
The risks of public Wi-Fi and how to stay safe [Q&A]
The demands of daily lives increasingly mean that we want to be connected wherever we are. Add in the shift to hybrid working and we’re likely to want to be in touch with the office all the time too.
That makes the lure of free public Wi-Fi, whether it's in a coffee shop, a hotel or an airport, hard to resist, especially if you have a limited data allowance on your mobile contract. But of course using public networks always comes with a side order of added risk.
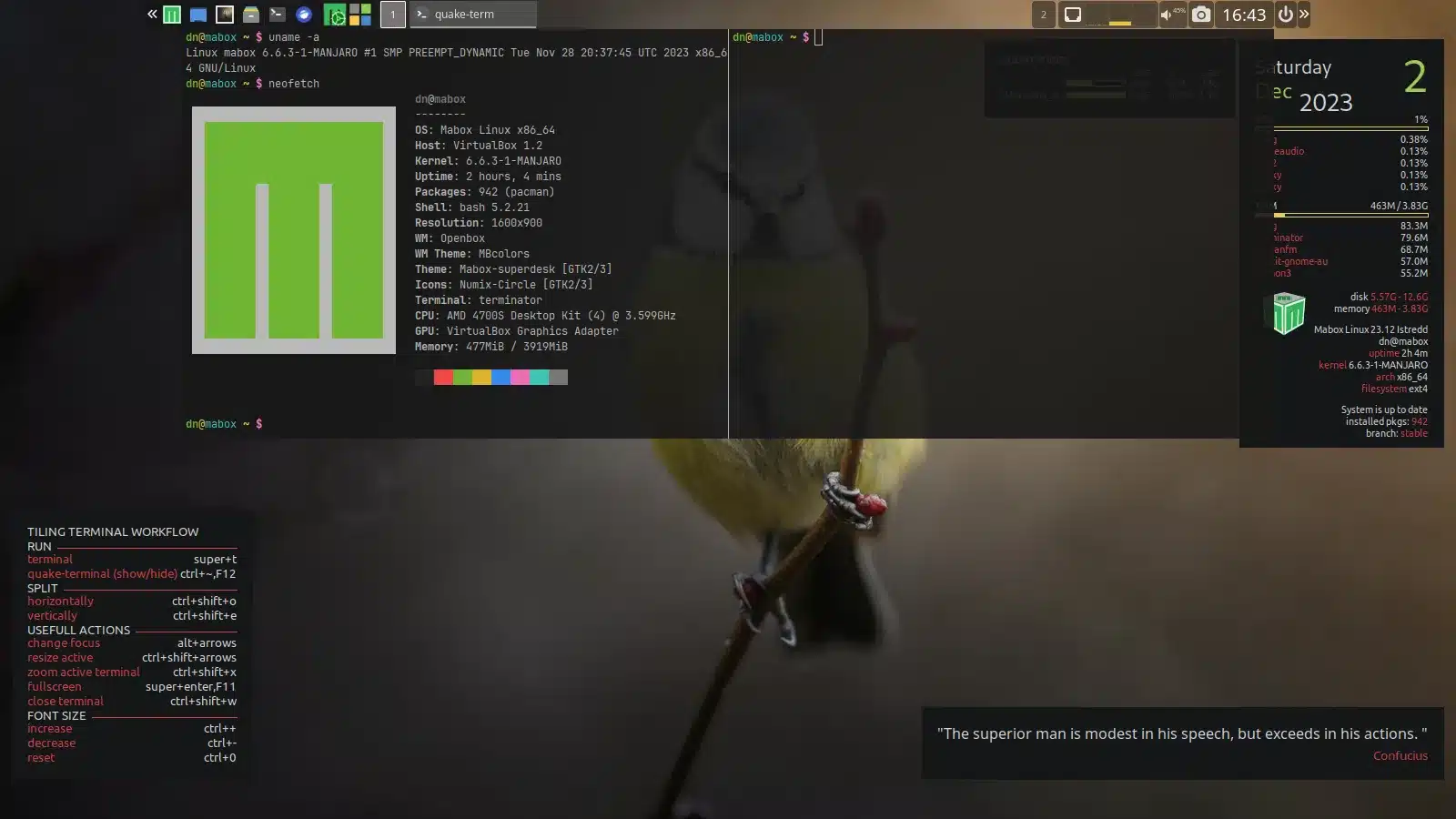
Manjaro-based Mabox Linux 23.12 features new LTS kernel
As we approach the end of 2023, the Linux community receives a delightful surprise: the December refresh of Mabox Linux 23.12. This update is not just a routine upgrade; it introduces the latest Long-Term Support (LTS) kernel 6.6, ensuring enhanced stability and longevity for users.
That 6.6 kernel promises support until December 2026, aligning with Mabox's commitment to long-term reliability. Additionally, Mabox hasn't forgotten its legacy hardware users, offering an alternative ISO with the older yet reliable LTS 5.4 kernel. Users can install multiple kernels, from the latest 6.6 to the sturdy 4.19 version, and select their preferred one at boot time.

