Time’s up! CryptoLocker ransomware is back in business
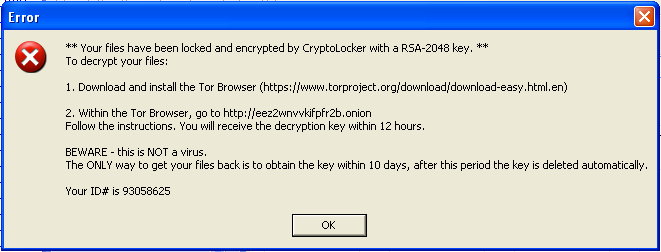
CryptoLocker recently had something of a setback when law enforcement agencies managed to seize control of servers running it and the GameOver Zeus botnet. Britain's National Crime Agency (NCA) declared this would give computer users a unique two week opportunity to secure their systems, which seemed a rather precise claim.
It turns out that prediction wasn’t too far off the mark. Three weeks after that warning, and CryptoLocker is indeed making its return, this time as a standalone threat. The new strain does not rely on 2048-bit RSA encryption nor need a Command and Control server to work.
The Trojan encrypts data on the affected computer, switching the extensions of affected files to .cryptolocker afterwards. It uses a weaker encryption method than the original, so it’s possible experts may be able to regain access to the locked files, but this won’t be an option for most infected users.
According to KnowBe4 CEO Stu Sjouwerman, "More ransomware copycats will show their ugly heads this year. Law enforcement recommends not paying any ransom for two reasons: first to discourage the criminal practices, and second it’s uncertain if they will keep their end of the bargain and provide the decryption. While we agree, many companies may be forced to pay ransom if their backups failed rather than experience months or years of lost work".
You can find out more about the new strain of CryptoLocker by reading this post on the Fakebit blog.
Photo Credit: Ollyy/Shutterstock