
Privacy warning: Android apps infected with SonicSpy spyware can record audio
Security researchers from Lookout are warning about raft of spyware-infected apps that have been found in Google Play. Seemingly connected to Iraq, more than a thousand apps hve been found to include SonicSpy spyware.
The spyware is embedded in a variety of legitimate-looking apps, such as messaging tools based on Telegram. One such example is an app called Soniac which was found to be capable of not only recording audio and retrieving contacts, but also taking photos and gathering phone logs. Lookout warns that SonicSpy is sneaky, and tries to hide from users to avoid detection.

Leaked emails show HBO offered hackers $250,000 to delay Game of Thrones leaks
The hack suffered by HBO has been in the headlines for the last couple of weeks, not least because it led to the leak of episodes and scripts. The anonymous hackers were known to have made a ransom demand, but details of how this was handled were not made public.
Now a leaked email suggests that HBO offered the perpetrators a sum of $250,000 to delay the leaks. But rather than offering up the sum as a ransom payment, HBO refers to the money as a "bug bounty payment."

Manufacturers are cybercriminals' biggest target
Cyber-attacks all over the world are becoming increasingly sophisticated, according to a new report by the NTT Group company. According to the same report, these attacks are also growing in frequency.
The Global Threat Intelligence Center (GTIC) 2017 Q2 Threat Intelligence Report says cyber-attacks were up by 24 percent globally, in the second quarter of 2017.

Phishing is the top threat faced by organizations
Both users and their endpoint devices are the primary target for cyber criminals with phishing being the most prevalent threat according to a new report.
The study from research and education specialist the SANS Institute finds security professionals rate phishing at 72 percent, spyware at 50 percent, ransomware at 49 percent, and Trojans at 47 percent as being the top threats today.

The top five cloud security myths debunked
Increasingly businesses are moving their data and applications to the cloud. But there are always concerns about how secure the information is.
Network security company Portnox has put together an infographic looking at some of the myths surrounding cloud security and explaining why they're ill-founded.
Former MI5 chief says UK government should not weaken encryption
The UK government has made no secret of its desire to exert greater control over the internet, and home secretary Amber Rudd has gone as far as suggesting that encryption should be weakened -- and backdoors should be included in software -- to make it easier to carry out surveillance on terrorists.
Lord Jonathan Evans, the former chief of MI5 in the UK, acknowledged that encryption had got in the way of monitoring communication between extremists, but said this should not be used as an excuse to weaken security.
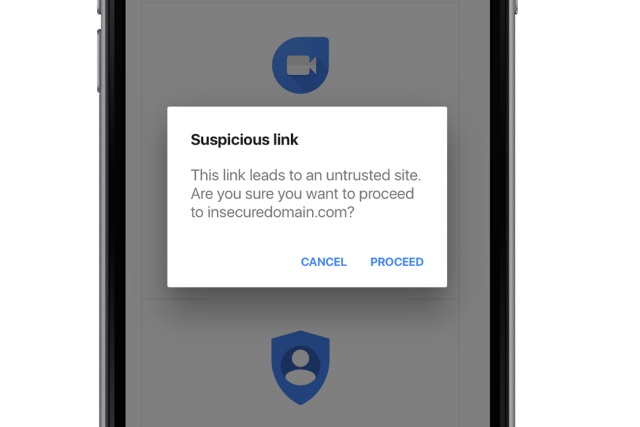
Google adds phishing protection to Gmail for iOS
A few months ago, Google brought phishing protection to Gmail on Android. Now the company is doing the same for the iOS version of the app.
The feature is rolling out over the next few weeks, and it offers a couple of safety nets to protect users from visiting potentially dangerous links in emails.

Security challenges slow down innovation in the financial sector
Organizations in the financial services sector are forced to innovate in order to stay relevant. At the same time, innovation is being slowed down by the need to keep data and applications safe, putting organizations in this vertical in quite a tough spot.
This conclusion was given out in a new report by Claranet. The report says that striking the right balance between innovation and security is becoming a "key competitive differentiator" in the sector.

WikiLeaks: CIA's CouchPotato tool grabs footage from remote video streams
The latest addition to WikiLeaks' Vault 7 cache of CIA documents and tools is a user guide for CouchPotato. This project is designed to capture RTSP/H.264 video streams, typically from networked cameras.
This is rather different to the approach taken with the Dumbo project which required physical access to a computer. The CouchPotato documentation is relatively recent, only dating back to February 14, 2014.

Microsoft announces open source Coco Framework to speed up enterprise blockchain adoption
Microsoft has today announced Coco Framework, a means of simplifying the adoption of blockchain protocol technology. The aim is to speed up the adoption of blockchain-based systems in the enterprise, whilst simultaneously increasing privacy.
Coco -- short for Confidential Consortium -- will be available in 2018, and Microsoft will be making the technology open source to help increase uptake. Intel is working with Microsoft as a hardware and software partner, and Coco Framework features Intel Software Guard Extensions (Intel SGX) to improve transaction speed at scale.

One in five people put corporate data at risk via unsecured Wi-Fi hotspots
Employees are putting corporate data at risk by using unsecured hotspots and over sharing on cloud services, according to a new report.
The study from cloud security specialist Bitglass set up Wi-Fi hotspots in random public spaces for two hour time slots, and captured and analyzed traffic, finding that of the 834 people in the public spaces, 187 unique devices (around 20 percent) connected.

Enterprises lack resources to respond to targeted attacks
The number one priority for security executives is achieving complete breach intolerance according to a new study from endpoint security company Endgame in conjunction with Forrester Research.
The study of over 150 security decision makers in large US enterprises also finds 64 percent of executives are concerned that the next breach or attack they experience could be severe, a fear that is heightened by the fact that decision makers don’t know the system or the vector that will be attacked next.

Managed service providers face cyber security talent shortage
Many businesses rely on outsourcing some or all of their IT to managed service providers (MSPs), but a new study from Kaspersky Lab reveals that two out of three MSPs are suffering from a shortage of qualified cyber security staff.
Among the findings are that cyber security is no longer seen as a separate or optional function among MSPs with 92 percent now including it as part of their portfolio of services. More than half (51 percent) cite security as essential to their customers' operational continuity in the next three to five years.

Microsoft appeases Kaspersky with security changes to Windows 10 Fall Creators Update
Two months ago, Russian security software firm Kaspersky Labs filed antitrust complaints against Microsoft in Europe, alleging that the software giant was favoring its own Windows Defender over third-party anti-virus software in Windows 10.
In response to that lawsuit, Microsoft has made changes to how the forthcoming Windows 10 Fall Creators Update works with anti-virus software, and an appeased Kaspersky has dropped its complaint.

Leaked exploits and hacking tools enable the surge of cyber attacks in 2017
Last year, the interconnectedness of cybercrime was demonstrated by a variety of supply chain hacks and other well-known cybersecurity issues that coalesced to create massive botnets powered by compromised Internet-of-Things (IoT) devices. The events from the first half of 2017 highlight another long-developing issue, which has been made worse by a variety of data dumps from actors such as WikiLeaks, TheShadowBrokers, and others: the leakage of state-sponsored and cybercriminal hacking tools and exploits.
Much like leaked personal data, once those vulnerabilities, exploits, and tools are exposed, they forever remain in the cybercriminal public domain. The May outbreak of WannaCry ransomware and the June outbreak of the data-destroying malware NotPetya both leveraged leaked NSA exploits to disrupt numerous organizations across the globe.