
The latest Windows 11 Release Preview build includes new features not found in Canary, Dev or Beta releases
Ordinarily Microsoft uses the less stable Windows Insider channels to try out new Windows 11 features -- something the company reiterated when it launched the ultra-cutting edge Canary channel.
But this week saw the release of a new build of Windows 11 to the Release Preview channel, the channel which is the final stage of testing before a build gets full public release. And this time around, things were a little different because the Release Preview build includes brand new features that have not been seen in other builds -- including notifications for Microsoft accounts in the Start menu.

New solution helps enterprises manage cloud assets
As organizations turn increasingly to the cloud they face the challenge of understanding not just the cost but also the value of their operation.
To help organizations maximize business value from their technology investments, Flexera is launching a new solution that strengthens an enterprise's FinOps and cloud central teams, while allowing the convergence of IT asset management (ITAM) and FinOps.
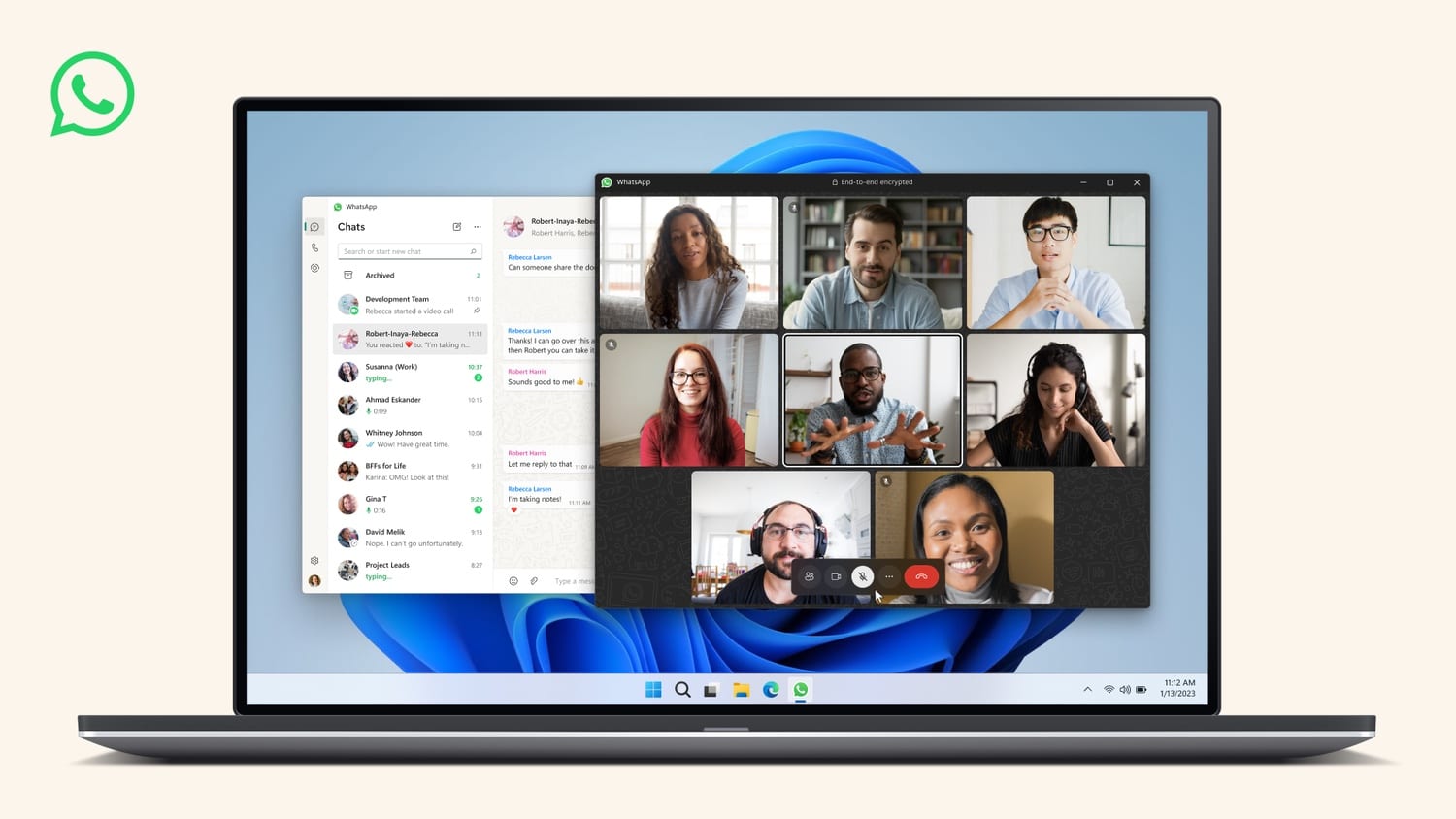
