
Medical device post market surveillance: Updates and trends
Post-market surveillance (PMS) is a critical part of pharmacovigilance, the science that focuses on the detection, evaluation, monitoring, and prevention of the unwanted effects of pharmaceutical products. It is vital in ensuring the safety and effectiveness of medical devices.
With the crucial role PMS plays in the healthcare industry, it merits the attention of patients, device manufacturers, and regulators. There have been developments involving or affecting post-market surveillance that needs to be highlighted because of their far-reaching consequences.

Adios, Microsoft Office 2013 support: What IT pros should know for migrations
It always sounds dire. "After five years of mainstream support, and five years of Extended Support, Office 2013 will reach the End of Extended Support on April 11, 2023," warns Microsoft. "Per the Fixed Lifecycle Policy, after this date security updates for Office 2013 will no longer be available."
At the end of support, the official statement continues, "Microsoft won’t provide any new security updates, and the continued use of Office 2013 after April 2023 may increase your organization’s exposure to security risks or impact your ability to meet compliance obligations." And dire it can be.

The dark data challenge
It is estimated that by 2025, the annual global data consumption will amount to 181 zettabytes -- over ten times more than in 2015. Does it mean we will make ten times better-informed business decisions? Most likely not, and the reason is simple: according to different sources, 75 percent or more of the data companies collect lurks in the dark.
'Dark data' is the vast amount of information collected by businesses but never analyzed or used. It can be web and app logs, email correspondence, visitor tracking data, the information generated by IoT devices, etc. Nowadays, every business activity is recorded somehow. Most of this data is unstructured and gathered in different formats. This cornucopia of information has to be processed, stored, secured, and maintained. Instead of increasing ROI, it increases noise, hidden costs, and safety issues since companies are legally responsible for all the collected data, even if they don’t use it.

How the tech industry can tackle the e-waste crisis head on
The success of the technology industry has been built on its constant innovation, always seeking out and creating products that are 'quicker' or 'more powerful' or 'sleeker'. However, as a consequence, there has been an elephant in the room growing for some time -- one that is yet to be tackled and taken seriously. That elephant is the mountain of electronic waste (e-waste) that continues to pile high every year.
With our tech consumption now comprising of everything from smartphones to tablets, from laptops to smartwatches, we as an industry bear a responsibility to manage the eventual waste these products create. Currently the amount of e-waste we generate rises by 347 million metric tonnes each year, and only 17.4 percent of it is known to be collected and properly recycled. To reverse the considerable environmental damage created by the IT industry, we need to change how we procure IT.

