
New business collaboration platform secures data with personalized cryptography
Data security is a big concern for both individuals and businesses. This doesn't only apply to the public face of a business, but to exchange of information and collaboration between employees too.
Canadian company Witkit is launching a new platform that allows the creation of teams and groups within industries, companies, and departments to tackle projects and solve problems collectively, with the safety and security of knowing their data cannot be breached.

How the 'Health of Things' could replace your trip to the doctors [Q&A]
One of the biggest trends of this year's CES was the "Health of Things", with wearable technology increasingly being connected to healthcare in order to enhance users' lives.
I spoke to health tech specialist Nudge about what exactly the "Health of Things" means to the general consumer and the impact it's having -- and will have -- on the tech and healthcare industries.

Federal cyber security rules should learn from industry guidelines
For many in the cyber security field, this year’s State of the Union speech was particularly notable, as information security took the spotlight alongside other major international and domestic issues.
President Obama said he would propose several sensible new security measures, including:

Smartphones: Apple ties with Samsung, Android still growing, Windows Phone still failing
Samsung is no longer the leading smartphone vendor. According to a new report from Strategy Analytics, Apple caught up with the South Korean maker in Q4 2014, thanks to a record number of iPhone shipments totaling 74.5 million units. The two players now share the top spot on the podium.
How did it come to this? Well, it's simple. Apple's shipments increased from 51 million units by 46.07 percent year-over-year, while Samsung's shipments decreased from 86 million units by 13.37 percent, each converging to 19.6 percent market share. Thanks to the strong performance shown by iPhones, iOS' market share rose also, to 19.6 percent from 17.6 percent a year prior, while Android's market share dipped slightly to 76.7 percent from 78.3 percent.

A single DDoS attack could cost over $400,000
One of the major worries for online businesses is being subject to a DDoS attack. As well as damaging reputations these can have a serious effect on finances too.
According to a new study by Kaspersky Lab the average cost of a DDoS attack ranges between $52,000 and $444,000 dollars depending on the size of the business.

Google faces a Sisyphean task to remove terrorist content from YouTube
Too much content is uploaded to YouTube for Google to be able to effectively police users' videos. This is what the search giant said in response to calls for more to be done to counter terrorism-related content on the video network.
Online censorship versus the right to freedom of speech is a battle that has waged online for some time now. Some parts of the world are more prone to censorship than others, and it's an argument that bubbles up from time to time. The debate usually centers around the moral rights and wrongs of censoring content, but the issue of practicality occasionally rears its head as well.

Intel's 5th generation Core vPro processors now available for enterprise and enthusiasts
Whether you are a home or business user, there is probably an Intel processor in your PC or workstation. Let's be honest, it has become a one-horse race; Intel is really the only player in the processor game nowadays. True, AMD is still producing chips, but the best value is Intel's "Core" line -- great performance paired with impressive battery life and temperatures. Sadly, AMD has nothing to compete with Intel's 14nm 5th generation Intel Core processors.
Today, Intel furthers its lead against competitors by announcing the immediate availability of the vPro-enabled 5th generation Intel Core processors. These chips are aimed at business users and workstations, but enthusiast home users will be interested in these chips too. The new features should allow workers to be more productive, while working smarter instead of just harder.

Monitor HTTP and HTTPS traffic with FiddlerCap
If you’re trying to diagnose web problems, or you’re concerned about security, then it can sometimes be useful to watch your PC’s HTTP and HTTPS traffic.
Fiddler is one possible solution, an industrial-strength web debugging proxy with a lengthy feature list and enough monitoring power to satisfy the most demanding of developers.

Employees can put corporations in danger for little money
The recent breaches of large corporation internal systems has lead some security analysts to believe indifference from employees is a key factor, rather than rogue nations attacking the private sector.
Identity management firm SailPoint claims employees would be willing to sell corporate information like passwords for as little as £100 and routinely use the same passwords for almost all applications.

