
How to get an extra 15 GB of OneDrive storage for free
There is plenty of competition in the cloud storage space, but, unfortunately, for the most part any massive changes are limited to paid plans. They get bigger, they get cheaper, but the free tier, which most users get first, remains largely as limiting as it has always been. Sure, we get a couple of extra gigs for free here and there, but it's all smoke after all, meant to lead us right to the money grabbers. (And who could blame providers for trying to make money?)
Now, Microsoft is doing something rather interesting, as it gives OneDrive users nearly twice as much storage in the free plan, bumping the limit from a so-so 15 GB to a respectable 30 GB. The reason? Well, it's a damn clever one -- the extra freebie is meant to help Apple users who are having trouble with iOS 8 upgrades due to low available storage. Because this is an oft-discussed issue, it is bound to generate some free advertising for Microsoft and OneDrive.

How to prepare your iPhone and/or iPad for iOS 8
The latest version of Apple’s mobile operating system is set to be released officially today.
Before you install it, it’s worth taking a few steps to make sure your device is ready for the update (and of course if it’s jailbroken, and you want to keep it that way, you’ll want to avoid updating until a jailbreak is made available for the new OS). Here’s what you should do in advance.

How to do the smart thing and migrate from Android to iPhone 6
For the majority of Android users, the idea of moving from a handset running Google’s mobile operating system to the iPhone holds zero appeal. But I did it last year, and I couldn’t be happier. For me, iOS is by far the superior operating system (and I use iOS and Android daily), and the iPhone is a great handset.
If you’re thinking of making the move from Android to one of Apple’s new sized-up iPhones (and you won’t regret it), the process is pretty painless and Apple has created a new support page explaining how to move your photos, music, documents, and more.

How to upgrade your iPhone 5s to iOS 8 now
Disclaimer: This is for educational purposes only, we do not recommend updating to iOS 8 before its official release (probably) on September 10. If you don't have a developer ID and install iOS 8 your warranty may be voided.
The iOS 8 release is likely to be announced alongside the iPhone 6 following Apple's trend of announcing devices on Tuesdays and releasing iOS updates on Wednesdays. A fairly safe bet would be that iOS 8 will be released on 10 September. But what if I told you that you could get iOS 8 on your iPhone 5s earlier than that?

Tired of privacy breaches? How to remove yourself from social networks
The leaking of celebrity photos which may have come from iCloud is just the latest in a series of high profile security and privacy breaches that are leading many people to question how safe their data is online.
For those who have decided enough is enough, secure transaction specialist Imprima has produced an infographic guide to "unfriending the internet" which covers how to take your personal profiles off the main social networking sites.

The top 10 security software design flaws and how to avoid them
It's a fact that most software has bugs of some sort when it gets released. More significant are fundamental flaws in the design, yet whilst bugs generally get fixed, design flaws are often overlooked.
In an effort to address this professionals organization IEEE is bringing together leading figures from Google, HP, Twitter and Cigital to form a Center for Secure Design group with the aim of tackling serious design flaws in software.
How to fix disabled audio in OS X 10.10 Yosemite [Update]
Apple launched, almost a week ago, the second public beta build of OX 10.10 Yosemite, which, among other improvements, includes a healthy dose of bug fixes. But, for some reason, the company has not yet addressed a glaring sound problem, where the audio stops working until a restart is performed. It is likely this occurs in the developer-only builds too. (It looks like this may even happen with the stable -- final -- version of the operating system.)
I am not alone in experiencing this problem, as I have seen other OS X 10.10 Yosemite users reporting the same issue with the built-in audio. In my case, after some testing, it appears that this issue occurs after my 2013 MacBook Air wakes up the built-in and external displays from sleep. (The sound also appears to have been disabled even after a clean install of the stable release; check the information pertaining to it at the end of the story for another solution.)

Enterprise mobility: How to choose the right strategy
Finding the ideal alignment and balance between hardware, software and employee preference has become the Holy Grail for those tasked with defining enterprise mobility strategy. BYOD delivered many great things, such as higher employee productivity and satisfaction. It also made IT managers rethink their strategies to make technology work for their organization in terms of mobility, security and management. Then COPE (corporate owned, personally enabled) came along, which promised to solve some of the problems that BYOD didn't, such as security. However, COPE also posed challenges of its own and is being followed now by CYOD (choose your own device).
With so many acronyms flying about, it might appear hard to know where to start identifying the best solution. However it would seem that 2014 has heralded the end for BYOD, with a recent report by analyst firm Gartner declaring its demise, stating, "There is no way for IT to assume full responsibility of securing and managing devices without ownership". Indeed, the acronym is now being translated by some as "bring your own disaster", suggesting it would perhaps be wise to learn from others' mistakes.
How to secure commercial online file sharing
Cloud-based file-sharing services benefit all types of businesses by providing easy, convenient access to information anytime, anywhere. With technology increasingly blurring the lines between work and personal lives -- often with the same platform being used in both worlds -- it can be easy to forget that work-related information often needs to be handled with greater care and a higher level of security.
If employees use personal accounts and free services designed for consumer use, in order to manage clients' documents, they could be putting your business at high risk for a security breach. This will become ever more important as the regulations around management of sensitive and private information get stronger and enforced more strictly. However, there are several simple steps companies can take to tackle these issues and keep business information protected.