One IdP to rule (or breach) them all: How identity access management tools can secure -- or destroy -- your kingdom
When we want to secure something highly valuable, say, a bag of ancient Spanish coins worth millions, we think of locking it behind as many layers as possible. For example, you might put it in a safe deposit box in a bank vault, nestled safely inside the institution that is itself blanketed with redundant physical security controls.
As organizations have become increasingly complex, so too have their associated layers of security around application access. Enterprises have tremendous amounts of applications and data, as well as users and devices with differing levels of permissions trying to access that data. To provide a consistent, IT-vetted method of creating, managing, storing, and authenticating the complexity of application access, we have arrived at Identity Provider (IdP) tools. IdPs are (typically) cloud-hosted services that store unique information used to identify users, organizations, and devices ("digital identities"), authenticate access requests, add/remove users, and provide security around these functions. Popular examples of solutions often used for IdP functionality include Okta, Microsoft Azure AD, and Duo.

2024 vision: Trends shaping the IT landscape
The IT and cloud computing landscape has grown and evolved in 2023, and it’s poised to continue developing in 2024. Companies worldwide are actively adapting to the dynamics of a post-pandemic world. In this pursuit of resilience and innovation, we anticipate the emergence of four key trends that will shape the new year. These trends encompass technological advancements and shifting IT paradigms regarding spending, loyalty and governance.
Here are four trends we will likely see in the new year.
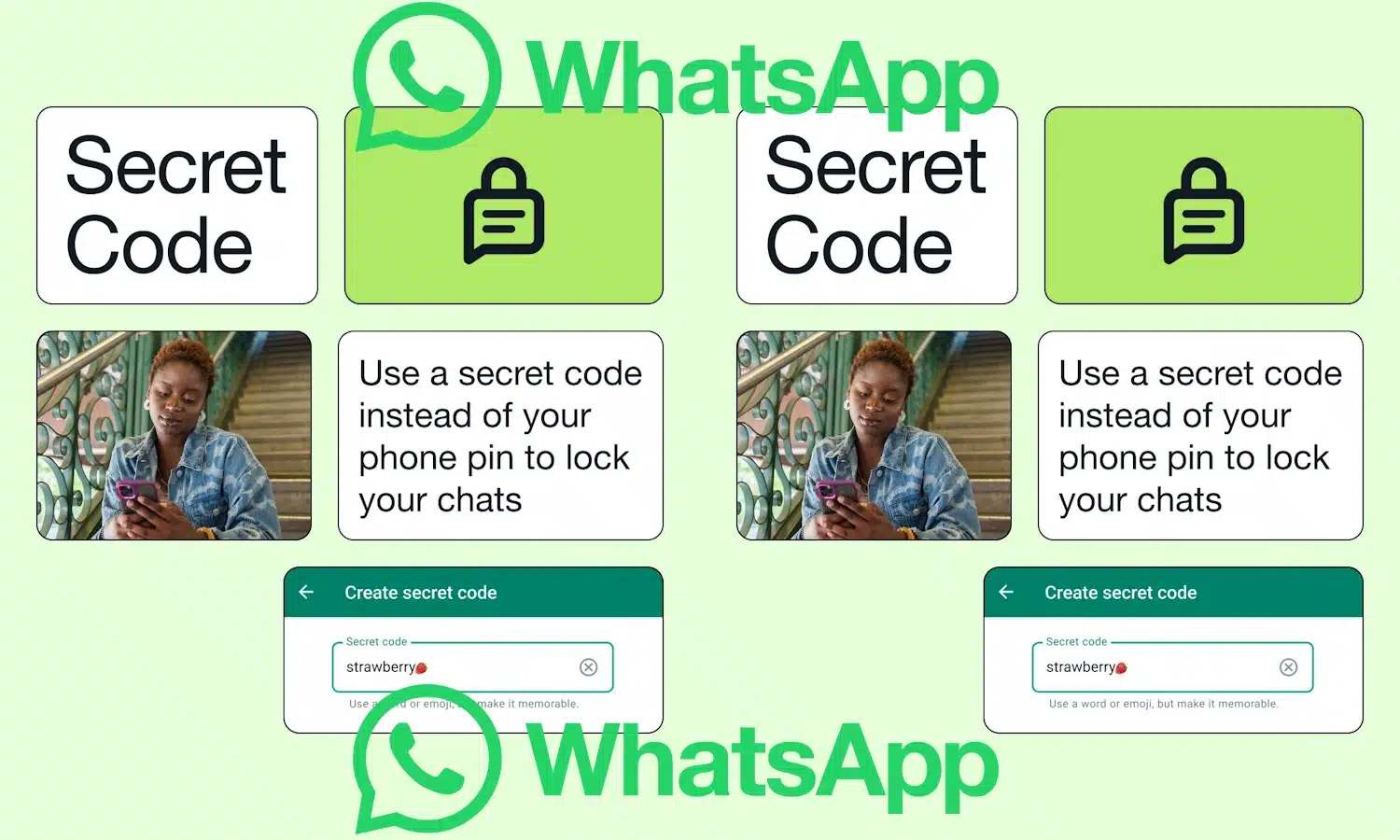
Hide and password-protect your private conversations with Secret Code for Chat Lock in WhatsApp
WhatsApp has launched a new way to help protect your sensitive conversations, extending the capabilities of Chat Lock which rolled out earlier in the year.
The newly added feature makes it possible to both password-protect and hide those chats you don't want anyone else to see. These hidden conversations can only be accessed by those who know of their existence and who have the necessary code to make them visible.