There is a new, faster version of WhatsApp for Windows with improved calling features
While WhatsApp is most commonly used on mobile devices, growing numbers of users are adopting the desktop version of the app. Meta has just announced the release of a significantly improved version of the Windows app.
Speed is a key upgrade here, with load times being reduced, but there are also feature improvements. The latest version of WhatsApp for Windows now supports larger group video and audio calls.
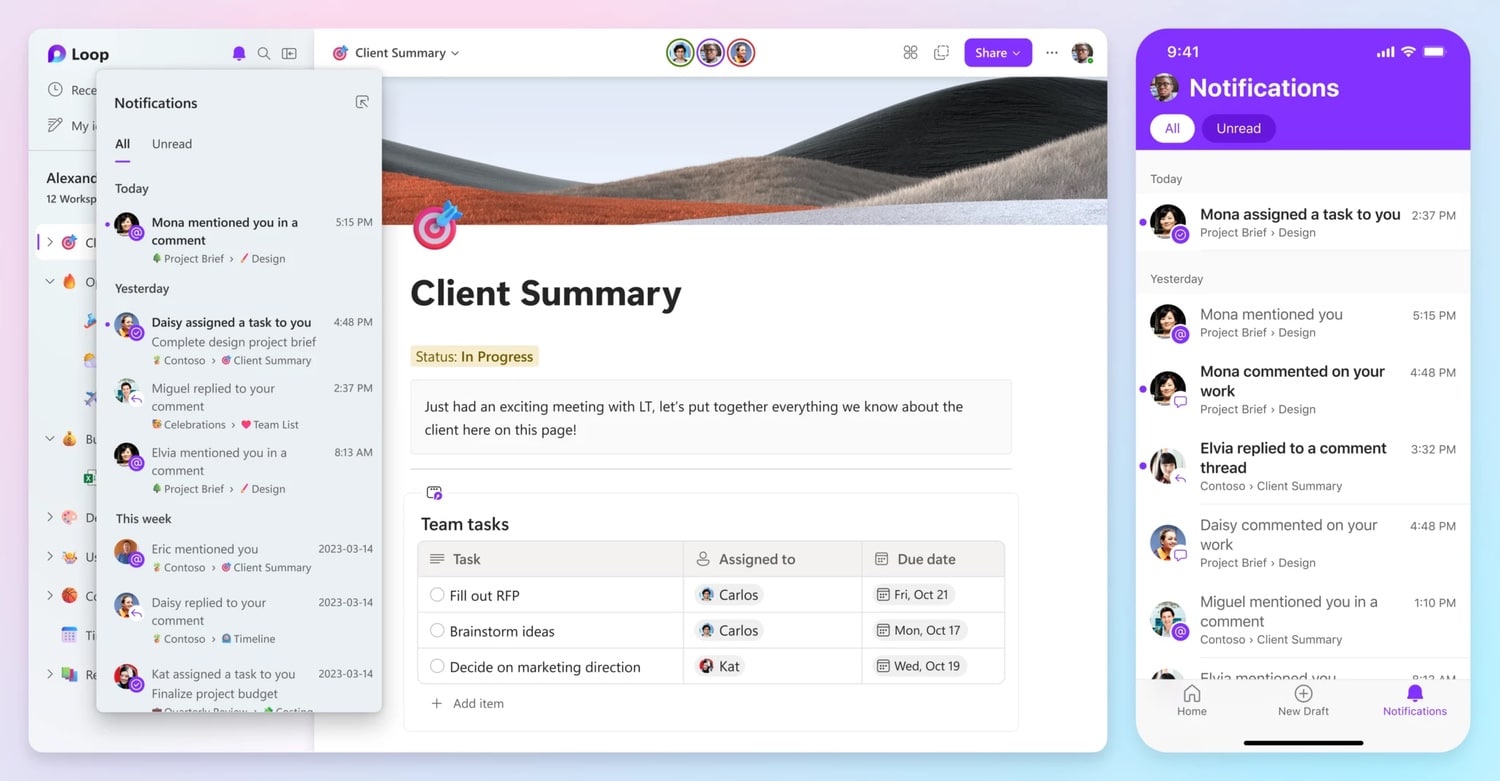
Collaborative working app Microsoft Loop is now available in public preview
Microsoft has announced the availability of a public preview of its new collaborative working app, Loop. The public launch follows a period of private previews with enterprise customers.
Microsoft Loop is available on the web, as well as for iOS and Android, and it allows teams to work together in shared workspaces that integrate neatly with Microsoft 365 apps. The app competes with the likes of Asana and Notion and has been in development for a couple of years. As you might expect, there is a dash of AI thanks to Microsoft 365 Copilot's support for Loop.