Microsoft's decision to ditch Surface is a long-overdue mercy killing for Windows RT
For too long it was the metaphorical unwanted litter of kittens tied in a sack just waiting for someone to ditch it in the river. Windows RT is dead, having enjoyed a cancer-ridden 'life' for longer than many people expected. Microsoft announced that it is no longer going to manufacture Surface devices, all but signing the death warrant for Windows RT.
Hear that sound? No? That's the sound of everyone caring about it. To be fair, the writing has been on the wall for quite some time. Windows RT was always the sickly twin sibling of Windows 8 and now Microsoft has done the decent thing. It might not quite have delivered the lethal shot to the brain yet, but the gun has been cocked. And not before time.

Internet censorship: The worst offenders
In the UK, policies that restrict the flow of information across the Internet are generally met with outcry and consternation for contradicting our fundamental right of free speech, but for many individuals widespread Internet censorship is the norm.
However, online censorship is much more pervasive than one might initially think, with Ethiopia, Russia and even the UK currently listed as Enemies of the Internet by the French non-governmental group Reporters without Borders (RWB).
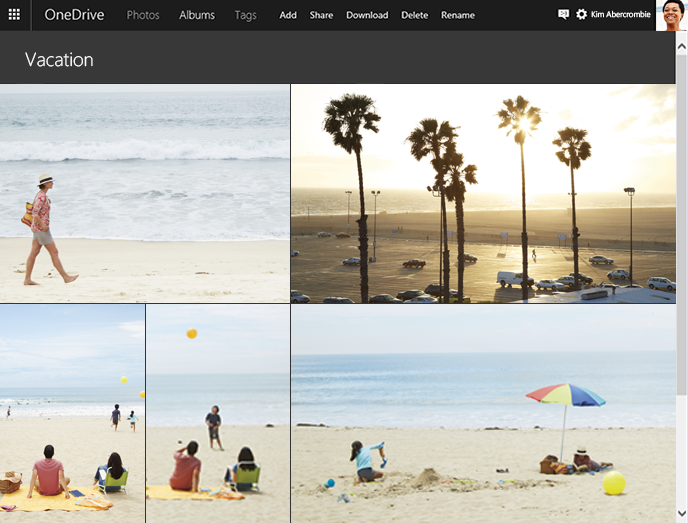
Microsoft OneDrive is now the place for your photos
Microsoft wants its cloud storage service to be the best place for all of your photos, and so is debuting new ways to import, organize, find, improve, and share them.
According to Douglas Pearce, OneDrive’s Group Program Manager, major updates coming over the next couple of weeks include: "the ability for customers to curate photos from their phone, desktop and inbox quickly and simply; a new feature that allows you to view, manage, and share photos with Albums; and finally, through a partnership with Bing, customers can now search for their files and photos in a new and exciting way!"

Pandora achieves 50 billion 'thumbs' -- users vote on what they like and hate
Listening to streaming music services can be a very rewarding experience. Unlike listening to vinyl or a CD, which can be a very private experience, streaming can feel more communal. In other words, it can provide the user with the feeling of a shared experience.
Pandora is very successful in this regard, as it allows users to vote with a thumbs up or down to make their voice heard. Ultimately, this allows the service to customize the listening experience, but more importantly, it supplies the company with valuable insights. You see, Pandora is tracking all of the user data on thumbs up and down, and using it for analysis. The company has now received over 50 billion thumbs (both up and down) -- impressive. To celebrate, it is sharing an infographic that tells the story of what music people respond to.

Xiaomi: Hand over your iPhone, get a Mi Note flagship for free
Xiaomi is going hard against Apple in 2015. CEO Lei Jun recently gave several shoutouts to the Apple's inferior design quality on the iPhone 6 when compared to the Mi Note.
And now the next step in the battle will focus on swapping iPhones for Xiaomi Mi Note and Mi Note Pro at no extra cost, according to a new report citing Xiaomi's media development director.

It's Data Privacy Day and Facebook knows you're reading this
A new global study conducted by Microsoft across 12,000 people shows that most internet users still don't believe they're aware of all the data that's being collected about them.
For example, Facebook, Twitter and Google+ know you've read this page, as they track your visits to any website with a 'Like', 'Tweet' or '+1' button, whether you click that button or not. Information gathered can include anything from your IP address and general geography, to insights into your age, gender, income, hobbies, health status and financial situation, by way of your browsing and purchase history.