'Mumblehard' malware turns thousands of Linux servers into spam botnet -- ESET shuts it down

Linux-based operating systems are rock solid -- reliable and secure -- but not infallible. The Mumblehard malware, for instance, targets servers running the open source kernel, installing a backdoor, and then turning them into part of a powerful spam-focused botnet. Surprisingly, Mumblehard was rather widespread, infecting 4,000 Linux-powered servers.
Of course, had administrators patched the systems appropriately, there is a good chance that some of them would have avoided infection. I say this, because ESET found that some machines were infected through known exploits, in things like WordPress. Thankfully, ESET successfully terminated the botnet on February 29th, 2016 by taking control of the home IP.
"ESET researchers observed a reaction from the operators of the botnet about a month after we published our paper. In our report we mentioned how we had registered a domain name acting as a C&C server for the backdoor component in order to estimate the botnet size and distribution. The malware authors apparently responded by removing the unnecessary domains and IP addresses from the list of C&C servers included in the malware and keeping only the one that was under their control", says ESET.
The security company further says, "with only one IP address acting as the C&C server for the Mumblehard backdoor and no fallback mechanism, a takeover of that IP address would suffice to stop the malicious activities of this botnet. We decided to take action and contacted the relevant authorities to make things happen".
ESET did not act alone, but rather as a collaboration with both the Cyber Police of Ukraine and a company called CyS Centrum LLC. By taking control of the IP address to which the infected machines would connect, they were able to effectively terminate the botnet. It also allowed them to analyze the data being sent using a "sinkhole".
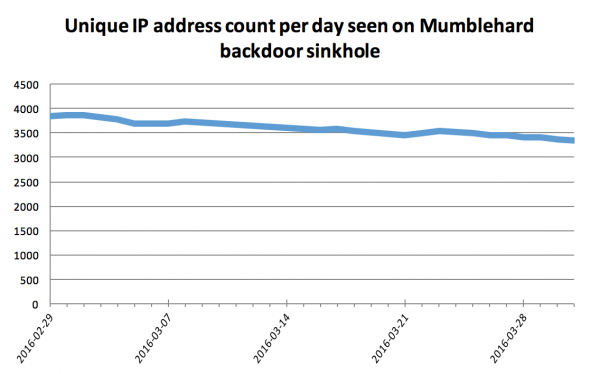
Slowly but surely, fewer machines are pinging the server as they are probably being patched. With that said, other machines are still infected -- the infection is just benign. In theory, if the criminals were to somehow magically regain control of the IP address -- not likely to happen -- the evil could resume.
If you have a fear that your servers are impacted, you should look into cleaning it ASAP. ESET shares the following GitHub landing to learn more about detection here.
Photo credit: Gunnar Assmy / Shutterstock