Leaked: How to install Android 13 in the stable version of Windows 11
It’s official: Android 13 has now been introduced to the Windows Subsystem for Android on Windows 11. The thing is, it’s only available to Windows Insider Program members (who also got special access to Microsoft’s Windows 10 22H2 preview build last summer). The Android update for WSA is available and accessible for users running Version 22.11.40000.11.0 and can be updated from the Microsoft Store app.
The update includes performance and reliability improvements such as boot speed, clipboard stability, mouse click input, app resizing, jump list entries, and media files. But you don’t need a Windows 11 Dev Channel or Beta build installed on your computer to upgrade the Windows Subsystem to Android 13 to try these features.
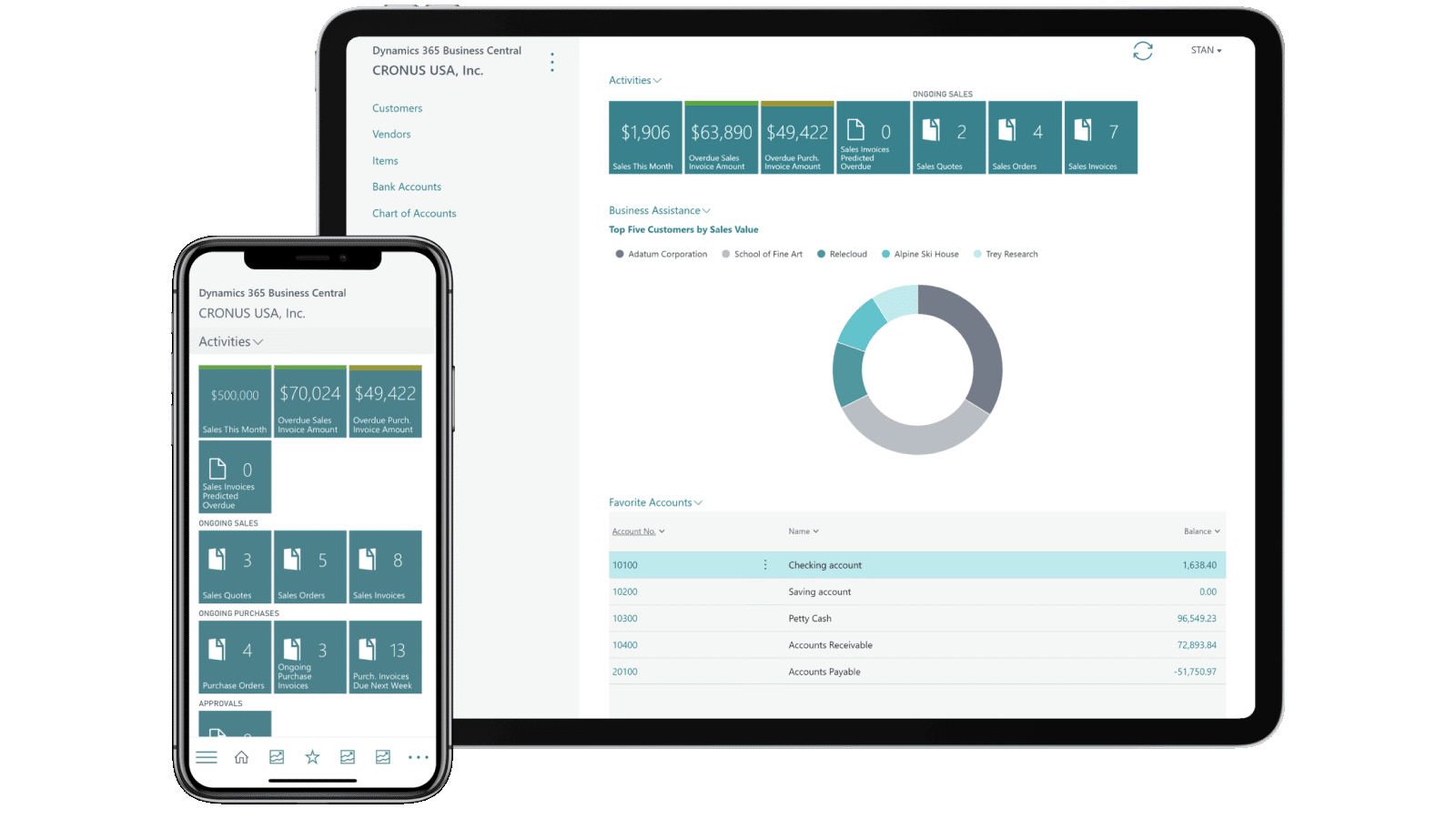
Unlocking productivity and uplifting efficiency with Microsoft Dynamics 365 Business Central
Microsoft Dynamics 365 Business Central holds the key to unlocking efficiency and productivity in the workplace. With improved processes at the forefront of business objectives, Dynamics 365 Business Central is the necessary solution for automating and streamlining operations.
Digitization has taken hold of our day-to-day lives and businesses. The technologies we now have access to allow us to flourish like never before -- when understood and used properly. While this may be overwhelming at times, it should be looked at in a positive light.

2023 needs to be a year of unification for cybersecurity
The past twelve months have been tough for a lot of organizations. From inflationary pressures to fears of a global recession, many economists have made pessimistic predictions about the year ahead. As a result, controlling and reducing costs is likely to be the focus for many companies in 2023.
Yet despite these economic stresses, IT spending has continued to rise. Gartner has estimated businesses spent around $4.5 trillion in 2022, up 3 percent year-on-year. While part of this spend is driven by digital transformation and the adoption of new technologies, a good part comes from unexpected expenses - especially when it comes to cloud where businesses can easily incur heavy costs without realizing it. Research finds that 80 percent of organizations lack awareness of how best to manage cloud computing, leading to overspending of between 20-50 percent.

