Monitor and analyze your network traffic with SmartSniff
We recently wrote about Microsoft Message Analyzer, and explained how it could be used to monitor and better understand your network and internet traffic.
It’s a hugely powerful tool, but also bulky and with an intimidating interface. If you’d prefer something more lightweight, then as usual, NirSoft might have the answer.
SmartSniff is also a network monitor which tries to capture the TCP/IP packets that pass through your chosen network adapter, then allows you to view, filter and display them.
Like Microsoft Message Analyzer, the program is very configurable. But unlike Microsoft’s offering, it’s portable, and a mere 100KB download.
To get started, open the program, click the green "Play" button toolbar and select the network adapter to use.
SmartSniff can capture packets using WinPcap and Microsoft Network Monitor, but is also able to use raw sockets if you’ve nothing else installed.
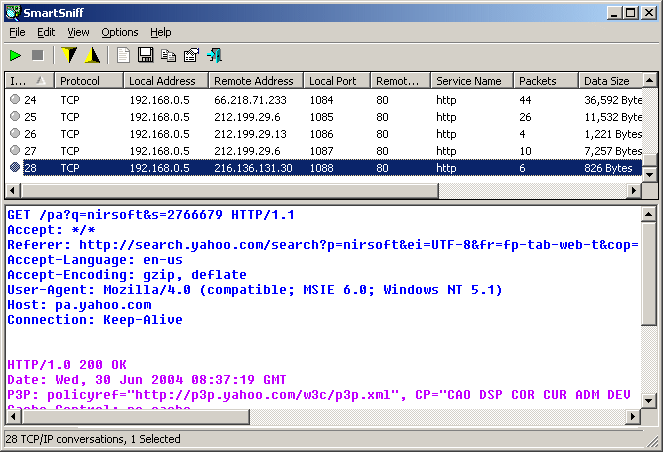
Once capture has started, collect some emails, open a browser, visit a website or do something else internet-related. With any luck the packets should be captured and various details displayed: protocol, local and remote addresses/ ports/ hosts, service name, data size, capture time, local and remote MAC address, and more.
If there’s a lot of activity this could be hard to follow. Click Stop to stop capture when you’ve had enough.
Browse down the report looking for interesting activity. This might be an IP address or remote host you don’t recognize, an unusual port number, maybe something that’s transmitting a lot of data and you don’t know why.
If you’re trying to diagnose an email issue, for instance, you might look for a relevant "Remote Host" (mail.something.com), "Service Name" (pop3) or "Remote Port" (110).
We clicked on the first element of a POP3 exchange and SmartSniff displayed the full conversation in plain text, including the account user name and password.
Further down was a "Remote Host" we didn’t recognize, static.xx.xx.xx.xx-clients.your-server.de. What was this? Clicking it displayed a hex dump of the traffic which included the text "www.tunnelbear.com", a VPN installed on our system -- suddenly it all made sense.
Display filters help you drill down to the information you need. Click Options > Display Filter and enter include:remote:tcp:80 to display only web traffic, for instance, or use include:remote:tcp:110 to focus on that pop3 activity.
A huge number of configuration options allow you to define what’s capturing, how it’s displayed and exactly how SmartSniff works.
Once you’ve finished, SmartSniff is able to save both its own report and the stored network packets. That’s helpful for you, but be very careful if you share it with others. The data could contain user names, passwords and other confidential information.
SmartSniff’s raw sockets capture method won’t work in every situation, and it doesn’t have the charts, graphs and other views of Microsoft Message Analyzer.
But then again, you can download and be running it in seconds, on anything from Windows 98 up (yes, really), and there’s still more than enough power here to handle many simple network troubleshooting tasks. Grab a copy immediately.
SmartSniff is a free application for Windows 98 and later.