How to avoid a big data nightmare
Big data is no longer just the domain of big companies. As the perception of big data moves from futuristic hype to real-world opportunity, the promise of improved decision making, increased operational efficiency and new revenue streams has more organizations actively engaging in data analysis projects than ever before. That no longer only means more enterprise organizations, either. Midmarket companies are jumping on the big data bandwagon in a major way.
In fact, a recent survey by Competitive Edge Research Reports indicates that an astounding 96 percent of midmarket organizations are either already in flight with a big data initiative, or plan to start one in the next year. That's a whole lot of companies whose big data projects are either going to sink or swim in the very near future.

How to overcome the main challenges faced by IT departments
IT departments always used to be the butt of jokes. Perhaps this was because being nerdy and geeky wasn't hip and cool until social media took the world by storm and made multimillionaires out of self-confessed geeks like Facebook's founder Mark Zuckerberg and Twitter co-founder Biz Stone.
Technology firms like Apple and Google are partly responsible for making consumer IT cool, but the IT department is still often viewed as an impenetrable world only inhabited by geeks and boffins that are often arrogant, rude and obstructive.
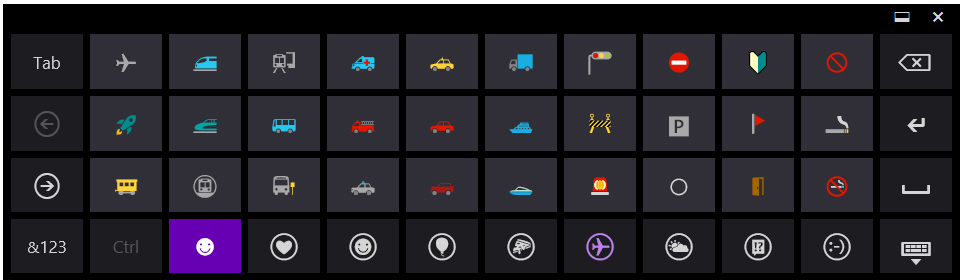
How to access Windows 8.x emoji on a desktop PC
The touch screen keyboard available on Windows 8.x tablets -- like Microsoft Surface, for example -- gives you access to a wealth of emoji you can use in chats, emails, comments and so on. As well as the usual smileys, there are hand signs, hearts, cartoon characters, vehicles, weather symbols, and many more to pick from. Just select the character set you want at the bottom of the keyboard.
If you’re not using a touch screen device, but still want to access these characters you can.

How to protect your company data without inspecting SSL
Since the start of this year, it has felt like Armageddon within the cyber-security arena. Attacks are coming thick and fast, with resultant breaches hitting the headlines. Advanced malware -- it’s clever, almost always relentless, and it's increasingly encrypted!
In every organization there are two types of traffic -- inspected traffic and non-inspected traffic. There’s a reason for that. Well, actually, it’s one of three reasons: performance, scalability or cost.

How to keep your smartphone safe in the age of industrialized hacking
The use of mobile devices for work purposes is on the up, creating all sorts of new opportunities for the modern worker. In fact, according to a recent report from Juniper Research, the number of employee-owned smartphones and tablets in the work place could exceed one billion by 2018. It is now possible to access your company resources whenever you need to, whether working from your living room, sat in a restaurant or chilling in the park.
When you do need to work from the office, smartphones and tablets are often a lot more convenient to use than a bulky laptop. The benefits of having a computer that fits in your pocket or bag are hard to ignore, especially for people who are always going from meeting to meeting.

How to prepare a business for the Internet of Things
If you follow what's trending in technology, you will by now know that the Internet of Things (IoT) is expected to create new possibilities for connected technologies, along with IT resource churn, as companies struggle to securely connect a deluge of devices, sensors and objects to the corporate network. According to IDC, there will be more than 212 billion devices connected to the web by 2020, including over 30 billion connected autonomous things.
The IoT hype focuses on how Internet-connected cars, homes, offices, appliances and gadgets will transform how we work, play and live; sensors in water bottles, web-enabled tennis rackets and every kind of conceivable wearable will capture the spotlight.
