
Grab your popcorn, AMC lands on Roku
AMC doesn't always show the latest films, but it does land some big names from Hollywood, and of course it's responsible for producing some excellent original content. It's become a go-to channel for surfers looking for something to watch. Now the entertainment network is coming to that tiny set-top box in your living room.
The channel debuts just in time for the mid-season launch of Fear the Walking Dead. If you're into zombie apocalypses then that's certainly for you.

JixiPix's Sprektrel Art is free until 29 August
Spektrel Art is a smart Windows and Mac app/ Photoshop plugin which transforms images into digital works of art -- and it’s available for free until August 29th.
What does it do? The developer attempts to explain, saying it’s "an extravagant otherworldly display of undulating movement that glimmers and gleams with intersecting lines of tapered light". Umm, great.

Latest Windows 10 update breaks PowerShell DSC and implicit remoting, but a fix is coming
While mandatory updates mean Windows systems are kept safe from threats, the downside is if a bad update makes it through testing it gets pushed out to everyone.
This is a problem we’ve seen several times already with Windows 10, and the latest update, KB3176934, is another perfect example of this.

Linux celebrates its 25th birthday today! But can it survive another 25 years?
Today, Linux celebrates its 25th birthday. This is certainly cause for celebration in the open source community. Surprisingly, however, after all this time, many people don't understand that Linux is simply a kernel, and not an operating system. Yes, it is used as a component of operating systems, such as Ubuntu, Fedora, Android, Tizen, and more, but a kernel alone does not an OS make.
Linux's longevity is a testament to the open source community as a whole, and not just one man, such as Linus Torvalds. True, he invented the kernel back in 1991 and maintains it to this day, but if he didn't have help along the way, it would have died long ago. Speaking of death, how much time does Linux have left to live? Some folks wonder if the kernel could meet its demise at the same time Torvalds does (or shortly thereafter). In other words, does the man have too much control with no real contingency plan?
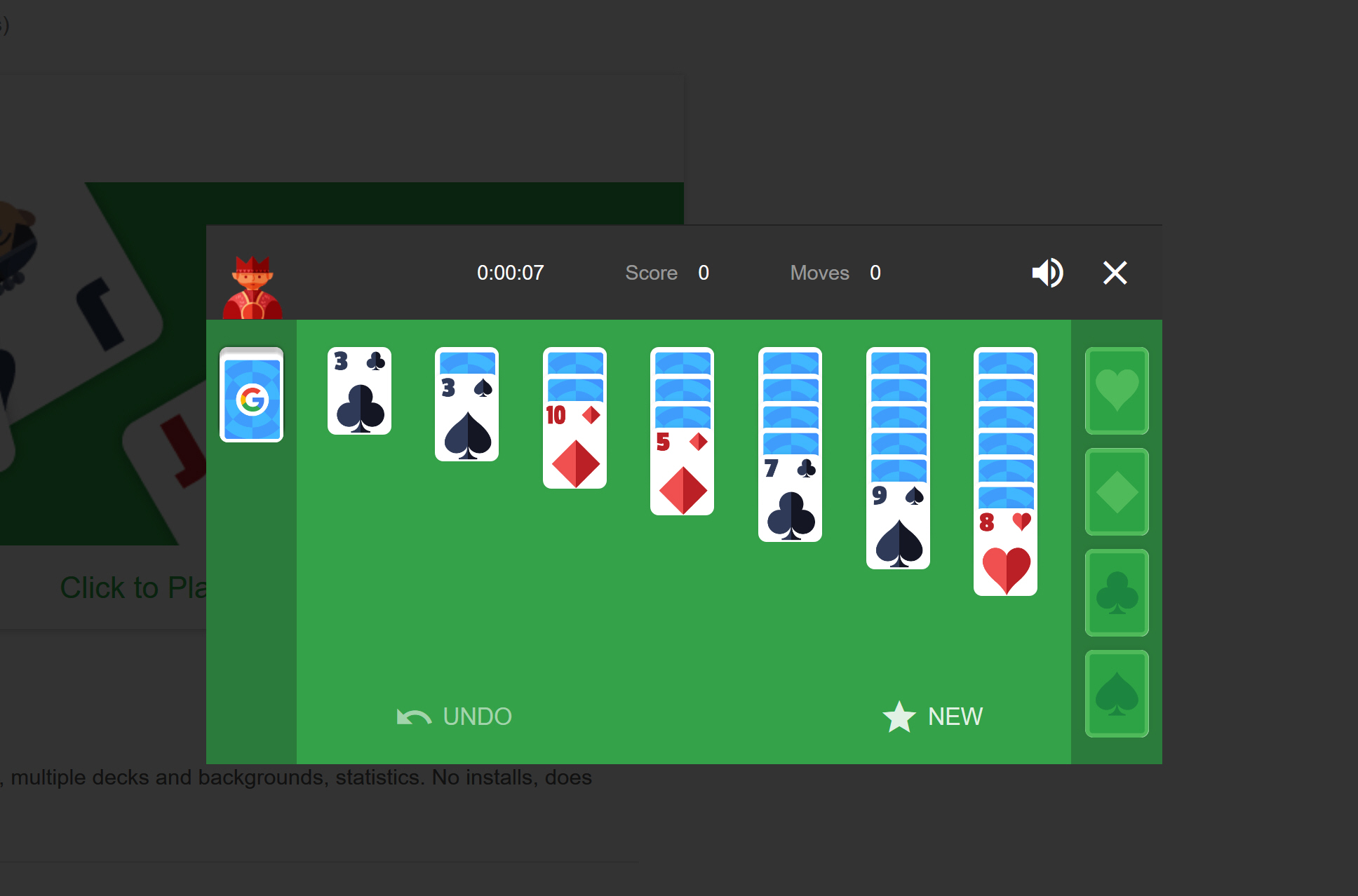
You can now play games directly in Google Search
When you go to Google it's usually to search for something, but from today you'll also be able to play games like solitaire and tic-tac-toe there -- both on the desktop and in the Google app.
And that's not all. You'll also be able to settle arguments with a toss of a coin, and hear the sounds of your favorite animals.

