Impersonation attacks leverage Silicon Valley Bank collapse in new phishing campaign

As news of Silicon Valley Bank’s (SVB) collapse continues to dominate the headlines, cybercriminals are running phishing campaigns impersonating SVB and other financial institutions, including M-F-A and Bloomberg.
Responding quickly to the 24-hour news cycle, cybercriminals aim to leverage their victims’ potential distress over their financial situation to make them more susceptible to this type of attack.
Quick attack summary
Vector and type: Email phishing
Techniques: Brand impersonation; social engineering
Payloads: Malicious hyperlinks to steal personal information, with embedded tracking to provide the attacker with additional insights, including which IP addresses accessed the phishing website; and attachments to steal financial details used for wire fraud
Targets: Organizations in North America and the UK
Platform: Microsoft 365
Bypassed secure email gateway: Yes
The phishing emails use highly stylized html templates, as well as plaintext emails, sent from spoofed, lookalike email domains. The payloads include hyperlinks to phishing websites that steal victims’ personal data and attachments used to collect financial details for wire fraud.
SVB phishing emails: impersonation and wire fraud attacks
The attacks we’ve seen impersonating SVB were created by copying and editing the standard SVB html that is used in their legitimate emails. This includes a high-resolution rendering of the SVB logo, use of brand colors, and inclusion of the original SVB footer with its legitimate London, UK, address. This increases the credibility of the attack, making it more likely the victim will be deceived.
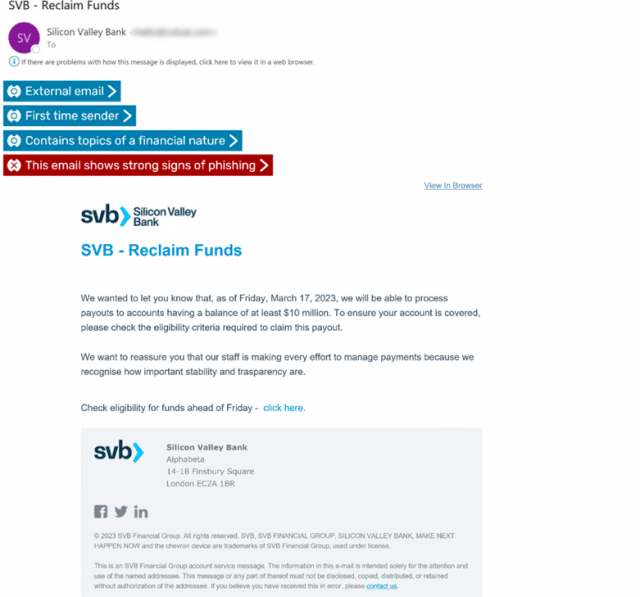
Some initial concerns for SVB customers focused on the $250,000 protection limit for each cash deposit account offered by the Federal Deposit Insurance Corporation. The phishing email below shows the cybercriminal leveraging this information by offering the victim access to their money significantly beyond the original limit -- up to $10m.
As well as manipulating victims using the concerns about accessing their funds, the cybercriminal also uses a deadline of 'Friday March 17, 2023' to increase pressure on the victims. A frequent social engineering tactic, this is designed to force people to 'think fast', making them less likely to check what they’re doing is safe.
The 'From' address impersonates the UK arm of SVB: 'svbuk.com'. At the time of writing, our researchers believe this to be a lookalike domain, rather than one owned by the legitimate SVB, as it fails technical authentication.
When a user clicks on the link in the email, they are taken to a phishing website that impersonates SVB.
