Malicious SSL content more than doubles in six months

As the overall percentage of encrypted traffic increases, hackers are increasingly using SSL to conceal device infections, and hide their other activities.
A new study from Zscaler finds that an average of 60 percent of the transactions in the Zscaler security cloud have been delivered over SSL/TLS.
"Hackers are increasingly using SSL to conceal device infections, shroud data exfiltration and hide botnet command and control communications. In fact, our study found that the amount of phishing attempts per day delivered over SSL/TLS has increased 400 percent from 2016," says Deepen Desai, senior director, security research and operations at Zscaler. "SSL inspection is a necessity in ensuring the security of network traffic in the enterprise. Zscaler sits between users and the internet, inspecting every byte of traffic, including encrypted traffic, so we can catch hidden threats before they get into the network."
Zscaler saw an average of 300 hits per day for web exploits that included SSL as part of the infection chain. The most prevalent malware family making use of SSL-based callbacks was Dridex/Emotet, which contributed 34 percent of the total unique, new payloads in 2017.
Of the new malicious payloads leveraging SSL/TLS for C&C activity, 60 percent were comprised of multiple banking Trojan families including Zbot, Vawtrak and Trickbot. 25 percent were made up of of ransomware families and 12 percent were infostealer Trojan families like Fareit and Papras. The remaining three percent were from other miscellaneous malware families.
You can see a summary of the findings in infographic form below.
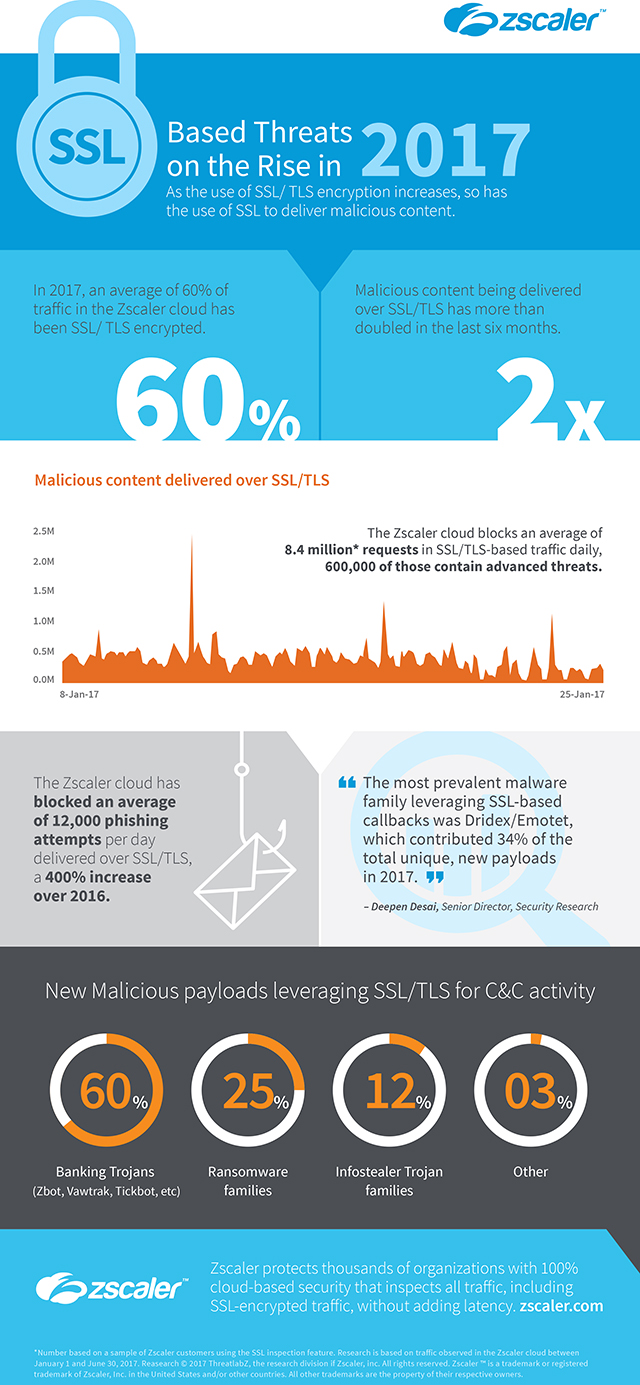
Photo Credit: adike/Shutterstock