
MPAA chief Chris Dodd fights off allegations of bribery
Opponents of the Motion Picture Association of America are using the US Government's recently created "We The People" online petition service to force the Obama Administration to take a position on some controversial comments by former Conn. Senator-turned MPAA chief Chris Dodd to Fox News last Thursday.
By Tuesday afternoon, the petition had already passed the 25,000 person threshold to trigger a response from the White House. With over 27,500 signatures, it is gaining about 1,000 signatures an hour. Stop Online Privacy Act and PROTECT IP Act protesters are not satisfied with killing the bill alone: they want heads to roll.
NYU prof releases app to predict whether a company will fail
In 1968, NYU professor Edward Altman devised a statistical method for determining the financial health of a company called the Z-score formula for predicting bankruptcy, and since its publication, it has become a common statistical model used in loan evaluation.
Now a Director of Research in Credit and Debt Markets at the NYU Salomon Center for the Study of Financial Institutions, Dr. Altman has turned his formula into a hundred dollar mobile app for iPhone, iPad, Android and BlackBerry called "Altman Z-Score Plus."

Don't cry for me Las Vegas, Microsoft cancels MIX!
In December, Microsoft pulled out of the Consumer Electronics Show starting with next year's event. The rationale: Smaller, Microsoft events are more beneficial to everyone -- the company, attendees and customers for starters. Hey, that makes sense to me. So then, why is the software giant suddenly pulling one of its most-important developer events of the year? Without fanfare, or even a proper burial, MIX is over. Not just MIX 2012, but the entire event. Poof! Gone! Outta here!
Tim O’Brien, Developer & Platform Evangelism general manager, broke the news on the Official Microsoft Blog early this afternoon. Considering how hot and heavy Microsoft is about the Cloud right now and release this year of Internet Explorer 10 and Windows 8, timeing sure seems strange.

Microsoft says botnet chief was former antivirus vendor employee
Microsoft spent a good deal of time dismantling the Kelihos botnet last year, making it the first takedown where it was able to name actual defendants behind it. On Monday it made the suprising announcement that its latest defendant, Andrey N. Sabelnikov, had previously worked for an antivirus software vendor.
According to information on the Web, Sabelnikov worked for two Russian security vendors: Agnitum, a firm that produces firewall and antvirus software for PCs from September 2005 to November 2008, and Retunil from November 2008 to December 2011.

Got a Mac and non-Apple SSD? You need TRIM Enabler 2.0
Hot on the heels of a fifth Beta release last week, TRIM Enabler 2.0 has been given a final, stable release. TRIM Enabler 2.0, which extends TRIM support to non-Apple SSDs in OS X Lion, features a complete rewrite and new way of enabling TRIM by patching existing SSD drivers rather than replacing them.
Recent updates have also improved the speed of the patching process, plus TRIM Enabler now automatically updates when changes have been made instead of requiring a manual refresh. The final release has also introduced a new automatic update checker, allowing users to be prompted when a new version is released.
Opera 11.61 is released -- get it now!
The latest addition to the stable release channel for Opera is v11.61, which includes more than 50 security and stability enhancements and is recommended for all users. You can either wait for the automatic updater to occur, or you can force a manual check and update from the Help menu.
Two of the most important changes to the browser see a couple of on-going scripting problems being fixed, but there are also a large number of additional tweaks that address issues with various aspects of the program.
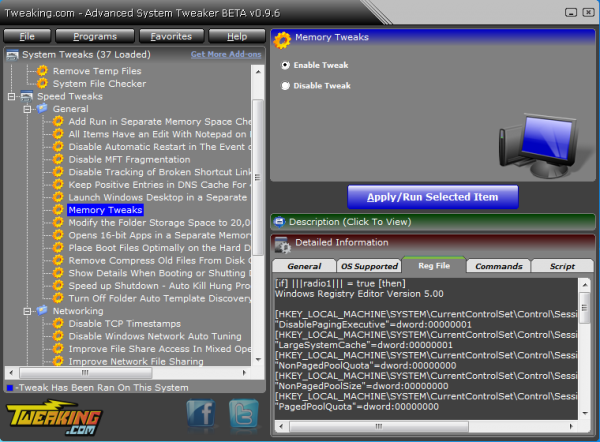
Fine tune Windows with Advanced System Tweaker
At first glance the Advanced System Tweaker looks much like many other Windows tweaking tools.
There’s the same familiar ideas, for instance, recommendations to disable this service or that, various networking and Explorer speedups. You get simple maintenance options, so you can perhaps clear your system temporary files at a click. And a Programs menu gives quick access to useful Windows applets, such as Device Manager and the Event Viewer.
CloudOn for iPad mini-review
The iPad has been touted as a replacement for the laptop, but if this is to happen a serious office suite is needed to allow everyday tasks such as word processing and number crunching to be carried out. In this area there are a number of mobile office suites to choose from, including Apple’s own iWork apps Pages, Keynote and Numbers as well as the likes of Documents To Go, Quickoffice and a few others.
While all of these are capable of producing and working with Microsoft Office compatible files, there is no getting away from the fact that none of them is Microsoft Office. This is something that CloudOn for iPad aims to address, bringing you fully functional versions of Word, Excel and PowerPoint to your tablet.

