Vulnerable mobile apps are not being patched -- millions of people at risk

Vulnerabilities in software are a fact of life; only a fool would say any code or method is perfect. The moment you fall into that trap of dangerous thinking, you have let your guard down.
So while vulnerabilities will happen, and must be accepted, how the developer responds to the flaw is the true test and measure of its security. In other words, if a vulnerability should always be expected, so too should a prompt patch to fix it. Sadly, McAfee Labs finds in a new study that this is not the case. Many insecure and vulnerable apps are found to not be patched, months after the flaw-discovery. Yes, months.
"In January, McAfee Labs tested the 25 most popular apps on CERT's list of vulnerable mobile apps that send login credentials through insecure connections and found that 18 still have not been patched despite public disclosure, vendor notification, and, in some cases, multiple version updates addressing concerns other than security. McAfee Labs researchers simulated man-in-the-middle (MITM) attacks that successfully intercepted information shared during supposedly secure SSL sessions. The vulnerable data included usernames and passwords and in some instances, login credentials from social networks and other third party services", says McAfee Labs.
The Intel-owned company further explains, "although there is no evidence that these mobile apps have been exploited, the cumulative number of downloads for these apps ranges into the hundreds of millions. Given these numbers, McAfee Labs’ findings suggest that the choice by mobile app developers to not patch the SSL vulnerabilities has potentially put millions of users at risk of becoming targets of MITM attacks".
The shocking thing is that these apps are not abandoned; they are popular and being regularly updated by the developer for other things, while the security flaws are being ignored. This shows a priority being put on features, rather than safety. Sadly, the users of the apps probably have no idea.
McAfee Labs has not revealed the names of these apps, and rightfully so; it doesn't make sense to bring the apps to the attention of people with malicious intent.
With that said, McAfee explains further, "the most downloaded vulnerable app in this group is a mobile photo editor with between 100 million and 500 million downloads. The app allows users to share photos on several social networks and cloud services. In late January, McAfee Labs tested the most current version of the app downloaded from Google Play using CERT Tapioca; we were able to intercept the app's username and password credentials entered to log into the cloud service to share and publish photos".
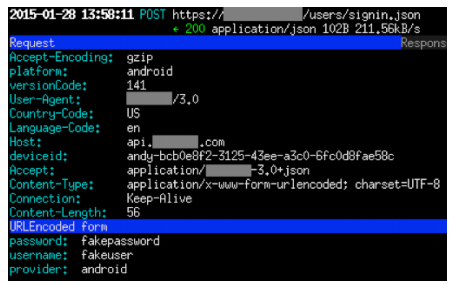
Yikes. McAfee Labs has been able to intercept login credentials for Facebook, Microsoft OneDrive, and more. The worst part is, these are apparently very popular and seemingly-reputable releases, so recommending the avoidance of "shady" apps does not help to protect here.
You can read more of the scary details in the report found here.
Photo Credit: faysal / Shutterstock