
Purism 'PureOS Store' will be for both desktop and mobile apps, and that's a mistake
Purism is a company that focuses on privacy, security, and open source ideology. What's not to love? It already manufactures Linux-powered laptops with cool features like hardware kill switches for webcam and wireless radios. This way, you can be confident that your hardware is less likely be hacked and used to spy on you.
The company's core values are noble and respectable, but financially, this won't necessarily signal success. In fact, competing with the likes of Microsoft, Google, and Apple for desktop computing is a very hard task. Even harder? Breaking into the mobile business which is dominated by iOS and Android. And yet, Purism plans to launch the Librem 5 smartphone (running Linux-based PureOS) at some point in the future. Of course, such a device will need an app store, so PureOS has finally revealed the name of its upcoming offering -- the unimaginatively named PureOS Store. Sadly, this will be an attempt to merge mobile and desktop into a single store.

How to export your saved passwords from Google Chrome
From social media sites to online stores, from forum accounts to financial institutions -- there are now so many websites that require the use of a username and password, it's little wonder than so many of us turn to some form of password manager to save them.
If you use Google's Chrome browser, you have almost certainly saved numerous passwords so you don't have to manually enter them every time they are requested. You may have wondered how to export these passwords for the purposes of backing them up, or to import into another password manager. Here, we show you how.
Best Windows 10 apps this week
Three-hundred-and-eighteen in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Windows Store in the past seven days.
The October 2018 Update is finally being rolled out again; check out Wayne's blocking instructions if you don't want it installed on your devices right now.

Microsoft concedes that Cortana can't -- and won't -- compete with Alexa and Google Assistant
Microsoft has seemingly admitted defeat in the digital assistant wars, with CEO Satya Nadella saying he does not want to compete with Amazon's Alexa or Google Assistant.
Rather than planning a Cortana-powered smart speaker or other device, Nadella has demoted Cortana, signaling that Microsoft wants to focus on bringing it to other platforms as a "skill". He believes users should be able to use Alexa or Google Assistant to call on the capabilities of Cortana through close integration.

Emby Server 4 adds live TV guide data, boosts performance across the board
Anyone who’s got a load of digital media lying about needs a media server, and while the obvious solution is to install Kodi or Plex, you might be missing a trick.
Although it’s still overshadowed by its better-known rivals, Emby Server 4.0 has just been released for Windows, Mac and Linux, plus is now available for Nvidia Shield and Android devices too.

Windows 10 October 2018 Update finally starts its phased rollout -- here's how to block it
The Windows 10 October 2018 update, aka Windows 10 version 1809, aka the botched update that deleted user files, caused default app issues, broke Apple iCloud, Edge, and Windows Store apps, and introduced a bunch of other problems, is finally rolling out to all -- well most -- users.
The update was first released at the start of last October, but then pulled a few days later when the scale of its problems become noticed. It was re-released in November, with a bunch of new problems. Microsoft has been working to fix these, and last month made 1809 available to 'advanced users' -- that is users who know how to manually check for updates.

Enterprise IT continues to move to the cloud
Cloud adoption in enterprises is already very high and growth is likely to continue in 2019 according to the latest cloud adoption survey from NetEnrich.
The study of IT decision makers in businesses with 500 or more employees shows 85 percent of respondents report either moderate or extensive production use of cloud infrastructure, while 80 percent say their companies have moved at least a quarter of all their applications and workloads to the public cloud.

How to view Wi-Fi passwords in Windows
You have probably used your laptop in all sorts of places. As well as at home and in the office, you may well have used it in hotels, coffee shops and other locations that offer Wi-Fi access.
As such, you've almost certainly got a large number of Wi-Fi passwords saved on your computer, passwords that are seemingly inaccessible. But these saved passwords are accessible -- if you know where to look, that is. This is handy if you need the password to get your phone online, or another laptop. Here's how to recover saved Wi-Fi passwords.

Poor information management harms productivity
Poor information management processes are making jobs harder for staff and reducing their productivity and effectiveness in the workplace, according to new research from information management specialist M-Files Corporation.
Navigating different systems and locations to find the correct version of a file they are looking for negatively affects productivity according to 82 percent of respondents.