Microsoft panics Windows 11 users with 'Local Security Authority protection is off' warning
Users of Windows 11 have been concerned by the appearance of a message that reads: "Local Security protection is off. Your device may be vulnerable". Microsoft is blaming a recent update (KB5007651) for the warning which implies that an important security feature has been disabled.
The issue affects Windows 11 version 21H2 and 22H2, and those hit by the message have been left confused about what they need to do. So what is going on?

BenQ PD2706UA is a 27-inch 4K UHD professional designer monitor
BenQ has established a reputation for producing high-quality monitors that cater to the needs of various users, and the PD2706UA is no exception. This monitor has been designed specifically for creative professionals who require the best possible color accuracy, resolution, and viewing angles.
The PD2706UA is a 27-inch monitor that boasts a QHD resolution of 2560 x 1440. The display is made with an IPS panel that provides excellent color reproduction and wide viewing angles. This makes it ideal for professionals who require accurate color representation, such as graphic designers, photographers, and videographers.

GNOME 44 'Kuala Lumpur' is finally here
There are many great desktop environments for Linux, such as Cinnamon, KDE Plasma, and MATE to name a few. With that said, only one can be the best, and that is obviously GNOME. Look, folks, there's a reason Canonical uses it as the default DE for Ubuntu -- it's that good.
If you are a GNOME fan, I have some extremely exciting news. You see, as of today, GNOME 44 is officially here! Named "Kuala Lumpur," this version of the desktop environment is loaded with new features. Most notably, the Software app has received several enhancements, including an improved user interface and better error messages. You can read the full release notes here.

Get 'Hands-On Software Architecture with Java' (worth $41.99) for FREE
Java, the most widespread technology in current enterprises, provides complete toolkits to support the implementation of a well-designed architecture.
Hands-On Software Architecture with Java starts with the fundamentals of architecture and takes you through the basic components of application architecture. You'll cover the different types of software architectural patterns and application integration patterns and learn about their most widespread implementation in Java.
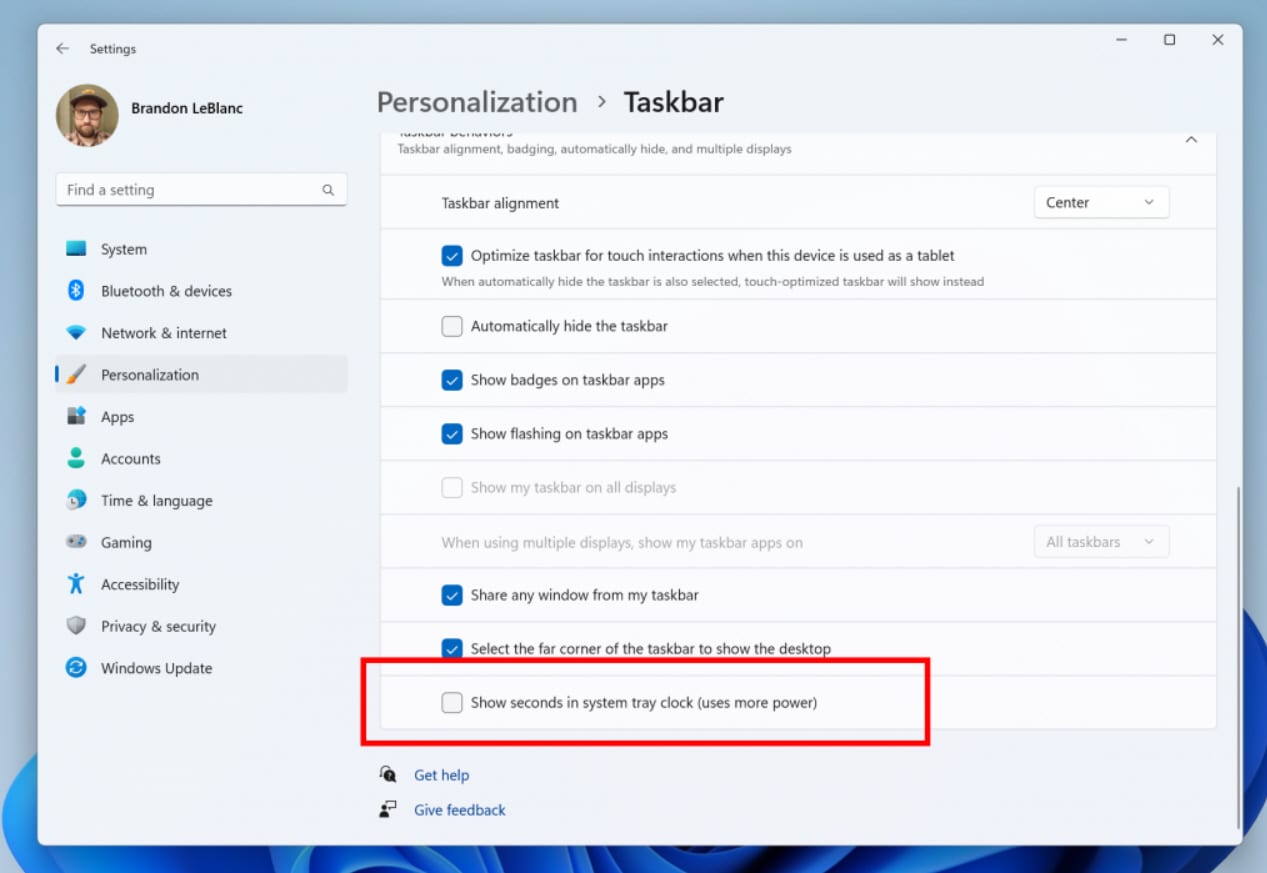
Windows 11 Build 23419 can show seconds in the system tray clock -- but the new feature comes with a warning
It’s business as usual for Windows 11 Insiders in the Dev Channel as Microsoft today releases a fresh test build for the new operating system.
Windows 11 Build 23419 comes with several new features, including introducing the ability to show seconds in the clock on the system tray. This welcome-sounding addition won't appeal to everyone, however.