Report: Microsoft will release Windows 12 in June 2024 to ride the AI PC wave
There have been questions, hopes and rumors about Windows 12 for quite some time now, and as time goes by this is something that shows no signs of changing. We've already had hints about the successor to Windows 11 from Intel, and now Taiwanese business media has offered up more information.
According to a report in the Commercial Times, we don't have long to wait until Microsoft releases Windows 12. Timed to coincide with the rising interest in AI PCs, Windows 12 is said to be due to launch in June 2024.

Fighting the next generation of fraud
In today’s digital age, the landscape of fraud is evolving at an alarming pace. Victim profiles, which used to skew heavily toward the elderly and infirm, now include younger, fully functioning adults. In 2022, 20-59-year-olds reported 63 percent of all fraud in the United States. Industries being targeted by fraudsters are evolving as well, and now include those in crypto and gaming.
In the past, most adults were able to see through scams and avoid them. However, the introduction of generative AI has been a game changer, transforming ordinary schemes into highly sophisticated efforts. Generative AI, a subset of artificial intelligence (AI), is making waves in the world of cybercrime. It is a technology that can generate content that is virtually indistinguishable from human-created content. Whether it's producing convincing text, images, or audio, generative AI leverages deep learning and neural networks to create highly realistic and persuasive output at scale. Shady third-world country call centers have been replaced by autonomous AI tools. This capability has become a powerful tool in the hands of fraudsters.
Best Windows apps this week
Five-hundred-and-seventy-one in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft is testing new features all the time. Windows 11 users may soon get more out of their device's battery thanks to the new Energy Saver tool that is currently in development. Another change moves the Copilot button from its center position on the taskbar to the very right of it.

