Why automation is the future of incident response [Q&A]

A security breach can lead to serious reputational and legal issues for enterprises. The speed and effectiveness with which they are able to respond to incidents is therefore crucial.
Larry Gagnon, senior vice president, global incident response at eSentire, believes that the way to address this is by greater automation incident response. We talked to him to find out more.
Zero Trust: A business imperative to enable the secure, hybrid-working enterprise

Without a doubt, cybersecurity will continue to be a topic riding high on the C-Suite agenda throughout 2022. With intensifying trade disputes, an escalating threat landscape, a highly distributed workforce, supply chains stretched to breaking point by the pandemic, and extra pressure exerted by the ongoing effects of Brexit in the UK and other geo-political issues, having a secure, productive, agile and cost-effective security framework in place will be paramount.
It’s evident that today’s enterprises conduct business and use digital technologies in ways that are evolving constantly. This digital transformation is making traditional perimeter-based cybersecurity IT infrastructure redundant. The days when every user and every device operating from within an organization’s premises or firewall could be automatically trusted, are over for good.
Cloud data breaches rise as adoption and complexity increase

According to a new report, 45 percent of businesses have experienced a cloud-based data breach or failed audit in the past 12 months, up five percent from the previous year.
The latest Cloud Security Report from Thales also shows multi-cloud adoption is accelerating with 72 percent of organizations using multiple IaaS providers compared to 57 percent in 2021.
Is it time to swap your password for a QR code?

Yesterday we reported on the introduction of the passwordless password manager, but as ever in the security industry other companies are never far behind a new innovation. Today LogMeOnce introduces a patented passwordless authentication method using a QR code.
With QR Code Login, rather than having to use or enter a master password to unlock the password manager, when a user wants to log into a web account, a unique QR Code will appear on the computer monitor screen. Users then use a mobile phone to scan the code and they are securely authenticated.
Pindrop delivers improved audio intelligence to combat voice fraud

Although we tend to focus on frauds as a result of online account takeovers, more traditional social engineering methods are still a major problem, as are newer threats like deepfakes.
Voice technology company Pindrop is using this week's RSA Conference to launch new features that boost the level of intelligence that can be gained from voice analysis.
LastPass launches passwordless password manager
For a company whose business is to protect passwords, going passwordless might seem a bit self-defeating, but stick with us, because there is method in this madness.
LastPass is announcing that its customers can now access their vault, and all sites stored in it, with a simple and secure passwordless login using the LastPass Authenticator.
Qualys updates vulnerability management with automated workflows

Security and compliance specialist Qualys is releasing the latest version of its Vulnerability Management, Detection and Response (VMDR) solution with TruRisk, which offers risk-based vulnerability management for insights into an organization's unique risk posture, allowing it to prioritize its most critical threats.
Qualys VMDR 2.0 gives security and IT teams a shared context and the ability to create workflows via drag and drop technology to quickly align and respond to threats.
New tool aims to stop 'Solver Service' bots

Researchers at anti-bot specialist Kasada have recently uncovered the use of 'Solver Service' bots -- an API-as-a-service tool created to bypass the majority of bot management systems.
By 'solving' a bot detection system's defense, these allow enterprising cybercriminals to now commercialize the Solver Service they deciphered and sell it for a profit. This means buyers can successfully conduct automated bot attacks without any technical skills -- and without having to worry about what bot defenses a site may have in place.
OpenSSF looks to further strengthen supply chain security

As we reported a few weeks ago, OpenSSF in conjunction with the White House and others has launched a 10-point plan and funding with the aim of improving the security of the software supply chain.
OpenSSF has also announced a number of new members including premier members, Atlassian and Sonatype, who will join the OpenSSF governing board.
Five steps to a secure cloud architecture

Policy as code is central to establishing and maintaining secure cloud architecture by enabling security teams to impart their knowledge across the organization in a common, machine-readable language.
Cloud computing cyberattacks don’t play out like the scenes from Hollywood thrillers. No one is slowly lowering Tom Cruise into a preselected target’s secure data center equipped with ultrasensitive noise, temperature and motion detectors so he can steal a specific file.
0patch releases free fix for Follina vulnerability in Windows as Microsoft apparently can't be bothered

This week, we have written about the Follina zero-day vulnerability that allows for remote code execution on a victim's computer. Despite having been known about for a number of weeks, Microsoft is still yet to issue a patch for the actively exploited critical security flaw, instead simply offering details of a workaround.
As has been the case in the past, a third party has come to the rescue. Micro-patching firm 0patch has released a free fix for the vulnerability -- for Windows 11, Windows 10, Windows 7 and Windows Server 2008 R2 -- which is tracked as CVE-2022-30190 and relates to the Microsoft Windows Support Diagnostic Tool (MSDT) component of Windows.
Poor alerts hamper effective automation of threat detection

According to a new report 85 percent of IT security professionals have experienced preventable business impacts resulting from insufficient response procedures, while 97 percent say that more accurate alerting would increase their confidence in automating threat response actions.
The State of the Modern SOC report from Deepwatch is based on a survey by Dimensional Research of over 300 security professionals, working at US organizations with 1,000 or more employees.
APIs and cloud apps are greatest threats to enterprise security readiness

A survey of over 400 CISOs finds they are are grappling with a wide range of risks and challenges, especially linked to accelerating utilization of technologies like cloud-based applications and the use of Application Programming Interfaces (APIs).
The study from CISOs Connect, an invitation-only community of cyber experts and part of Security Current, finds the IT components rated as most needing improvement are: APIs (42 percent), cloud applications (SaaS) (41 percent), and cloud infrastructure (IaaS) (38 percent).
Almost half of IT security leaders believe they won't be breached

A new study shows 47 percent of security leaders do not believe they will be breached despite the increasing sophistication and frequency of attacks.
The survey of 1,000 IT and security professionals across eight countries, conducted by The Enterprise Strategy Group for Illumio finds in the past two years alone 76 percent have been attacked by ransomware and 66 percent have experienced at least one software supply chain attack.
Microsoft Entra is a new identity and access-focused family of products
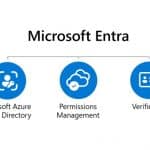
Microsoft has launched a new family of products called Entra. Microsoft Entra encompasses a number of identity and access management solutions including the existing Azure AD. The launch comes after the acquisition of CloudKnox Security last year, and is Microsoft's attempt to help boost security across multicloud environments -- or "secure access for a connected world".
Bolstering the product family, the company has also launched cloud permission management tool Microsoft Entra Permissions Management, and Microsoft Entra Verified ID -- a system that allows for more secure interactions, based on decentralized identity standards. Microsoft has also announced public previews of Workload Identities and Lifecycle Workflows.
Recent Headlines
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.