Amazon is shutting down its Freevee app in August

Amazon has finally announced when the Freevee streaming video app will close for good. As of next month, the Freevee app will be inaccessible, with content now being available on Prime Video instead.
The shuttering is no surprise, as the closure was announced last year. At the time, however, Amazon did not specify a timeline for how things would pan out. Some eight months after the original announcement, the company has finally revealed that the Freevee app will be shut down in August 2025.
Google reduces Pixel 6a battery life with mandatory Android 16 update
In just a few days, Google is starting the rollout of a mandatory automatic software update to Android 16 for Pixel 6a handsets. While an update would generally be expected to add features or improve performance, this particular, unavoidable update will have an unwanted side effect for some handset owners.
Having determined that some Pixel 6a handsets are a risk of an overheating battery, the update is being used to reduce battery capacity and charging performance on impacted devices. For users who are unhappy with this, there is the option of a battery replacement, but there are eligibility criteria.
Microsoft announces another round of layoffs as it plows money into AI

Microsoft plans to further reduce its global workforce, having already trimmed back on employee numbers several times this year.
The company is yet to provide exact details of the number of people affected by the latest round of layoffs, and it has also not revealed which divisions are to be hit. Microsoft has confirmed, however, that the cutbacks represent less than 4 percent of its workforce, leading to estimates of around 9,000 layoffs.
Microsoft acknowledges Intune issue that wipes out security customizations

Microsoft has published a warning about a problem in its Intune management software that stops customizations from being saved. Stemming from an issue in the security baseline policy update flow, an update can wipe out settings that have been put in place by administrators.
Although Microsoft has acknowledged the problem, the company is currently working on working out how to address it. In the meantime, Intune users are being told to use a workaround that could prove to be time-consuming for many.
Microsoft releases PowerToys v0.92 with new features for many modules
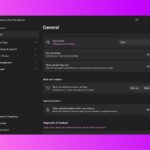
If it feels as though it has been a while since PowerToys received an update, that’s because it has been a number of weeks. But now this changes. Microsoft has launched PowerToys v0.92.0 as part of a release cycle that focuses on new features, stability, optimization improvements, and automation.
Every PowerToys release causes fans of the utility suite to ask whether any new modules have been added. This time around there are no completely new utilities to play with, but there a so many modules that have gained new features and improvements that it’s hard to remain disappointed for long.
X turns to AI-powered bots to write Community Notes to clarify posts

X has announced the latest addition to Community Notes as the social platform seeks ways to replace third-party fact checkers. The company is giving developers the option of building AI bots that can write notes that provide further details, clarity and context for posts.
The AI Note Writers are not being allowed to run completely free, however. X says that the aim of the AI Note Writer API is to help humans rather than replace them, pointing out that the bots “must earn the ability to write notes, and can gain and lose capabilities over time”.
Elon Musk confirms everyone is getting the 'all new' XChat this week, complete with 'Bitcoin style encryption'

Looking to compete with the likes of Signal, Elon Musk is ready to rollout XChat to all users of his X social platform. Rather than being a separate app for chatting, however, XChat is essentially just direct messaging within X -- so who is it for, and what does it have to offer?
Taking inspiration from numerous sources, Musk says that in addition to text-based messaging, there is also video and audio calling. Other features include vanishing messages, the option to “send any kind of file”, and an undetailed encryption system.
Microsoft is making huge changes to Windows 10 and 11, cutting out nagging to use Edge... for some
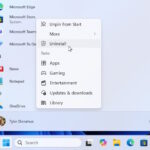
There can be few Windows users who have not been frustrated by notifications suggesting that they use Microsoft Edge as their browser. Microsoft’s heavy-handed promotion of its own web browser has been the source of annoyance, frustration and lawsuits for some time.
Now the company is relenting, making sweeping changes across Windows 10 and Windows 11 that will stop some of the pestering to use Edge, and also make it easier to change default browsers. More than this, it is making changes to Windows Search, the Microsoft Store and many other apps... but not for everyone, and not because it wants to.
Microsoft releases emergency fix for Windows 11 startup problems

Following the release of the KB5058405 update last month, Microsoft acknowledged that it was causing problems for some users. Affected users were left with startup issues and a warning of a 0xc0000098 error in the ACPI.sys file.
Now the company has released an out-of-band fix for the issue in the form of the KB5062170 update. Such is the impact of the original problem that Microsoft recommends installing this update in place of the May 2025 security update for Windows 11.
Microsoft says it is ending USB-C confusion with updated Windows 11 WHCP

USB-C was supposed to be the connection that simplified everything -- but it has ended up doing anything but making things simple. With different USB generations, and within those generations different levels of capability, it is no wonder people are confused about just what their USB ports and cables can do, and what level of capability to expect.
This is something Microsoft is looking to change. Pointing to the “inconsistent implementations of USB-C port capabilities across the PC ecosystem”, the company is seeking to end USB-C port confusion by using the Windows Hardware Compatibility Program (WHCP) to help people know precisely what to expect from certified PCs.
Microsoft Security gets a style upgrade that goes beyond the surface to embrace the human

Padlocks, chains, keys, shields: these are all stereotypical images used to represent security. They are also the themes -- tropes, if you will -- that have been avoided in an eye-catching and vibrant rebranding for Microsoft Security.
A team at Koto -- a creative studio also behind design projects for Amazon, Riot Games, FitBit, WhatsApp, and more -- is responsible for a bold new brand identity that sidesteps the obvious. Instead, the new look that is bold yet human, clear and confident.
Instagram announces support for the most commonly used photo aspect ratio
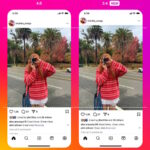
Post an image to Instagram and it will almost certainly be automatically cropped. The reason for this is that, until now, the platform has supported 4:5 aspect ratio images, as well as the Instagram staple -- the square format.
But this is not in line with how most people shoot photographs, and the platform is finally taking this into account. There is now support for a new (new to Instagram, at least), aspect ratio.
No prizes for guessing what's to blame for the latest problem that stops Windows 11 booting (yep, it's another OS update)

Windows updates that cause problems are far from being uncommon, sadly, but the latest issue is a pretty serious one. Some users who have installed the KB5058405 update from earlier this month have found themselves with an non-booting system.
Those affected will note a 0xc0000098 error in the ACPI.sys file, and a message informing them that their device needs to be repaired. The bad news does not end there. Microsoft does not yet have a fix -- or even a workaround.
Your WhatsApp status just got a huge upgrade that injects creativity and personality

While WhatsApp is, ostensibly, a messaging, chat and video calling platform, it is more than that; it is also a pseudo social media platform. The Status section of WhatsApp has gradually evolved over the years to become a way to not only indicate your availability, but to express much more.
And now Status has received another massive upgrade. It is now possible to display a collage of multiple photos, share music, and much more. A plethora of new options are rolling out globally; here's what you have to look forward to.
Get your hands on the new Windows Share feature and try out Click To Do enhancements with the KB5058499 update for Windows 11

Microsoft has released a preview version of the KB5058499 update for Windows 11, adding a host of new features to the operating system -- many of them, predictably, AI-oriented.
The biggest additions are updates to Click To Do, as well as the rollout of the new Windows Share feature. There is also “Cross device resume” to allow for seamless device migration when using OneDrive files, and much more.
Sofia Elizabella's Bio
Sofia Wyciślik-Wilson is a queer, transgender journalist based in Poland. She has been writing about technology for more than two decades, and after years working for magazines, her writing moved online. She is fueled by literature, music, nature, and vegetables. You can find her on Bluesky and Mastodon. If you like what you read, you can Buy her a Coffee!
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.
