Are you a defense contractor? Beware the Elderwood Project!
 The Hydraq (Aurora) Trojan horse is in the spotlight, courtesy of a hacking group that uses it to wreak havoc with the security of numerous renowned industries. While these hacking maneuvers were pretty high profile and as a result got a lot of coverage, it is the said group’s hacking activities, and patterns, that have caught the eye of a lot of security pundits and writers.
The Hydraq (Aurora) Trojan horse is in the spotlight, courtesy of a hacking group that uses it to wreak havoc with the security of numerous renowned industries. While these hacking maneuvers were pretty high profile and as a result got a lot of coverage, it is the said group’s hacking activities, and patterns, that have caught the eye of a lot of security pundits and writers.
Zero-day exploits, another term brought to fame by these hackers who took the computer spy software game up a few notches, has been used by the group to not only penetrate the security of the targeted organization, but also the manufactures that were servicing the said company in their cross hairs.
Elderwood Project
The hacking group is meticulously systematic in the way it goes about its business. When we say systematic, we intend to highlight their re-use of components of a particular infrastructure that has been dubbed “Elderwood Platform”.
The name basically traces its origin from the exploit communication, Elderwood, which helps the hackers deploy the aforementioned zero-day exploit strategy to expose holes in the security systems of leading defense contractors. The methodology -- or the hacking ideology, if you will -- is synonymous with spear phishing emails that are used to throw computer spy software bombs at the target. However, there has been a recent trend of “watering hole” attacks (for more specifics, see below).
This entire project is called “Elderwood Project”, which has been a lesson in tech violence for the hacking mafias all over the globe.
Zero-day Vulnerabilities
The really malicious zero-day vulnerabilities -- ones that a real keylogger exponent would eye -- are wildly exploited and influence a common software and are rare; there were eight of them last year. Even so, while the previous year collectively accounted for eight zero-day vulnerabilities, in a dramatic turn of events the last few months have witnessed four such uses of the vulnerabilities by the Elderwood mafia. And while there is a multitude of other hacking groups that use these exploits -- namely Nitro, Stuxnet, Sykipot et al -- such frequent use is a serious oddball; and no other hacking group exploits the vulnerabilities with similar frequency.
What these zero-day exploits divulge is the technical capability of the hackers. For, an Average Joe hacker can’t pull these hacking maneuvers off with such frequency, and with such deadly effectiveness.
Unearthing the Menace
Digging out these vulnerabilities, or discovering them, requires the attackers to reverse-engineer the applications, and their effort would be substantially less if the source code was in their knowledge. Considering the ease with which this group tracks these zones to exploit, it seems as if they have this unfathomable reservoir of zero-day vulnerabilities, and that they can dig one out at will. Understandably, vulnerabilities are used when they are needed and often in close succession -- primarily because there is no better way to consolidate the initial exposure by firing the next bullet as quickly as possible.
Target Identification
The hacking stratagem is such that the primary targets need to be identified from within the realm of the defense supply chain, but they do not have to be from the upper-echelons of the defense organizations. The targeted companies are those that manufacture components, electronic or mechanical, which are sold later on to the topmost defense companies. This is conjured up after monitoring the easier-to-exploit security postures and using them as the stepping stone to bigger and better contractors to eventually capture a top-ranked defense company.
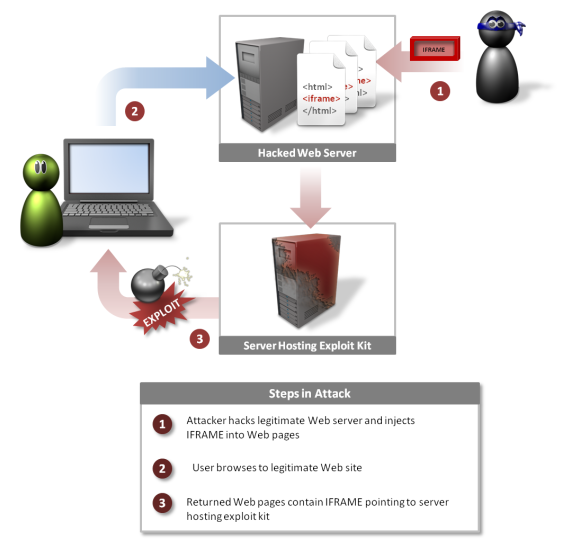
The Watering Hole
Another infection mechanism, that would put the stealthiest of keylogger mafias to shame, is the “watering hole” maneuver, which is the hacking group navigating totally different waters (pun again intended). The concept of this attack, wherein the name is extracted from, is akin to a predator waiting in the wings, as if in a desert’s water hole. Since the predator knows that his targets would obviously come to the water hole, so instead of prowling around and hankering after the victims, the predator waits for the targets to come to him.
Attackers trace a particular website, which caters to a particular audience, the one that the hacking group eyes. Once the website is identified, the hackers penetrate its defense and then inject one of their exploits into a page of the website knowing that their target users would eventually visit it. And when one of the targeted users visits the page, they are compromised and a ‘back door Trojan’ is conveniently installed into their PCs -- like a moment from their worst computer spy software nightmare.
The Threat Prevails
These hacking techniques are being used with increasing frequency, owing primarily to their uncompromising effectiveness. This increase in use requires hackers to delve into a wider array of stolen information, which then aids their targeted email attack, which in turn ensures that it is game set and match on many a victim as a deadly Web injection injects their device’s most feared malady into the system. All manufactures in the defense supply chain need to be on the lookout for attacks that originate from their business partners, subsidiaries and any associated partners -- they could be compromised and would bring the security of the bigger companies under jeopardy.
All manufacturing companies and the related personnel at the helm should brace themselves for a menace-laden 2013, especially those that have had to bear the brunt of this deadly hacking group in the past. The knowledge and the experience that the hackers mustered in their previous attack would surely aid them come up with something even more beastly the next time around.
Photo Credit: Kheng Guan Toh/Shutterstock
Graphic: Symantec
Natalia David blogs for mobistealth, an author who significantly contributes towards computer and cell phone monitoring, android spyware and smartphones. If you want to know more about her you can follow her on twitter @NataliaDavid4