
Data privacy in a wearables world
Data is precious -- that much is obvious. For wearable tech and the quantified self in particular, digital brands and hardware vendors are increasingly conscious of the huge opportunity that this data provides them. It gives them greater insight into the lives, behaviors and tastes of consumers than ever before. But as we learned in Spiderman, "with great power comes great responsibility" -- although a responsibility that I feel many organizationals are not taking seriously enough. Google is currently in the British high court accused of bypassing security settings to track the online browsing of Apple's Safari users and target them with personalized adverts. Facebook's privacy policy is being investigated by Dutch regulators for similar reasons. The company has come under fire before for using consumer data without making consent processes explicit and transparent enough, and its constant updates to its privacy policies are creating an incomprehensible puzzle which many consumers struggle to solve.
With this in mind, I've listed five steps I think hardware vendors and brands should take to prevent wearables becoming an unquantifiable nightmare:

New SDK aims to make protecting mobile apps easier
Illinois-based Zebra Technologies Corporation acquired Motorola Solutions' Enterprise business in late 2014 and is now announcing one of the first fruits of that link up.
Enterprise app development platform RhoMobile -- part of the MSE acquisition -- is launching a new independent software vendor (ISV)-targeted SDK through Digital Defence. Its aim is to make the task of protecting mobile applications more developer-friendly.

New brainstorming tool helps translate ideas into action
Task management tools tend to be good at collating lots of information, but translating that into action and turning ideas into reality is another matter.
German software company MeisterLabs is launching a new visual task completion tool called MeisterTask to help teams manage projects and bring ideas to life.

Anonymous wants humanity to go into outer space and 'explore other worlds'
Hacktivist collective Anonymous is mostly famous for launching attacks on the Church of Scientology, ISIS, world governments, child pornography websites and, er, Kanye West. But its latest mission is to unite humanity and get us working together to go into space and colonize new worlds. No, seriously.
I suspect someone at Anonymous may have enjoyed Christopher Nolan’s Interstellar a little too much.

MeshMagic 3D is a simple STL viewer and editor
Australian developer NCH Software has announced the release of MeshMagic 3D, a simple 3D design tool which can import and edit STL and 3DP models.
This is very much "CAD lite". The 335KB setup file doesn’t download the real files from somewhere else, it really is all you get: a single executable plus an installer, and nothing else at all.

Amnesty calls for ban on mass surveillance
Amnesty is taking legal action against the US and UK governments, challenging “the lawfulness of their indiscriminate mass surveillance programs”.
The human rights campaigning group will head to the European Court of Human Rights in Strasbourg on Friday because, it says, "every legal avenue in the UK has been exhausted".

Despite what you may have heard, Internet Explorer is not dead
You shouldn't believe everything you read online -- no, really, you shouldn't. Just the other day we heard from John Gruber who made the baseless suggestion that Apple invented USB-C (hint: it didn't). Now it's the turn of Tom Warren from the Verge. Yesterday he wrote an article with the headline "Microsoft is killing off the Internet Explorer brand". Gosh!
He goes on to talk about Project Spartan (the new default web browser in Windows 10 that we learned about weeks ago) but also immediately contradicts himself in a sub-heading: "IE will live on...". Hang on... I thought it was being killed off? There then followed confusion, back-pedalling, and playing with semantics from Warren that did nothing to clarify the matter and served to rile many on Twitter.

5 smart devices that will kickstart the Internet of Things this year
The Internet of Things is expected to make big waves this year, with the number of connected devices predicted to increase massively.
Although IoT products have yet to make major in-roads within the consumer market, there are a few concepts being released later this year that could help kickstart the IoT boom.

Xiaomi testing Windows 10 for phones -- could Microsoft use the company for flagship?
Microsoft confirms today that Windows 10 -- its forthcoming operating system for desktop, mobile, Xbox, and IoT platforms -- will be releasing this Summer in 190 countries and 111 languages. On a blog post, the Windows Phone-maker also announces that it has entered into a partnership with Xiaomi, China's top smartphone vendor to test Windows 10 for phones, suggesting that the two companies are working to make a flagship-level smartphone.
Microsoft notes that the company is testing Windows 10 with select Xiaomi Mi 4 power users. The Mi 4 is XIaomi's current flagship smartphone, which runs Android. "Through a new program with Xiaomi, one of the top smartphone distributors in the world, a select group of Xiaomi Mi 4 power users will be invited to help test Windows 10 and contribute to its future release later this year", the company notes on a blog post. "These power users will have the opportunity to download the Windows 10 Technical Preview – installing it and providing their feedback to Microsoft".

