Legacy defenses can't keep pace with new cyber threats

Attacks such as ransomware are able to bypass legacy security solutions because organizations are neglecting to patch, update, or replace their current products according to a new report.
The study from cyber security company Webroot also shows cryptojacking gaining ground, with over 5,000 websites being compromised with JavaScript cryptocurrency miner CoinHive to mine Monero since September 2017.
Polymorphism, which involves creating slightly different variants of malicious or unwanted files, has become mainstream too according to the report. In 2017, 93 percent of the malware encountered and 95 percent of potentially unwanted applications (PUAs) were only seen on one machine. This means the identifiers are unique and undetectable by traditional signature-based security approaches.
"Over the past year, news headlines have revealed that attackers are becoming more aggressive and getting extremely creative," says Hal Lonas, chief technology officer at Webroot. "Cryptojacking made our threat report for the first time this year as an emerging threat that combines everything an attacker could want: anonymity, ease of deployment, low-risk, and high-reward. Organizations need to use real-time threat intelligence to detect these types of emerging threats and stop attacks before they strike."
Among other findings are that Windows 10 is almost twice as safe as Windows 7. Yet the migration rate remains slow, with only 32 percent of corporate devices running the newer OS by the end of 2017.
Phishing attacks are becoming better targeted too, using social engineering and IP masking to achieve greater success. On average, phishing sites are online from only four to eight hours, meaning they’re being designed to evade traditional anti-phishing strategies. Only 62 domains were responsible for 90 percent of the phishing attacks observed in 2017.
You can find out more in the full report on the Webroot site, and there's summary of the findings in the infographic below.
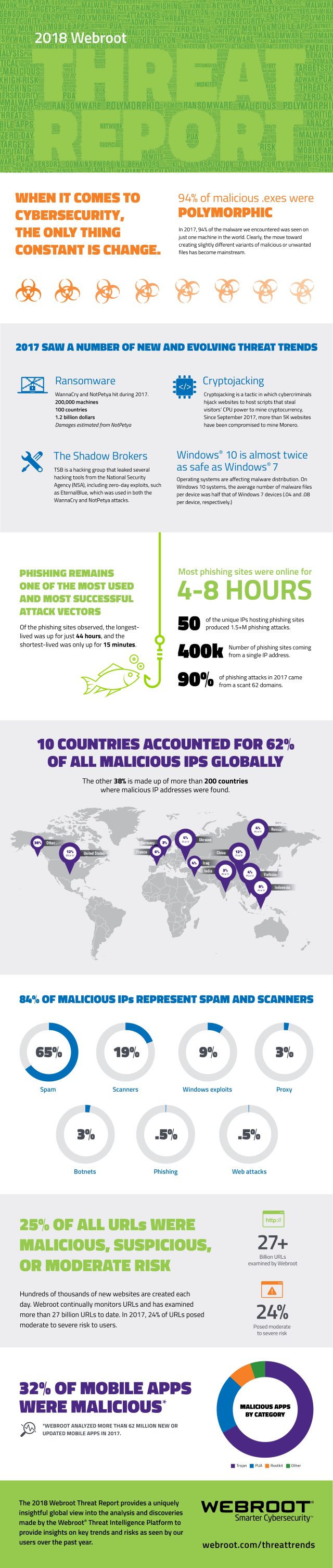
Image Credit: Jurgen Priewe / Shutterstock