iPhone represents more than half of Verizon smartphone sales
This morning before the opening bell, Verizon Wireless announced fourth-quarter results. The carrier sold 7.7 million smartphones. Earlier this month, the nation's largest carrier disclosed 4.2 million iPhone activations during the same time period. Divide it up, and iPhone accounted for 54.5 percent of Verizon smartphone sales. (Update: Revised 4.3 million number released today puts it at 55.8 percent.) By comparison, Verizon sold 2.3 million 4G LTE devices, which includes mobile hotspots and tablets. At best, LTE devices accounted for 30 percent of smartphone sales. However, since that number includes other devices, iPhone outsold LTE smartphones by about 2 to 1.
In September I asked: "What if there is no iPhone 5 LTE?", before Apple announced 4S instead. Today, Verizon answered that question. As of Monday, the nation's largest 4G network reached 200 million in 195 US markets. Verizon currently offers 20 LTE devices, 10 of them smartphones -- 11, if counting 16GB and 32GB Droid Razrs. How much does LTE matter? Clearly not enough.

Get more from Windows Firewall with TinyWall
One common view of the Windows Vista/ 7 firewall is that it’s a toy, almost entirely useless, and you should replace it with something more capable just as soon as you possibly can. But this isn’t entirely fair.
Sure, there’s no easy way to, say, restrict outgoing network connections to the applications you specify, but that’s more to do with the firewall’s awkward configuration options than the underlying technology. And these are easy to fix. Install TinyWall and this compact tool will immediately extend the standard Windows Firewall, giving you far easier control over who gets to go online, and who really shouldn’t.

'This is our generation's Woodstock'
Samsung's newest "The Next Big Thing is Already Here" TV commercial is the riskiest, but by far the snarkiest for anyone closely following the marketing campaign. The jokes are all inside and require some familiarity with previous installments. The risk: Everyone else won't get it. The snark: The iPhone hipster putdowns are mean -- really mean.
During the very first commercial, one Apple hipster waiting in line for iPhone could never get a Samsung because he's "creative". The guy next to him snipes: "Dude, you're a barista". Both men are back in the new commercial, with the barista serving coffee to the snarky companion -- who is carrying Galaxy S II! He's done with the iPhone hipset and makes it known: "It's nice latte art, my man. I see you're still creative". He's with a woman who had the same Samsung smartphone during the first commercial in the series. The Barista: "You two look happy, with your phone".
Google+ names policy goes just far enough
There are lots of places where you can be anonymous online. Google+ isn't one of them. Late today, Google announced a revision to the G+ names policy that doesn't change this, but it does allow people to use nicknames and established pseudonyms. If anonymity is your thing, go somewhere else. I don't want you on Google+. You can bully pulpit somewhere else. As for those folks whose lives might be at risk for using real names, please be safe someplace else -- Facebook, Reddit, Twitter, Tumblr or WordPress, for example. Those services have proven they can protect your identity.
But, of course, the griping will continue from the Internet rabble determined to hide their identities everywhere. They want more from Google than just nicknames. What are you afraid of? I use my real name everywhere, as I have always done. I see that as being in the very spirit of the open -- and transparent -- Internet. Be who you are, not someone else. And if that comment --- or other online interaction -- requires you to hide your identity, shut the frak up. Vent somewhere else. For everyone else, and this includes people who have built up alternative identities, Google+ welcomes you.

AT&T, T-Mobile look to FCC to approve spectrum transfer
AT&T and T-Mobile filed a request with the Federal Communications Commission to gain approval for the transfer of spectrum, a stipulation agreed to as part of the breakup of the planned merger between the two companies. The value of the spectrum is about $1 billion, and is in addition to $3 billion in cash that AT&T will pay T-Mobile.
The nation's fourth largest carrier has repeatedly said it needs additional spectrum in order to compete with its larger rivals as they look towards 4G. T-Mobile is also due a favorable roaming agreement from AT&T, which would also address criticisms of the carrier over lack of coverage.

Don't believe me about the iTunes hack? Just check Twitter
In my most recent story about Apple's hacking problems within iTunes, I was not surprised to see the same criticisms as eight months ago: there's no evidence of it, it's all the users' fault for their crappy passwords, it's a small problem.
Okay, I'll give you the possibility that this could be partially the user's fault in some way. Like saying the guy run down by a speeding vehicle shouldn't have been driving during rush hour. That does not answer how these hackers are getting in -- which from BetaNews' research on this, is mainly an in-app purchase mechanism issue -- nor the true scope of this problem.

Sony unveils next-generation mobile camera sensors
Sony Corporation on Monday announced that it is working on a new design for CMOS image sensors that will be used in camera modules for smartphones, tablets, and other mobile applications. This model of sensor includes built-in signal processing functionality, a task which used to be handled by external elements, and that it can handle advanced imaging tasks in an even smaller profile.
The design is what is known as a stacked CMOS sensor, and Sony has turned two major elements of the sensor into independent components. The stack puts the "pixel section" and "circuit section" fully on top of one another rather than fitting them on the same board side-by-side.