Huge Collection #1 database leak exposes 773 million email addresses and 21 million passwords
A massive database leak -- dubbed Collection #1 -- has made its way to hacking forums, exposing millions of email addresses and passwords. The news was first shared by Troy Hunt -- the man behind Have I Been Pwned? -- who explains that the leak comprises, "many different individual data breaches from literally thousands of different sources".
Hunt explains that there are "1,160,253,228 unique combinations of email addresses and passwords", so there are a very large number of people that may have been affected by the leak.
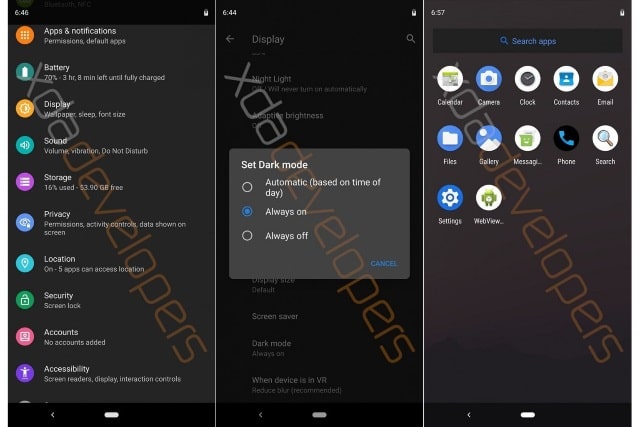
Android Q leak shows dark mode, improved privacy and intriguing Desktop Mode
The inclusion of a system-wide dark mode in Android Q is something that has been rumored for a little while now, and a new leak of the next version of Google's mobile operating system seems to confirm this.
A leaked build of Android Q not only features a customizable dark mode option, but it also shows that Google has tightened up permissions to help improve privacy. There are also exciting references to a Desktop Mode feature which would appear to be similar to Samsung DeX in making it possible to connect a phone to a monitor and use it like a desktop computer.

Get 'Advanced Penetration Testing -- Hacking the World's Most Secure Networks' ($26 value) FREE for a limited time
Typical penetration testing consists of low-level hackers attacking a system with a list of known vulnerabilities, and defenders preventing those hacks using an equally well-known list of defensive scans.
The professional hackers and nation states on the forefront of today's threats operate at a much more complex level -- and this book shows you how to defend your high security network, including:

Microsoft releases Windows 10 19H1 Build 18317, splits up Search and Cortana
New Windows 10 19H1 builds are coming thick and fast at the moment. With some builds the focus is just on fixing problems and making general improvements, but Insider Preview Build 18317 for Windows Insiders on the Fast ring is notable mainly because Search and Cortana are no longer linked.
Yes, that’s right -- instead of being part of the search bar, Cortana’s button now sits to the right of it.

deepin 15.9 Linux distribution is here with new multi-touch gestures and improved power management
Since Microsoft will be ending Windows 7 support in less than a year, many computer users will have to decide if they will move onto the much-maligned Windows 10. Alternatively, depending on their needs, they could opt for a Mac or Chromebook. But what if you are happy with your current computer and don't want to buy new hardware? In that case, Linux can save the day. The excellent Netrunner, for instance, is a great option for Windows switchers that fear a change of user interface.
If you are open to moving away from the traditional Windows-like interface, another superb Linux distribution to consider is deepin. If you aren't familiar, deepin is a very stable operating system that focuses heavily on appearance. Quite frankly, it puts Windows 10 to shame in that regard -- its "Deepin Desktop Environment" is far superior to the dated and boring interface found on Microsoft's latest operating system. Today, deepin 15.9 becomes available for download with a huge list of changes, including new multi-touch gestures and improved power management.

Compliance fears inhibit cloud adoption
According to a new survey, 88 percent of IT decision makers at mid- to large-sized companies think having to meet compliance standards in the cloud inhibits further cloud adoption within their company.
The study from Wakefield Research and Logicworks, finds that among senior management -- those most close to and responsible for cloud execution and performance -- the figure is even higher, with 97 percent agreeing that compliance inhibits cloud adoption.


