2017 -- the year malware became evasive

While 2017 saw enhancements in defenses -- such as the use of artificial intelligence -- it also demonstrated that cyber criminals continue to find their way around defensive measures with new evasion techniques.
Anti-evasion software specialist Minerva Labs has released its Year in Review report, which takes an in-depth look at the approaches used by common malware families to bypass anti-malware tools, including antivirus and analysis sandboxes.
Among the findings are that exploit kits, which target vulnerabilities in client-side software of website visitors remained an effective attack vector in 2017. Of the campaigns tested 99 percent were evasive either in the exploit kit or the payload phase. Exploit kits were also among the most common ways to spread ransomware in 2017 with over 60 percent of them applying evasive techniques.
As part of their ransomware research activities, Minerva Labs has collected representative samples from 60 different ransomware families, including Locky, Spora, TeslaCrypt, Cryptomix, JigSaw and more. Of the evasive techniques found, roughly half of the samples used memory injection, 28 percent used weaponized documents to deliver malware and 24 percent used environment tests to check whether they are in a hostile environment -- like a sandbox -- before executing the attack.
Beyond benefiting from the 'established' revenue sources, such as ransomware, adversaries continued to look for additional profitable endeavors, which fueled a steady rise in malicious cryptomining closer to the end of the year.
"Evasion techniques will be used in both classic forms of malware, such as ransomware, as well as in malicious software that offers adversaries new revenue streams, such as malicious cryptominers," says Lenny Zeltser, vice president of products at Minerva Labs. "On the defender side, incident response teams will look for ways to more actively combat malicious presence in the enterprise in 2018, going beyond the practice of merely identifying which systems might have been compromised."
The full report is available from the Minerva website and there's a summary in infographic form below.
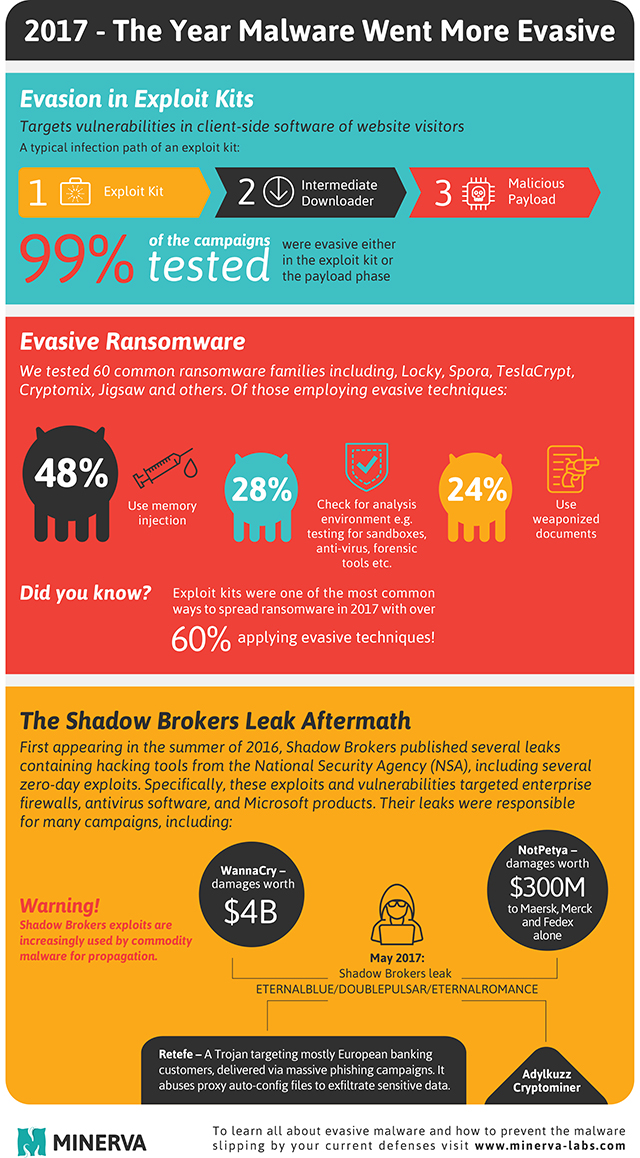
Image Credit: Brian A Jackson / Shutterstock