Microsoft reveals a worldwide Windows 10 summer release
They say that when buying property, location is everything. This is very true, because a beautiful home in a terrible location is hardly a smart investment. In other words, the true value is the community and neighborhood, not the number of bedrooms.
The same can sort of be said regarding product releases too; instead of location, however, timing is everything. This is especially true in the technology world, as there are key months that make more sense for new computers or operating systems to be released. Ideally, you want to release prior to two key moments -- back to school and holiday shopping. With that said, Microsoft casually announces today that Windows 10 will be released this summer.
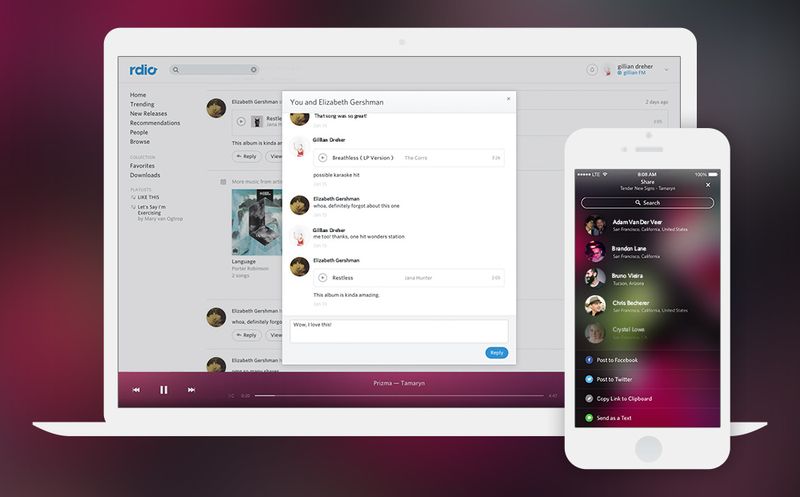
Rdio uses SXSW to announce new sharing features
In the crowded space that is today's streaming music market, Rdio is one of the names that pops out. Combine that with the current Austin, Texas festival known as SXSW and you have a match -- technology and music meet each year the party. This year is no different, as announcements are coming out from various services in attendance.
Rdio is one of those companies revealing information at the big show. The latest update brings new features to the streaming service, all centered around community -- as in sharing with your circle of friends.

Electronic payments coming to Facebook Messenger
Facebook is introducing support for sending and receiving money through Messenger. Starting in the US in the next few months, users of the social network will be able to make electronic payments free of charge. While this is not a service that will rival the likes of Apple Pay or PayPal, it provides a way to quickly send money to a friend.
This is not a payment system that has been completely built from the ground up. It's based on the same backbone that's used to process payments for gamers and advertisers. Security is understandably of paramount importance, and Facebook stresses that as well as encryption and PIN protection for all, iOS users will also be able to take advantage of Touch ID.

Twitter empowers victims to report abuse to the police -- put bullies behind bars
The Internet can be a marvelous place. Not only is it chock full of information, but it tears down boundaries, enabling people to communicate with each other from all parts of the world. Unfortunately, the sometimes anonymous nature of the web can bring out the worst in people. On social media, many people are bullied, harassed and even worse -- threatened with violence, including rape or murder. Heck, some people have even committed suicide as a result of the abuse. Often times, the attacker's actions goes so far as to break the law.
Today, Twitter is taking a stand against online bullies that commit crimes through threats and intimidation. Instead of just reporting the abuse to Twitter, users now have a tool to help report the crimes to law enforcement. By simply clicking a button, users can start the process of putting some online bullies behind bars.

Microsoft Azure moves to the Internet of Things with new suite for businesses
The Internet of Things (IoT) are three words that can both terrify and fascinate. On the one hand you have the Jetsons-style modern future, but on the other a darker side filled hacks to products in your home. Microsoft's latest move isn't heading into your home, at least yet. Instead it aims to harness the power of Azure to aid the business world in this new frontier.
Microsoft shoots to "better connect people, processes and assets, and better harness data" with this new offering. The company claims it will allow businesses to more easily monitor digital assets, thereby bring a host of benefits along with it.

Google starts vetting Android apps and implements age rating system
For a long time now Google Play has been home to just about any sort of app imaginable. Apps covering every subject under the sun are available, with quality ranging from atrocious to incredible. To help sort the wheat from the chaff, Google has announced two important changes to the way apps appear in the store.
Apps that are submitted to Goole Play are now subject to a review process, and an age rating system is being introduced to help indicate the target audience for apps. Google says this will help to weed out "violations of our developer policies earlier in the app lifecycle".