The challenges for cyber resilience in 2023
Given we've all been told that it's inevitable that we'll get hacked, or at the least we need to assume that we will, what does this mean for businesses? It's clear that investment in cyber security measures isn't slowing down the attacks, and in 2023 it feels like there's been a significant increase in reported cyberattacks already. And we've only just hit February!
It would also appear that cyber attacks are becoming more sophisticated and technologically advanced. Fundamentally, you can't prevent a member of your team from clicking a phishing link, and the attack surface remains expanded due to the current hybrid working arrangements in place at most companies. So, if we are being told to expect an attack, does this shift the emphasis from prevention and defense, onto preparation and response? How would you recover your business?

Tips for overcoming challenges in a talent-constrained recession
The new year began with a curveball. Normally, when economic troubles occur, high unemployment follows. That’s not the case this time around: there are plenty of jobs that still need filling. This has created a rare talent-constrained recession, leading analysts such as Forrester to encourage IT leaders to maintain employee numbers.
This is especially true of companies that have committed significant resources towards creating a positive employee experience. In doing so, they’ve been able to attract candidates and retain skilled personnel. By taking a step back, a hard-earned reputation is tarnished and a useful recruiting tool diminished. The following takes a look at talent issues in the year ahead accompanied by some tips to overcome them.

How can SaaS give banks a competitive edge over BaaS users? Anyone? Anyone?
Core banking technology moves pretty fast. If you don’t stop and look around once in a while, you could miss out…
The reduced cost of fintech, and increased functionality of cloud-based "as a service" models can reduce the number of applications a bank is running by 30 to 40 percent, and the cost of ownership by 15 to 20 percent, when compared to traditional financial services IT infrastructure.

The ABCs of cybersecurity in 2023: Autonomy, BOMs, CaaS
Another year on the calendar, another guarantee that the technology on which we are so reliant will demonstrate new and largely unanticipated consequences. Perhaps nowhere is this clearer than in the world of cybersecurity. Let's take a brief look at three themes of cybersecurity predictions for 2023.
A is for Autonomy. The automobile industry is the very first thing we think of when we hear "autonomy," and there is no denying the promise of fully automated smart vehicles and how they can improve logistics, personal transport, and last-mile delivery. Through a darker looking glass, while we've seen proofs-of-concept in the past demonstrating unauthorized control of a moving vehicle, look for exploits relating to vehicular data: deliberate obfuscation of real-time geolocation coordinates and tampering of previously recorded data will surface as new areas of mischief for researchers and criminals alike.

Why companies must act now to reduce the cost of delivery
Seventy-one percent of logistics companies in the U.K. saw an increase in transportation costs in the first quarter of 2022 when compared to the same period in 2021. Forty percent of companies surveyed reported that the costs had risen by nearly 25 percent.
Enterprises are battling rising shipping costs in a hyper competitive market with an eye on providing end users with top-class consumer experiences. It’s a balancing act that leaves companies walking on a tightrope, trying to juggle between cost and consumer expectations.

How businesses can overcome IoT device firmware skills shortages
In recent years, the Internet of Things (IoT) has become an increasingly important area for businesses as more and more companies look to connect their products and services to the internet to deliver new experiences and unlock new revenue streams and capabilities. In Eseye's Annual State of IoT Adoption survey, over three-quarters (76 percent) of respondents said that IoT is a priority for their business in the next two to three years.
However, the design of hardware, firmware, and coding connectivity management software into IoT devices are all highly specialist areas. These three core components require significant specialized knowledge and expertise. A considerable skills gap in the industry makes it difficult for businesses to successfully design, develop, and deploy IoT estates.

Why BYOD could be the key to increased business productivity
A 'work device' isn’t what it used to be. Employees are no longer restricted to a single, company-issued device. Instead, they move between devices based on task, time of day, and location. One minute, they might be working at a desk on a Mac, while the next they are on the move, staying productive from an iPhone.
Research has shown that employees highly value the ability to choose which device(s) they use. In fact, 87 percent of respondents in an independent global survey, conducted by Vanson Bourne in 2021 said choosing their work device was important to them, and 89 percent said they’d even be willing to sacrifice part of their salary to be empowered to choose their own technology.

Cloud security: Top trends and threats to watch out for in 2023
As security professionals assess the cloud security challenges that lie ahead for the coming year, one thing is certain. Threat actors will continue to double down on their efforts, utilizing new techniques and refining pre-existing methods as they extend their ever-growing toolbox.
To help enterprises stay ahead of the game, our security research team has highlighted some of the top trends and attack vectors cloud security teams can expect to encounter in 2023.

