Are VPNs Still Trustworthy in 2025? Why NordVPN Stands Apart

The “VPN is the best tool for online security” era seems to be officially over.
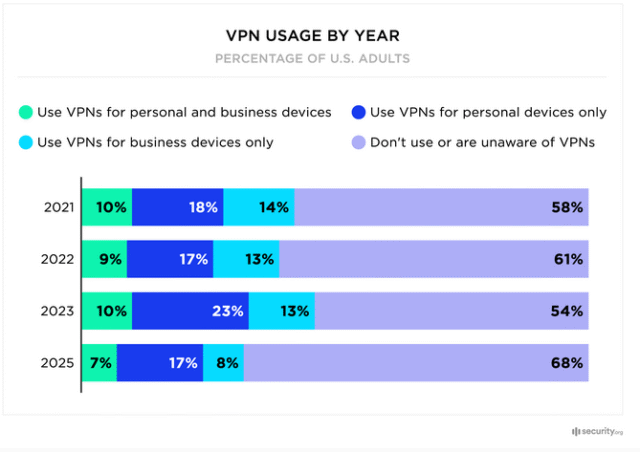
According to security.org’s 2025 study, VPN usage has fallen from 46% in 2023 to only 32% in 2025. This percentage has never been lower in the past five years.
What’s even more alarming is that 65% of enterprises are actively planning to abandon their VPN services entirely, while 81% are rushing toward zero-trust security frameworks by 2026.
This isn't just a trend. It's a mass evacuation. And for good reason.
VPNs haven't just failed to evolve with modern threats. They've become the attack vectors themselves. Seeing this, cybersecurity experts, companies, and individual users are running away from VPNs like there’s no tomorrow.
Yet, one provider stands out as the most preferred VPN provider in the U.S. because it's not just patching old problems, but building entirely new defenses.
In this guide, we’ll examine exactly why VPNs have lost the confidence of security experts, and which brand is now the exception in this scenario.
Why VPNs Have Become a Security Liability
Let's begin by looking at exactly why security experts are losing trust in VPNs and what makes them so dangerous today.
1. VPNs Are Now Prime Targets for Cybercriminals
As of 2025, 72% of cybersecurity leaders are openly concerned about VPN security risks. Reflecting this, 94% of organizations acknowledge that the VPN they use can be very attractive to cyberattacks.
Yes, these are all thoughts of industry leaders. But what about the facts? Well, they prove industry leaders right. In 2024, 58% of all ransomware attacks happened through VPNs.
What’s mouth-watering about VPNs to cyber criminals is that VPNs concentrate user traffic through centralized gateways. They have to, that’s how they work. And it's exactly what modern attackers want, because only one compromised node grants them access to thousands of users. Let us explain what we mean:
Most people use their VPNs to stay safe while using a shared network like a public WiFi, and in 2024, cybercriminals discovered a vulnerability in this use case and exploited it. The problem is called the “DHCP Option 121” exploit.
This vulnerability lets attackers manipulate routing instructions delivered by the Dynamic Host Configuration Protocol (DHCP). Essentially, they can silently re-route a VPN user’s traffic through a malicious server, even while the VPN is active. Yes. You read that right. Using a VPN can sometimes make the hackers’ jobs easier.
Your VPN Provider Knows Everything You Do
Here's an uncomfortable truth:
By design, your VPN provider has complete visibility into your online life.
A VPN can have a no-logs policy (honestly, it’s the least they should do), and can prove it through multiple audits. But this doesn’t account for all your data.
A provider in a country with invasive surveillance laws can be legally forced to log and hand over your data. This has happened multiple times in the past.
Even if a VPN truly keeps no logs of your browsing, it still collects metadata. And metadata (connection times, bandwidth usage, IP addresses) tells a story that can be combined with other data sources to identify you. In the era of AI-driven threat intelligence, metadata can be as revealing as raw browsing history.
Yesterday's Technology Can't Handle Today's Threats
Most VPNs are running on technology from the early 2000s. While cyber threats have evolved dramatically, VPN architecture has barely changed.
Many VPN providers still offer PPTP and L2TP/IPSec protocols, despite knowing they're fundamentally broken. PPTP can be cracked in under a day with basic equipment. And even if your VPN’s encryption holds, it can’t protect you against modern tracking techniques.
Browser fingerprinting, device-level identifiers, and app telemetry bypass the tunnel entirely. Your VPN may hide your IP, but it won’t stop your shopping app from leaking your exact location to an ad network.
Then there’s quantum computing, which is no longer a sci-fi buzzword. By the early 2030s, experts expect quantum attacks to break much of today’s public-key cryptography. How do you think your VPN’s early 2000s tech will protect you then?
The Internet Has Evolved Beyond VPNs
In addition to being weak against modern attacks, another downside of using technology from the early 2000s is that VPNs are now irrelevant. Back then, most web traffic was unencrypted, and hiding your IP address provided real privacy.
Today, over 90% of all web traffic is encrypted via HTTPS. Moreover, most browsers include DNS-over-HTTPS by default, encrypting the very lookups that VPNs claim to protect. Your ISP can't see which sites you're visiting anymore anyway, with or without a VPN.
Data shows that users who are “very” or “extremely” familiar with VPNs don’t just stick to VPNs. They’re more likely to layer multiple privacy tools, like Tor browsers or encrypted DNS, into their security stack.
When You Actually Need a VPN (And When You Don't)
Despite all these vulnerabilities, VPNs aren't completely useless. There are specific situations where they still provide value:
- Accessing geo-restricted content: Streaming services, sports broadcasts, or websites that are only available in certain countries.
