Enterprise SIEMs fall short on detecting attacks

Enterprise Security Information and Event Management (SIEM) tools are detecting fewer than five of the top 14 MITRE ATT&CK techniques employed by adversaries in the wild, according to a new report.
Analysis by AI-powered detection engineering company CardinalOps also shows SIEMs are missing detections for 80 percent of the complete list of 190+ ATT&CK techniques.
Among other gaps in detection coverage the report finds that 15 percent of SIEM rules are broken and will never fire, primarily due to fields that are not extracted correctly or log sources that are not sending the required data.
In addition 75 percent of organizations that forward identity logs such as Active Directory and Okta to their SIEM, do not use them -- which is concerning because identity monitoring is one of the most critical data sources for strengthening zero trust. Also 75 percent of out-of-the-box detection content provided by SIEM vendors is disabled due to noisiness and customization challenges experienced by detection engineering teams.
These gaps in detection are put down to an ever changing threat landscape, increasing complexity and difficulty in recruiting skilled staff. Many enterprises are still relying on manual and error-prone processes for developing new detections, which makes it difficult for engineering teams to reduce their backlogs.
"Our goal with creating this report was not to shame security teams for having blind spots, but rather to draw management-level attention to the disparity between perceived security and actual detection quality and coverage, using MITRE ATT&CK as the benchmark," says Michael Mumcuoglu, CEO and co-founder at CardinalOps. "If we're spending all this time and money on more security tools, why are we still being hacked? We believe the answer lies in the need to apply automation and analytics to identify and fix misconfigurations in existing tools, as well as remediate the riskiest detection gaps, in order to free detection engineers to focus on more strategic activities such as investigating new and novel attack scenarios."
You can get the full report from the CardinalOps site and there's an infographic summary below.

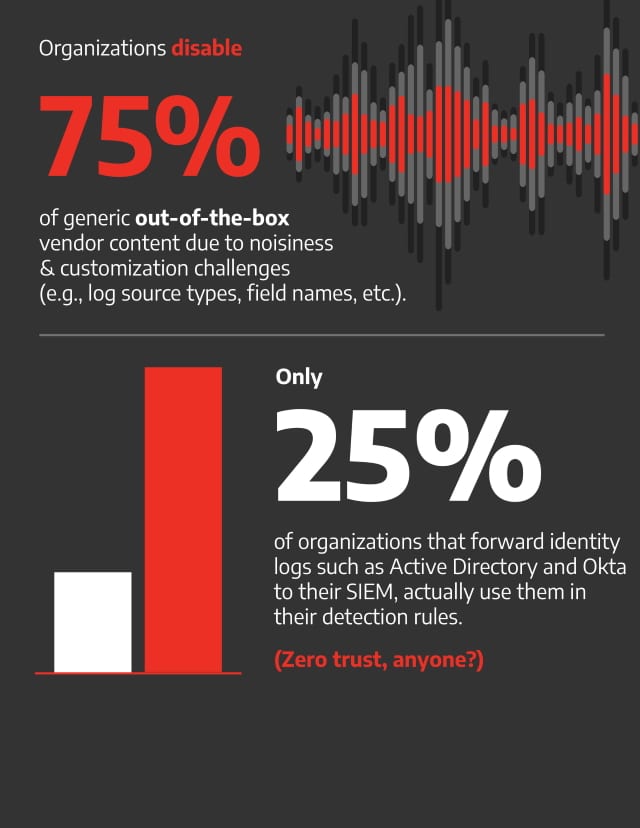
Image Credit: Jurgen Priewe / Shutterstock