New malware uses Android smartphones to mine for digital currencies
 Digital currencies can be purchased in their respective markets, or acquired through "mining", which can be done using any computer or smartphone and a special piece of software. Security firm Lookout has just released details on a new piece of malware called CoinKrypt that uses a botnet of Android smartphones to mine for currency.
Digital currencies can be purchased in their respective markets, or acquired through "mining", which can be done using any computer or smartphone and a special piece of software. Security firm Lookout has just released details on a new piece of malware called CoinKrypt that uses a botnet of Android smartphones to mine for currency.
Because mining is incredibly resource-intensive, the process can severely run down a phone’s battery, eat through a data plan by periodically downloading what is known as a block chain, or a copy of the currency transaction history, and potentially damage hardware by causing it to overheat and burn out.
Lookout says CoinKrypt is about as basic as they come, comprising of just three small program sections or classes embedded in the target app, that kick off the mining process. However this simplicity is part of the problem, as the malware drives the hardware to mine relentlessly until the phone runs out of battery or overheats.
CoinKrypt is currently targeting the likes of Litecoin, Dogecoin, and Casinocoin, but not -- yet anyway -- the much more popular Bitcoin. This is down to the difficulty rate of mining the best known of the digital currencies. It is almost one million times easier to mine Litecoin than Bitcoin, and over 3.5 million times easier to mine Dogecoin.
Marc Rogers, Principal Security Researcher at Lookout, explains: "In order to control the rate at which new digital coins are minted, the software that runs the currency sets a difficulty rate which governs just how much processing power you need to expend in order to solve the blockchain and get new coins. The difficulty for Bitcoin is so tough right now that a recent mining experiment using 600 quadcore servers was only able to generate 0.4 bit coins".
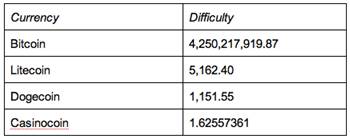
Mining for digital currency on a smartphone is hugely inefficient. "When we tested the feasibility of mining using a Nexus 4 by using Android mining software such as the application AndLTC, we were only able to attain a rate of about 8Kh/s -- or 8,000 hash calculations per second, the standard unit of measure for mining. Using a Litecoin calculator and the above difficulty setting we can see that this would net us 0.01 LTC after seven days non-stop mining. That’s almost 20 cents".
So far CoinKrypt has only been found in Spanish forums dedicated to the distribution of pirated software, and while mining as a strategy hasn’t paid off for these malware authors yet, Lookout is convinced that the number of new malware families targeting digital currencies will continue to grow, as authors experiment with new, and more efficient ways of using smartphone botnets to mine for digital cash.