Microsoft patches Windows 8.x but leaves Windows 7 vulnerable, according to researchers
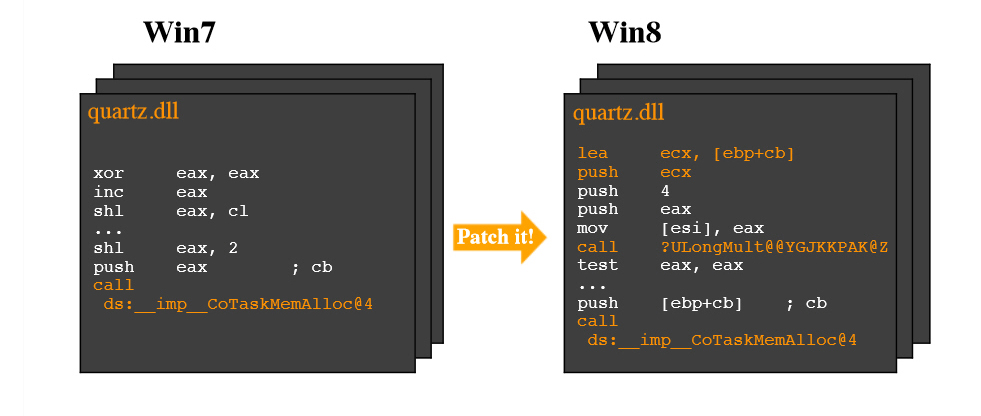
Around 50 percent of PC users are on Windows 7, while just 12 percent are running Windows 8.x, yet Microsoft is leaving the more popular OS vulnerable to zero day attacks by choosing to only patch the newest Windows version. That’s the findings of two security researchers who built a tool to compare 900 libraries in Windows 8 with their Windows 7 counterparts.
"If Microsoft added a safe function in Windows 8, why does it not exist in Windows 7? The answer is simple, it’s money -- Microsoft does not want to waste development time on older operating systems. They want people to move to higher operating systems," security researcher Moti Joseph claimed in a presentation at the Troopers14 conference in Heidelberg, Germany.
The DiffRay tool, developed by Joseph and malware analyst Marion Marschalek, compares libraries in the two operating systems and logs any patches found in one but not the other. In a demonstration, embedded below, they found four security functions which were updated in Windows 8 but not Windows 7.
Marschalek said it was "pretty simple, really scary simple" to develop the comparison tool, and warned that hackers, or governments, could use this technique to find and exploit missing patches in Windows 7.
Although the Troopers14 presentation happened last month, The Register only uncovered it a few days ago.
We reached out to Microsoft for comment on the allegations, and a spokesman told us: "We follow an extensive process to develop security updates for all supported devices and services, involving a thorough investigation, update development, and testing for compatibility among other operating systems and applications. We are continually working to improve our products and we encourage researchers to coordinate vulnerability disclosure with Microsoft in order to help protect customers".