CryptoLocker ransomware is flourishing
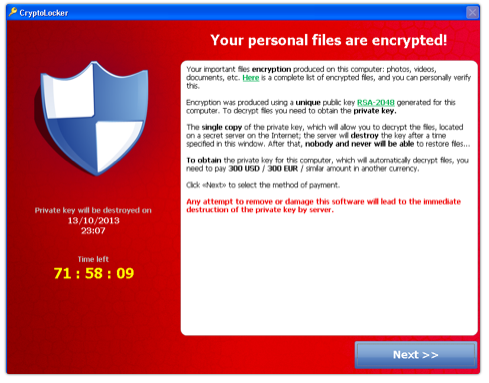
The number of CryptoLocker infections is rising, causing problems for administrators and potentially raising millions of dollars for the malware authors behind it.
Security awareness training firm KnowBe4 says it's seeing a rise in the number of complaints about CryptoLocker as users are tricked into opening attachments and infecting their workstations.
"We have been getting a lot of system administrators calling us to request security awareness training because their end users have been tricked into opening up attachments of phishing emails and infected their workstations with the CryptoLocker malware," says Stu Sjouwerman, CEO of KnowBe4. "It started last September and is not going away but actually getting worse".
Ransomware is generally spread by attachments to emails -- fake tracking notices purporting to be from couriers like DNL, UPS and FedEx are a common form of attack. Less frequently infection can be via a malicious website that exploits outdated browser plug-ins.
Once triggered the malicious code detects the personal files of the user and wraps them in strong encryption, demanding a $300 ransom to decrypt and a short window of time in which to pay up. This affects both locally stored user files and remote shared folders, encrypting every file with standard Office extensions as well as images and PDFs.
Sjouwerman recommends IT managers ensure they have an effective working backup. But even so removing the infection will involve wiping and rebuilding the machine and restoring files which can take several hours.
Antivirus companies are working to combat CryptoLocker and some programs can prevent it from running, but frequent changes to the code make it hard to eradicate. Sjouwerman says, "The need for security awareness training shouldn't be overlooked. Despite the best efforts of IT and antivirus companies, sometimes the attachments are blocked by existing filters as 'possible malware' but users request them to be released and the (outsourced) help desk releases them. Users might not initially admit they opened an attachment saying it it did nothing, until they are locked out of their files and the infection has spread".
You can find out more about KnowBe4’s Kevin Mitnick Security Awareness Training 2014, how it can teach users to recognize threats and avoid the social engineering tricks used to get them to click on infected attachments, by visiting the company's website.