Social networking behind the corporate firewall increases 500%, creates big vulnerabilities
Enterprise security and firewall company Palo Alto Networks on Wednesday released the results of an eight-month study of more than 1,200 organizations and 2 million users that observed more than 28 exabytes of data passing through corporate networks. Among the results of the study, Palo Alto found that applications using SSL (secure sockets layer) in some way represented 23% of all corporate bandwidth, and dynamic/port hopping applications represented a further 16% of all bandwidth.
In total, social networking within the corporate firewall has increased 500% in one year's time.
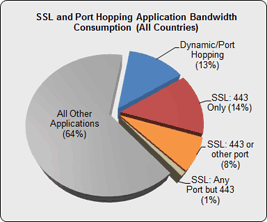
The reason this is important is because Palo Alto highlights this as a huge vulnerability, since most SSL-encoded traffic is invisible to corporate IT, and it is a potential vector for serious security breaches.
The problem is that many of the most popular sites and services on the Web today are using SSL, including not only e-mail, p2p, and web commerce services, but social networking sites like Facebook, Linkedin, and Twitter, and the use of these sites in enterprise settings is only increasing.
Most firewalls and intrusion prevention systems offer zero visibility into SSL traffic. So in short, a huge chunk of corporate bandwidth is being consumed by sites to which IT admins have no access to behind the corporate firewall.
This problem is compounded because social media has taken an ever larger role in the marketing, public relations and customer service aspects of business, and many companies cannot afford to simply block these sites from use on the corporate network.
Just one year ago, the bulk of enterprise Facebook use could be attributed mostly to non-work related activity (i.e. employees goofing off.) But according to "The State of Corporate Social Media in 2011" from usefulsocialmedia.com, customer service, employee engagement, and product development will each increase their use of social media more than 50% by the end of this year.
"The pain is that the vulnerability is all in one port. If you want to allow Twitter and Facebook in a read-only mode, but you're a bank, you can't have people talking over Gmail, you can't have an unaudited communication channel that could potentially be used to conduct trades over," said Chris King Palo Alto Networks' director of marketing. "Yet Twitter, Facebook, Gmail, all those things, all come over port 443. So do you turn that port off or leave it open? Oh, by the way, your outsourced CRM --whether it's Salesforce or something else-- goes over the same port."
King says that when all this traffic is coming through one port, and your only control is to turn on and off ports, then you effectively have no control. "A lot of the trusted and collaborative type applications --especially the more image-conscious ones-- are going with SSL to prevent their users' sessions from being hijacked by something like FireSheep. And there's an aura of security that you get when that little lock closes. Is it secure? Well, it's encrypted. But it's an encrypted channel from which threats can flow."
Palo Alto's Application Usage and Risk Report (May 2011) is available for download here.