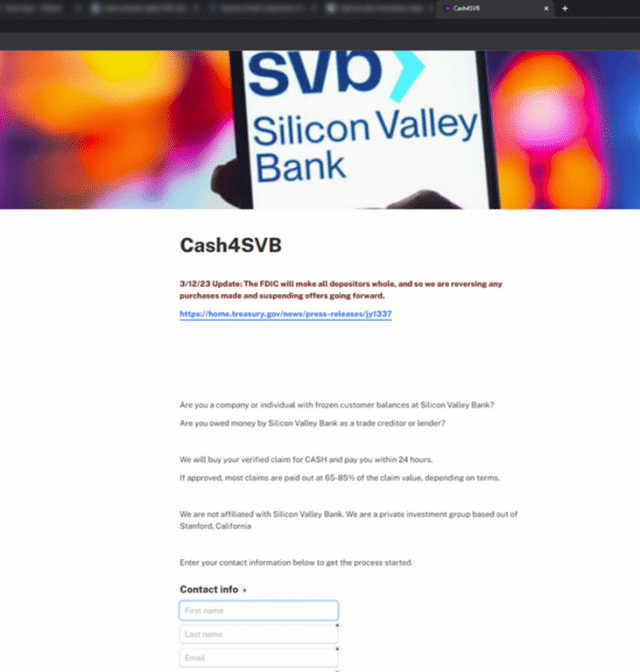
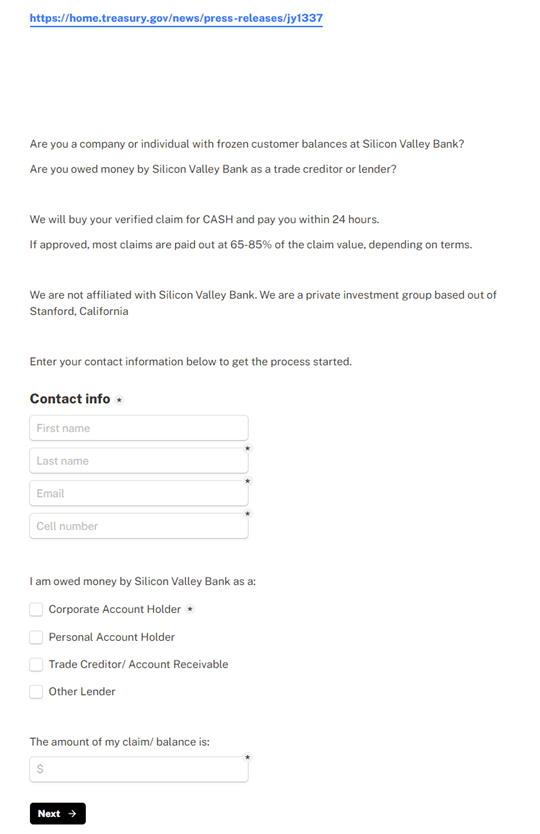
The phishing link payload routes the victim to a website domain created on March 10, 2023, (the same day as the SVB collapse) called 'cash4svb', which claims to collect information from the recipient to see if their account is eligible for the increased pay out.
At this point, the attack becomes potentially less convincing. Our researchers noted that the lookalike website has some obvious cosmetic issues and doesn’t compare favorably to the legitimate website. However, using a domain containing 'svb' and the banner image including SVB at the top of the page, the cybercriminal anticipates that anxiety and desperation will drive the victim to populate the fields.
Additionally, the cybercriminal makes the claim on the phishing website that it belongs to 'a private investment group based out of Stanford, California'. This claim could work in two ways: (1) explaining why the website doesn’t closely align to SVB branding and (2) increasing confidence the money will be paid despite SVB’s turmoil.
Our researchers expect these details could be used by the cybercriminal to continue their attacks directly on SVB (by completing the form, the victims are creating an SVB customer list for the attacker) or the information could be sold on the dark web for use in future attacks.