The self-driving car is old enough to drink and drive
Twenty-one years ago, when we were shooting Triumph of the Nerds, the director, Paul Sen, introduced me to his cousin who was working at the time on a big Department of Transportation research program to build self-driving cars. Twenty-one years ago! Yet what goes around comes around and today there is nothing fresher than autonomous cars, artificial intelligence. You know, old stuff.
As you can see from this picture, driverless cars were tested by RCA and General Motors decades earlier, back in the 1950s.

One in four breaches in the financial sector are from lost or stolen devices
New research from data protection company Bitglass into breaches in the financial services industry reveals that leaks nearly doubled between 2014 and 2015, and that lost and stolen devices are the most common cause.
While hacking remains a major fear, only one in five leaks were caused by it. Other breaches were the result of unintended disclosures (14 percent), malicious insiders (13 percent), and lost paper records (8.1 percent).

Ransomware: 3 seconds to encryption
Imagine how you would feel if everything on your entire PC hard drive was encrypted, and somebody was demanding a large sum of money from you to make it accessible? This scenario is exactly what happens to thousands of people every day when they are infected with ransomware, and it is essentially a digital hold up. Though your life is not in danger, you face the imminent threat of catastrophic consequences from the loss of irreplaceable data.
Much of the attention in the industry is focused on the damage caused by ransomware. The common belief is that most ransomware infections are caused by human carelessness, so there is no guarantee that you will never get infected. So the focus really needs to be about how to detect and respond to a ransomware infection.

Cloud platform lets marketers deliver personalized Google Ads
Google Ads has proved itself an effective tool for gaining new business, but it's a rather less useful way of targeting existing customers.
Now though, marketing cloud specialist Optimove is launching a new integration with Google Ads. This allows businesses to target existing customers with personalized ads on google.com and across the Google Display Network, based on recent and predicted behavior patterns.

Windows 10 Anniversary Update crashing when Amazon Kindles are connected
Windows 10 Anniversary Update has been causing problems for users in all sorts of ways. There have been reports of it freezing systems, and killing webcams.
Now owners of Amazon Kindles are reporting their PCs crashing when plugging in their devices via USB to charge them or transfer books.

iOS device failures overtake Android for the first time
In the ongoing smartphone performance and reliability battle, Apple has lost its leading position to Android for the first time in the second quarter of 2016.
Plagued by crashing apps, WiFi connectivity and other performance issues, the iOS failure rate more than doubled to 58 percent, compared to a 25 percent failure rate in the previous quarter, according to the research by mobile device diagnostics company Blancco Technology Group.
How the Industrial Internet of Things is set to change the world
We're all aware of the Internet of Things and its likely effect on our homes, but there's another side to it which is its impact on industry.
Electronics supplier RS Components has put together an interactive graphic looking at how the Industrial IoT is going to change everyday functions from streetlighting to agriculture.

Will we ever be able to go entirely laptop free?
In a world that is fast producing new technologies every year, it’s interesting to read what technologies are reported to being on the decline. For example last month, a study from comScore has shown that desktop browsing is fast becoming a thing of the past.
In the article, from April 2016, it was stated that over the past four months, desktop use for Internet browsing has been consistently below the recorded amounts for the same time period last year. Alongside these figures, it is also stated that desktops are losing share to mobile, which now accounts for 65 percent of digital media time spent. As a result, mobile devices seem to be replacing the traditional PC -- in the age of being connected anywhere and at any time, this is hardly surprising, but what lies ahead for the other devices we hold dear?

The essential 2016 back-to-school technology shopping guide
Holy cow. The end of August is approaching, signaling the end of summer vacation for many students around the USA. This is the time when those learners, and -- depending on student age -- their parents, begin shopping for back-to-school items.
If you aren't sure what to buy, I am going to help you out. Keep in mind though, BetaNews is a technology site -- I won't be advising on pens, pencils and binders. What I will help with, however, is smartphones, tablets, laptops, and more.

Amazon 'Kindle Reading Fund' makes books more available to those without access
The ability to read is something many of us take for granted. At a young age, you probably had tons of books in your homes and schools, enabling you to learn to both read and write. Believe it or not, not everyone has access to books. Isn't that sad?
Luckily, Amazon is looking to change this. Today, the famed retailer launches a new literacy initiative called 'Kindle Reading Fund". The company is aiming to get books into the hands of those who don't normally have access. How? It will be distributing free Kindle e-readers, Fire tablets, and Kindle e-books to those that need them.



