How hackers can infiltrate a network and remain undiscovered

In 2014 we saw many data breaches which were often due to a direct attack on a company’s network in which human error played a part.
Big data security specialist Exabeam has produced an infographic showing how hackers can penetrate a network and remain difficult to spot.
It points out that 76 percent of breaches involved stolen user credentials. Using stolen identities hackers can penetrate a system and will then look to elevate their access privileges to allow them access to sensitive information.
Because they're using valid credentials these attacks often remain below the radar. This allows hackers to remain on the system for a long time, 200 days according to some sources.
Exabeam uses SIEM (Security Information and Event Management) technology to digitally monitor user behavior, and take human error out of the equation.
You can view the full infographic below.
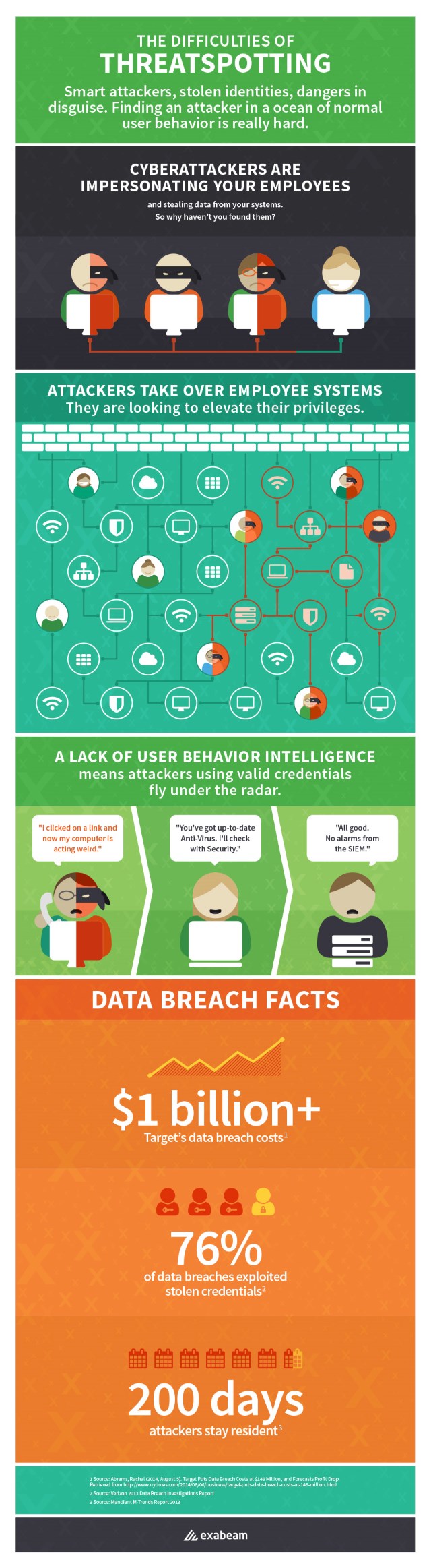
Photo credit: Adchariyaphoto/Shutterstock