IT in 2023: Security, cloud and more
Given the ever-changing trends in cloud computing, security, and more, it can be difficult to plan for the road ahead. However, anticipating new developments, both within your organization and the wider industry, is vital if you want to stay prepared and maximize ROI.
Data is one of a business’ greatest assets, and its role, size and value is only going to increase in 2023 and beyond. Cybersecurity Ventures suggests total global data storage is expected to exceed 200 zettabytes by 2025, with a ransomware attack precited to impact a business, consumer or device every two seconds by 2031, properly securing your data is paramount.

The risk and reward of ChatGPT in cybersecurity
Unless you’ve been on a retreat in some far-flung location with no internet access for the past few months, chances are you’re well aware of how much hype and fear there’s been around ChatGPT, the artificial intelligence (AI) chatbot developed by OpenAI. Maybe you’ve seen articles about academics and teachers worrying that it’ll make cheating easier than ever. On the other side of the coin, you might have seen the articles evangelizing all of ChatGPT’s potential applications.
Alternatively, you may have been tickled by some of the more esoteric examples of people using the tool. One user, for example, got it to write an instruction guide for removing peanut butter sandwiches from a VCR in the style of the King James Bible. Another asked it to write a song in the style of Nick Cave; the singer was less than enthused about the results.

New solution helps to visualize cloud-native app risks
With more and more organizations turning to the cloud and cloud-native application development, AppSec teams face a mounting challenge to keep pace with their development counterparts.
To address this, Backslash Security is launching a new solution to provide unified code and cloud-native security by correlating cloud context to code risk, backed by automated threat modeling, code risk prioritization, and simplified remediation across applications and teams.

Dark web intelligence is critical to defending the enterprise
A new survey of over a thousand CISOs from large enterprises in the US and UK, finds that 93 percent are concerned about dark web threats and 72 percent believe that intelligence on cybercriminals is critical to defending their organization.
The report from Searchlight Cyber looks at how CISOs are gathering data from the dark web to improve their security posture.

The role of service mesh in application security [Q&A]
As organizations embrace cloud-native development, they are building new types of applications and microservices that are easier to scale and add more business value.
But the growing adoption of microservices has introduced new security risks because microservices and modern applications contain more 'pieces' that increase the attack surface.

Microsoft is changing the release schedule for Windows update previews
For the majority of Windows users, OS updates are just something that happens in the background. But for anyone who keeps a closer eye on things, the monthly Patch Tuesday is an important day when they know the latest "stable" versions of Windows updates are released.
For some time, however, Microsoft has released preview versions of updates ahead of the wider rollout, giving eager Windows users the chance to grab the latest fixes faster -- and also serve as beta testers. Now the company has announced that a new schedule for non-security preview releases is to be used from next month.