- Public WiFi in high-risk countries: Airports, hotels, or cafés in regions with active cybercrime or government surveillance. Not perfect protection, but better than broadcasting your activities directly to potentially hostile networks.
- Corporate remote access: Many companies still rely on VPNs to connect employees to internal tools or networks.
- Journalists and activists in oppressive regimes: If you're facing targeted surveillance or censorship, a VPN is one tool in your arsenal.
- Bypassing ISP throttling: When your internet provider deliberately slows down specific services, a VPN can sometimes mask the traffic type.
How NordVPN Addresses Every VPN Vulnerability
As of 2025, 17% of all VPN users in the U.S. are using NordVPN. This makes Nord the most preferred VPN provider by far (closest competition is Proton with 9%).
Now, let’s dive deeper into why Nord VPN stands apart from its competitors against all these drawbacks of VPNs.
GET NORD: THE BEST VPN IN 2025 TRUSTED BY THE MAJORITY
Defeating Network-Level Attacks
First of all, NordVPN has a different approach to network-level threats. First of all, Nord’s WireGuard-based NordLynx protocol encrypts all traffic at the kernel level and assigns ephemeral, server-side IP addresses that never expose the user’s real routing table to the local network.
NordLynx also uses a double NAT (Network Address Translation) system to make attacks like DHCP Option 121 less likely. The NAT makes sure that no fixed identifier is ever tied to a user’s real IP address.
In addition, NordVPN applies network segmentation and isolation. This limits the blast radius of any breach: even if an attacker somehow compromised a single server, it wouldn’t give them carte blanche access to the entire network.
Combined with their kill-switch, Nord actually can combat the new-age attacks malicious actors are directing to VPNs.
The Trust Equation: Verified No-Logs and RAM-Only Servers
NordVPN knows that the biggest barrier to trusting a VPN is the fact that, by design, it could see everything you do. Their answer is to remove the ability to store anything in the first place.
It is a given that Nord has a solid no-logs policy. It has been audited by PwC and Deloitte multiple times. But we know these audits don’t mean much in case of a hack. So, to further tighten the security, Nord turned all its servers to run as RAM-only, because they can’t store data once powered off (literally, by technical capability, they can not).
When it comes to having to comply with lawmakers' requests for data, Nord doesn’t care, because it is based in Panama. The country has no mandatory data retention laws and no membership in intelligence-sharing alliances like Five Eyes or Fourteen Eyes.
Future-Proof Security Architecture
At the protocol level for today’s weaknesses, NordVPN’s NordLynx replaces outdated and vulnerable options like PPTP and L2TP/IPSec. Based on WireGuard, NordLynx offers leaner code for easier auditing, faster performance, and stronger encryption without the known weaknesses of legacy protocols.
This proactive approach is backed by a public bug bounty program, which rewards independent researchers for finding flaws. In addition to creating hundreds of checkpoints by skillful professionals, this initiative also turns potential attackers into collaborators.
GET NORD AND SECURE YOUR DATA TODAY AND TOMORROW
Beyond Basic VPN Protection
NordVPN also knows that modern tracking happens at the browser app, and even device level, therefore unstoppable by just simply hiding IP. That’s why they’ve built additional layers that go far beyond the basic tunnel:
- Threat protection pro: This feature blocks malicious websites, intrusive trackers, and ads before they ever reach your device. This not only prevents malware downloads but also cuts off a major source of browser fingerprinting and behavioral tracking.
- Dark web monitor: Continuously scans dark web marketplaces for leaked credentials linked to your email address. If your data shows up, you’re alerted immediately, giving you a chance to change passwords before criminals can use them.
- Meshnet: Creates encrypted, direct connections between devices anywhere in the world. This lets you securely share files, play LAN-style games, or access your home devices remotely without exposing them to the public internet.
Nord Pricing
Despite being the best VPN on the market, Nord remains affordable. Its Basic plan starts at around $3.09 per month when billed over two years. That gets you fast, secure access for up to ten devices and includes features like Threat Protection.
Stepping up to Plus or Complete adds deeper cybersecurity tools (like threat protection pro, a password manager, and encrypted cloud storage) for only a couple of dollars more per month.
GET NORD AND SECURE YOUR CONNECTION NOW
Your Next Move in the VPN Trust Crisis
The VPN industry has a trust problem. But not every provider is the same. While many have been patching holes in a sinking ship, NordVPN has been rebuilding the vessel entirely: modern protocols, RAM-only servers, post-quantum encryption, and tools that address threats far beyond the tunnel.
If you still have situations where a VPN makes sense, choose one that’s prepared for today’s and tomorrow’s risks. The security landscape isn’t going to get friendlier, and neither should your defenses!
FAQs
Is any VPN truly trustworthy anymore?
Trust depends on proof, not promises. A reliable VPN should have independent audits, transparent policies, and technical safeguards like RAM-only servers to ensure no sensitive vpn data and vpn information can be stored.
Should businesses abandon VPNs entirely?
Not always, but most organizations are moving toward zero-trust security and cloud-native access tools. That’s the current direction in vpn news, as companies look to replace legacy systems that create single points of failure.
What's the difference between consumer and enterprise VPNs?
Consumer VPNs focus on privacy and bypassing geo-blocks. Enterprise VPNs are built for secure corporate access, but they can still face the same weaknesses, which is why even big companies are reconsidering their role.
Can NordVPN protect against quantum computing attacks?
Yes. Nord is one of the few providers already rolling out post-quantum encryption, preparing for the time when quantum systems could break today’s cryptography. This is a key feature for anyone looking for a safe VPN that won’t become obsolete.