Google begins deleting inactive accounts
Starting from today, a new Google inactive account policy comes into effect which means that accounts that haven't been active for two years will be deleted.
So, what counts as 'activity'? Google provides a helpful list:

KB5032278 update brings Copilot to Windows 10 and improves 'news and interests'
Microsoft has released the KB5032278 update for Windows 10 22H2, bringing a number of changes and improvements including the arrival of Copilot.
This is an optional update because it is a preview of next month's patch, and because it is a preview it is a non-security update. In addition to bringing Copilot to anyone outside of the EU, the KB5032278 update also includes numerous other changes, additions and fixes.

Why you need a multi-layered strategy to secure the cloud [Q&A]
Recent cyber attacks have seen not just the usual monetary motives but also the rise of espionage attempts with attacks on government officials.
So how can organizations, both public and private sector, protect their most valuable assets? We spoke to Glenn Luft, VP of engineering at Archive360, to find out.

Microsoft could soon let you use your Android phone as a webcam in Windows
An APK teardown of Microsoft's Link to Windows app for Android (also known as Phone Link and Your Phone) shows that the company is working to bring a handy feature to handsets -- webcam functionality.
Code shows that Microsoft appears to be working on a feature to rival Apple's Continuity Camera, the feature that makes it possible to use an iPhone as a webcam in conjunction with a Mac. Now it seems that Android users are going to get a similar option under Windows.

