Faster or more secure? Microsoft publishes IE patch to Automatic Updates
Given the choice between speed and security, Betanews readers this week have been siding with security, in a show of support that suggests that Windows Vista had the right idea after all. This morning, Windows XP, Vista, and Windows 7 users who have their Automatic Update notifications turned on manual will be making that choice, as Microsoft has published update 976749 -- released as a manual update on Monday -- to its Windows Update service, not as a "security update" or anything "critical" or even "important."
It's an "Update for Internet Explorer" whose purpose is to "resolve issues that may occur after installing the Internet Explorer cumulative security update issued as MS09-054" -- one of the major updates from the last Patch Tuesday round. The issue that update addressed is a very serious one, and Windows users who are concerned about their operating system possibly being vulnerable to a new class of attack, should apply that update and also apply the patch to that update, released this morning. Many users with Automatic Updates turned on full may wake up this morning with the update already having been applied.
Those folks may notice a difference, or they may not. There will be a performance cost, at least with respect to all versions of Internet Explorer since 5.01, but also to other features of Windows that rely on Internet Explorer. Betanews readers have suggested that this performance cost will be negligible, especially for those who do not time their browser with a stopwatch.
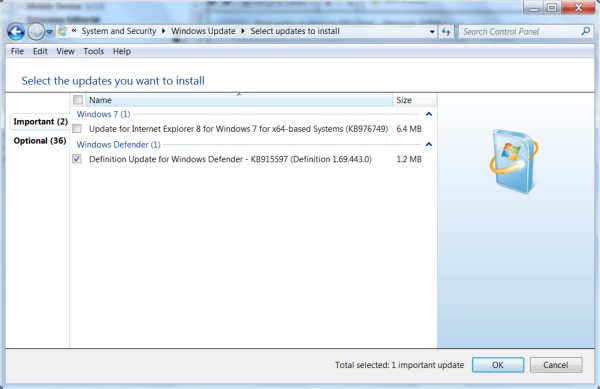
However, Betanews tests reveal the performance hit completely wipes out at least one category of speed increase that is the subject of recent Microsoft television advertising: a faster Web experience for those who prefer IE. Our tests show that, after update 976749 is applied, IE8 on Windows 7 is no faster than IE8 on Vista SP2 on the same machine.
Right now, the vulnerability exists more in concept than in practice. Although no known exploit appears to have been discovered yet, it's the architecture behind that vulnerability that makes it very serious at the outset. Conceivably, if and when an exploit appears and a patch is published to thwart it, malicious users could craft a variation of the exploit quite easily. The problem has to do with a fundamental programming technique that could be discontinued in the future, but which is pervasive throughout applications of all classes, from Microsoft and everyone else, and not just for Windows. Microsoft is treating the issue quite seriously, judging from the company's recent communications with us.
But the defense against this problem comes at an inopportune time for Microsoft, which is working to promote Windows 7 to consumers as better than its predecessor for being both more secure and faster. Of course, there are other Web browsers, perhaps all of which perform much faster and are arguably more secure. But Microsoft had been hoping to market IE8 as a solid contender, with some features like Web Slices and Accelerators that third-party alternatives have not yet matched. Microsoft may have to take a hit for publicly securing IE -- arguably the more responsible course of action -- at a time when Windows 7 is just coming out of the gate.
