Microsoft stops you from using weak passwords

Having a good password can make the difference between your account being hacked and receiving a notification informing you of a failed login attempt. Even though this should be common knowledge, it seems that many folks are in the dark about this. You do not need to look hard to find evidence of this, as there are many reports that reveal passwords like "1234567890" to be very popular still.
Since it is clear that it cannot rely on its users to make the right decisions about their account security, Microsoft is taking a proactive approach by "dynamically banning commonly used passwords". So, if you think that "qwerty123" is good enough to keep all your emails private, luckily you will not have to find out whether you are right or not.
"When it comes to big breach lists, cybercriminals and the Azure AD Identity Protection team have something in common -- we both analyze the passwords that are being used most commonly. Bad guys use this data to inform their attacks -- whether building a rainbow table or trying to brute force accounts by trying popular passwords against them. What *we* do with the data is prevent you from having a password anywhere near the current attack list, so those attacks won’t work", says Microsoft's Azure AD Identity Protection group program manager Alex Weinert.
So, whenever there is a new data leak, Microsoft will analyze the passwords in the attack to make sure that you do not set one of those up to protect your account. This security feature is live for Microsoft Account, which gives you access to your Outlook.com, Office 365 and Xbox Live, and in private preview for Azure ActiveDirectory. Microsoft says that it will roll it out across all 10 million+ tenants of its cloud platform's directory and identity management service.
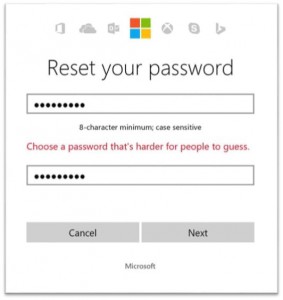 The way this security feature works for a Microsoft Account is by letting you know that you should "choose a password that's harder for people to guess". Microsoft has shown it in action during a password reset, but, as Weinert has explained in a previous blog post, it also kicks in when a compromised password is detected. When that happens, Microsoft locks down the account and protects it "before the bad guy can ever use the credentials".
The way this security feature works for a Microsoft Account is by letting you know that you should "choose a password that's harder for people to guess". Microsoft has shown it in action during a password reset, but, as Weinert has explained in a previous blog post, it also kicks in when a compromised password is detected. When that happens, Microsoft locks down the account and protects it "before the bad guy can ever use the credentials".
So, how does that work? Well, Microsoft says that when it detects a "bad guy" trying to guess your password it will lock them out. This only happens to that login session, so if you try to login from your PC you should have no issues accessing your account. The only time you will get locked out too is when the bad guy is using your actual device to gain access to your account.
Apparently, 54 percent of the time that this protection, referred to as "Smart Password Lockout", kicks in is when someone from "anomalous environments" tries to guess your password.
Given the fact that the Microsoft Account is an integral part of the user experience in Windows 10, Microsoft recommends that IT administrators enforce strong passwords at corporate level or embrace Windows Passport, which is a two-factor authentication solution designed for Windows 10 and Windows 10 Mobile.
But, as my colleague Wayne Williams noted and I noticed as well, the benefits of enforcing a strong password can be easily outweighed by an easy-to-guess PIN. As you know, Windows 10 lets you protect your PC with a four-digit PIN, but the combinations that are allowed do not seem to be subject to the same scrutiny your Microsoft Account password is.
Wayne and I have been able to set up rather simple PINs on Windows 10 machines, and I assume many of you have as well. So, perhaps, Microsoft should work on that front too, as it is far too easy for users to basically expose their devices.
Microsoft has provided a guide to creating strong passwords, and you can read it here. It is aimed at both IT admins and users.
Photo Credit: AlexandreNunes/Shutterstock