Linux and Raspberry Pi machines become top targets for credential hacking

New research shows that hackers are regularly gaining access to servers with the same commonly used -- often default -- passwords.
The data from Bulletproof also reveals that default Raspberry Pi usernames and logins feature prominently on the list of top default credentials used by hackers.
The research conducted throughout 2021 using honeypots, shows that 70 percent of total web activity is currently bot traffic. With hackers increasingly deploying automated attack methods, default credentials are the most common passwords used by these bad actors, acting in effect as a 'skeleton key' for criminal access.
"On the list are the default Raspberry Pi credentials (un:pi/pwd:raspberry). There are more than 200,000 machines on the internet running the standard Raspberry Pi OS, making it a reasonable target for bad actors. We also can see what looks like credentials used on Linux machines (un:nproc/pwd:nproc). This highlights a key issue -- default credentials are still not being changed," says Brian Wagner, chief technology officer at Bulletproof. "Using default credentials provides one of the easiest entry points for attackers, acting as a 'skeleton key' for multiple hacks. Using legitimate credentials can allow hackers to avoid detection and makes investigating and monitoring attacks much harder."
A quarter of the passwords still being used by attackers today originate from the RockYou database leak of December 2009. These passwords remain viable, Bulletproof's penetration testers also attempt to use these passwords during testing as they still have a high success rate.
"Within milliseconds of a server being put on the internet, it is already being scanned by all manner of entities. Botnets will be targeting it and a host of malicious traffic is then being driven to the server," adds Wagner. "Although some of our data shows legitimate research companies scanning the internet, the greatest proportion of traffic we encountered to our honeypot came from threat actors and compromised hosts."
The full Bulletproof Annual Cyber Security Industry Threat report from the company's site. There's a list of the top default credentials being used below.
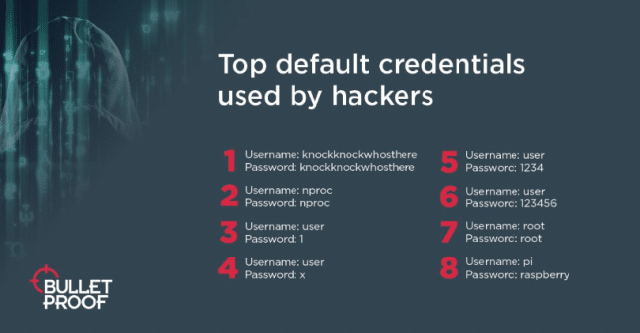
Image credit: Georgy Timoshin / Shutterstock