Bloomberg phishing emails: impersonation leading to wire fraud
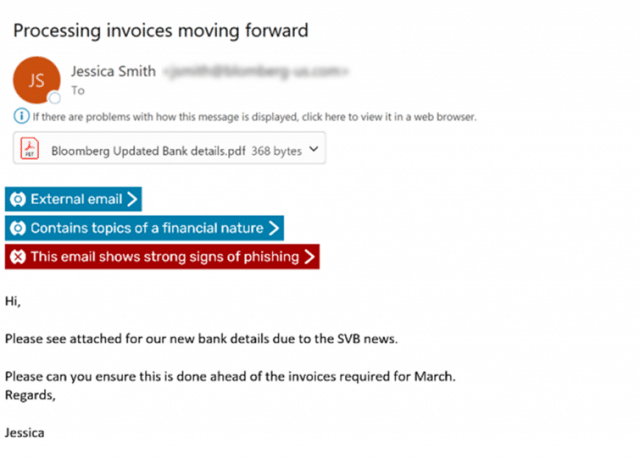
In addition to attacks impersonating SVB, Egress Defend has also detected discreet social engineering attacks that inform victims that the sender’s organization is changing bank accounts and financial details need updating.
In the example below, the cybercriminal uses a spoofed, lookalike domain to impersonate Bloomberg ('@blomberg-us.com). The phishing email uses the SVB news as a plausible excuse for why bank details need to be changed. The .pdf attachment supports the claim via the file name 'Bloomberg Updated Bank details'.
Similar to the SVB impersonation email, this attack also uses a deadline (‘ahead of the invoices required for March’) to socially engineer the victim into reacting quickly to avoid ramifications.
The attachment contains alternative bank details, which if a company uses, will result in wire fraud.
Domains we’re seeing these emails sent from
As noted, the emails are being sent from spoofed, lookalike domains that impersonate legitimate organizations. Some of the domains our researchers have seen are:
- svb.com
- svbUK.com
- svb.uk
- blomberg.com
Links we’re seeing as the payload in these phishing emails
Here are some of the spoofed, lookalike malicious hyperlinks that are part of the SVB impersonation attacks:
- https://cash4svb[.]com/
- http://svbreclaim[.]io/
- https://svb-payment[.]com/
- https://svbhelp[.]com/
As mentioned above, some of the attacks use attachment-based payload for wire fraud.
Egress analysis
These attacks demonstrate how cybercriminals weaponize the 24-hour news cycle. When organizations or topics trend in the news, it is now almost inevitable to see a wave of phishing campaigns in response. The phishing website analyzed above was created on March 10, 2023, the same day as the SVB collapse, demonstrating the speed with which cybercriminals create and execute phishing campaigns that leverage trending news.
In this campaign, cybercriminals leverage victims’ heightened anxiety about financial security and access to their funds, as well as take advantage of wider disruption with changes to bank details and payment processes.
The phishing emails contain social engineering tactics to increase their credibility and lower the victims’ suspicions, such as the use of the legitimate SVB email template and spoofed domains. Additionally, the sense of urgency created through arbitrary deadlines pushes people to react instinctively, with less time for rational thought or double checking the situation with someone else. People will be in a heightened state of anxiety already, and these tactics manipulate them further to increase the likelihood that they make a mistake and fall victim to the attack.
The information scraped by the phishing website in the SVB impersonation attacks could present cybercriminals with a curated list of SVB customers, as it’s likely only affected companies and individuals would respond. This information could be used to retarget the victims and their organizations in other related attacks or used in other SVB campaigns, including by other cybercriminals who could purchase the list if it’s put up for sale on the dark web.
Finally, the wire fraud attacks could result in a quick payday for cybercriminals, with at least March invoices being paid into their accounts as victims try to be responsive to the changing situation with their suppliers.
Advice for staying safe from these phishing attacks
As with any trending news story, people need to be made aware the SVB collapse is being used by cybercriminals and should be advised to treat any update with caution, including verifying messages via another means (e.g. visiting the correct website via a search engine or saved browser link, rather than clicking on a phishing email).
Organizations should also enable multi-factor authentication as a layer of defense to protect themselves from account takeover attacks.
We also recommend that organizations invest in advanced phishing detection solutions, such as Egress Defend, that deliver intelligent detection capabilities for advanced phishing attacks and real-time teachable moments to improve security awareness and training to help people identify the actual threats that are targeting them.
Image credit: rarrarorro/depositphotos.com
Jack Chapman is VP of Threat Intelligence, Egress.