TP-Link launches Deco BE63 BE10000 Tri-Band Wi-Fi 7 Mesh System
TP-Link has launched the Deco BE63 BE10000 Tri-Band Wi-Fi 7 Mesh System, and it looks friggin’ incredible! Designed for homes packed with many devices, the Deco BE63 offers tri-band speeds up to 10Gbps, ensuring seamless internet coverage across spaces as large as 7,600 square feet. This versatility makes it suitable for different housing types, from apartments to large multi-level homes.
The Deco BE10000 stands out in the Wi-Fi 7 mesh system market, providing gigabit speeds of up to 5.2Gbps on the 6GHz band, 4.3Gbps on 5GHz, and 574Mbps on 2.4GHz. These speeds are delivered across 8 simultaneous streams. Its performance is significantly enhanced by features such as Multi-Link Operation, a broad 320MHz band, and advanced 4K QAM technology, making it 3.6 times faster than Wi-Fi 6/6E routers. The new 6GHz band offers ample bandwidth with minimal congestion and interference, ensuring a smooth and reliable connected experience.
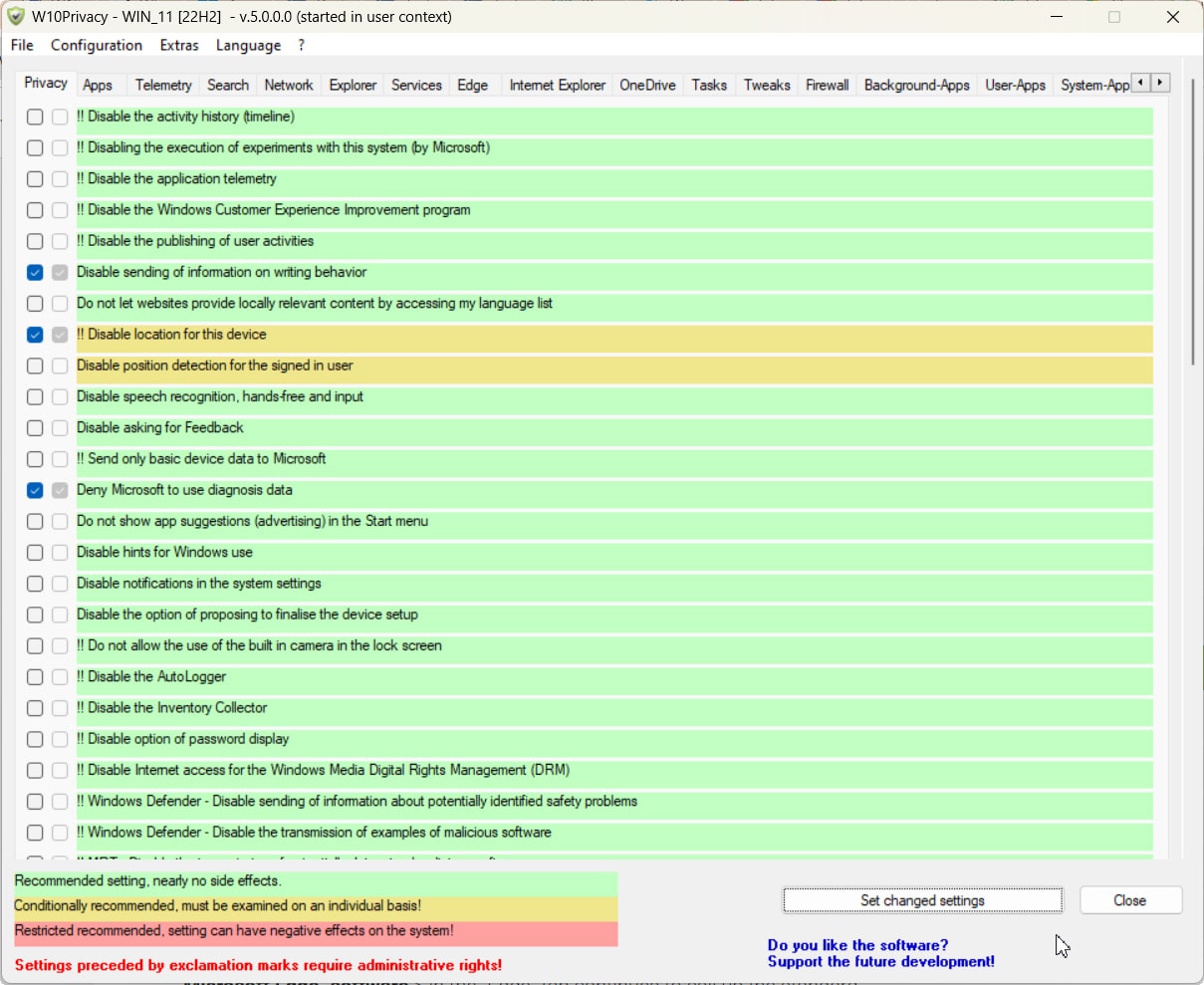
Win10Privacy 5.0 gives you complete control over your privacy in Windows 10 and Windows 11
When it was first released, Windows 10 famously spied on users and shared all sorts of information with Microsoft. Over the years, the software giant has reigned in this behavior and introduced a wealth of privacy controls to let you manage what you share.
That said, these controls are scattered throughout the OS and finding them isn’t always easy. This is where Win10Privacy can help.

Get 'AI & Data Literacy' (worth $14.99) for FREE
AI is undoubtedly a game-changing tool with immense potential to improve human life.
This book aims to empower you as a Citizen of Data Science, covering the privacy, ethics, and theoretical concepts you’ll need to exploit to thrive amid the current and future developments in the AI landscape. The book explores AI's inner workings, user intent, and the critical role of the AI utility function while also briefly touching on statistics and prediction to build decision models that leverage AI and data for highly informed, more accurate, and less risky decisions.


