to clean and optimize Windows 11
There is a lot to think about when it comes to maintaining the performance of your computer -- so much so that it can become an all-consuming task. If you would rather spend your time using and enjoying your PC, you should delegate the job of optimization and cleanup to a third party. And this is precisely where IObit Advanced SystemCare 15 can help you out.
The latest version of this incredible free collection of utilities adds support for Windows 11, but this release is about more than just working with the latest version of Microsoft's operating system, There is an improved cleanup component that can tidy up after a larger number of applications than ever before. There is also smart AI that not only makes the software faster and more efficient than ever, but also means that it is incredibly easy to jump into and start using straight away.

Why improved digital solutions sit at the heart of a successful office
The pandemic has changed a lot for businesses, whether that’s their customers’ buying behavior or product demands.
One of the biggest challenges for many businesses was the shift to home working. In March 2020, companies who hadn’t already implemented dedicated digital solutions scrabbled to adapt. Digital transformation was accelerated -- McKinsey found that businesses sped up their digitization by three to four years.

Can vaccine passports ensure a safe return to school?
With no true end to the COVID-19 pandemic in sight, there are growing concerns from parents, teachers, and dignitaries alike about how schools can operate safely as the new school year gets into full flow. As vaccination rates increase across the board, educational institutions nationwide are determining whether or not to make it mandatory for students to be vaccinated upon re-entry.
Vaccine passports have become a hot topic of discussion. They are valid pieces of documentation that prove that you have been vaccinated against COVID-19 and other infections. They can be physical copies, such as a paper card. Or, more conveniently, vaccine passports are digital, available through phone apps and other technological means. Some universities and colleges have required that these passports be shown, while several apps have been developed to show these passports. As health officials express concern about COVID spread and variants make their presence felt, can vaccine passports assure students a safe return to school this year?

How firewalls have improved and become part of zero trust cyber defense
The zero-trust model is an enigmatic animal. Sometimes you think you already know and understand it, but you may end up realizing there’s still a lot to learn. This quandary can be exemplified by the use of firewalls to protect an organization’s networks and IT resources.
Traditional firewall software has already ceased to be useful in putting up meaningful security for organizations. The same goes for legacy firewall appliances. However, firewalls have evolved to provide more features and functions that address present-day threats. As network security specialist Ruvi Kitov suggests, "firewalls are not going anywhere." They just evolve and add new features to address new needs.

4 tips for creating a DevOps implementation strategy
By its very design, DevOps is a disruptive technology -- but one that can profoundly and positively impact how businesses manage and deliver software projects. As one of the most complex technologies to implement, DevOps includes multiple phases critical to achieving successful digital transformation. But, when it’s managed correctly, DevOps is the most powerful tool available in modern software development.
With proper guidance, organizations that take the leap and deploy DevOps will become adept with its unique structure and realize its ability to create and deliver results at the speed modern business demands. While there are no shortcuts to implementing DevOps, general recommendations to apply will benefit any business considering its implementation.

Adobe Photoshop Elements 2022 and Adobe Premiere Elements 2022 are unleashed
Adobe has long been a name associated with creativity, but it is also a company whose products are most generally thought of as being professional, with a level of complexity and price tags to match. With its Elements range, however, Adobe brings the essential components of its flagship products to a wider market in easier-to-use, more affordable tools.
Now the company has launched the 2022 editions of the range, furnishing each with important and powerful new features that will enable you to take your creativity to the next level. For photo editing and image-based creations, there is Adobe Photoshop Elements 2022; for video-based work there is Adobe Premiere Elements 2022.

Workforce optimization in a new world of worker mobility
A recent BBC article highlighted the tidal surge of workers looking for new jobs in the post-pandemic world. Dubbed "The Great Resignation", the data paints a startling picture of people "leaving the workforce or switching jobs in droves". A similar survey by Microsoft of more than 30,000 workers showed 41 percent were considering quitting or changing professions within twelve months. Meanwhile yet another study of British and Irish employees showed 38 percent planning to quit in the next six months to a year.
These alarming figures could make any employer break into a sweat, unless they were in the recruitment business. However, in sectors that struggle with high staff turnover even in normal times, the projected increase in labour mobility presents an existential threat. In the contact center industry, for example, where employee turnover is usually around 26 percent annually -- significantly higher than the national average of 10-15 percent -- mapping on the new churn multiplier might even mean total workforce loss.
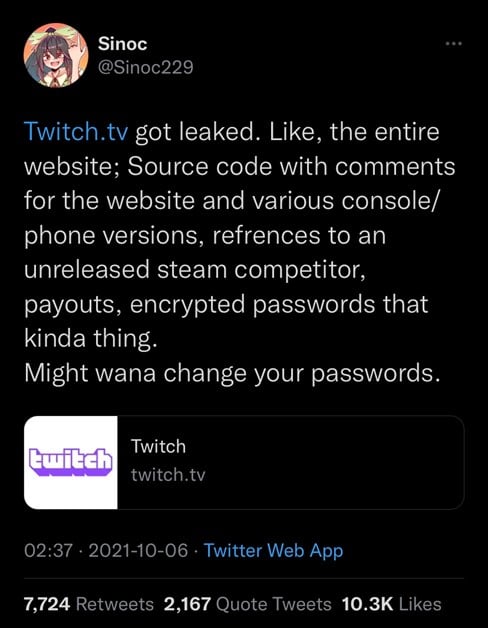
The week of tech outages and leaks
History will treat Monday and Tuesday as days the tech world would love to forget.
Monday was Black Monday for those who rely on Facebook, Instagram, and WhatsApp. All of these Facebook-owned properties went down for around eight hours, leaving a lot of people confused and services such as Twitter booming with the extra traffic. This was a critical outage that even affected Facebook employees and their internal systems, making it impossible for many people at Facebook to use anything they needed to get their jobs done.

Fake lies matter: Brand impersonation attacks
While a great deal of news articles, white papers, and security solutions are focused on 0-days and vulnerabilities, the core vulnerability of all of our information technology is people. Our entire tech stack makes it easy for users to make mistakes because the fundamental problem is that there is no good way to authenticate anyone or anything online. In 1993, a comic in the New Yorker famously said, "On the Internet, nobody knows you’re a dog", and not much has changed in 28 years.
One of the key ways attackers get an initial foothold into organizations is by tricking users to compromise themselves, often using brand impersonation. A recent study stated that there were 88 instances where malicious mobile apps attempted to impersonate TikTok. The reason, people share TikTok videos, it’s immensely popular, and it has a trusted brand-name, so people feel safe.

How businesses can keep colleagues and customers close
While the past 18 months or so have focused on providing business continuity in the midst of a crisis, the next year is set to bring another shift. As organizations around the world gear up to return the office -- at least in a hybrid capacity -- businesses need to make a seminal decision: should they go back to old ways of working? Or can firms take this opportunity to fundamentally review their practices and reduce the inevitable complications that have arisen throughout the pandemic?
Given that firms have experienced some teething problems implementing new approaches, I would urge organizations to take the latter course. In a world where workplace communication between customers and colleagues is becoming increasingly frayed, now is the perfect time for businesses to rethink whether their chosen solutions fit their needs.

Hybrid working is here to stay
The Covid-19 pandemic has meant that for the last 18 months or so, workers across the UK and Europe who previously worked in offices were compelled to work from home instead.
This huge shift to remote working was unprecedented in its speed and scale. It was made possible by technology such as high-speed broadband at home: mobile phones: video conferencing: and online fax services, which together reproduced the capabilities of being in the office.

