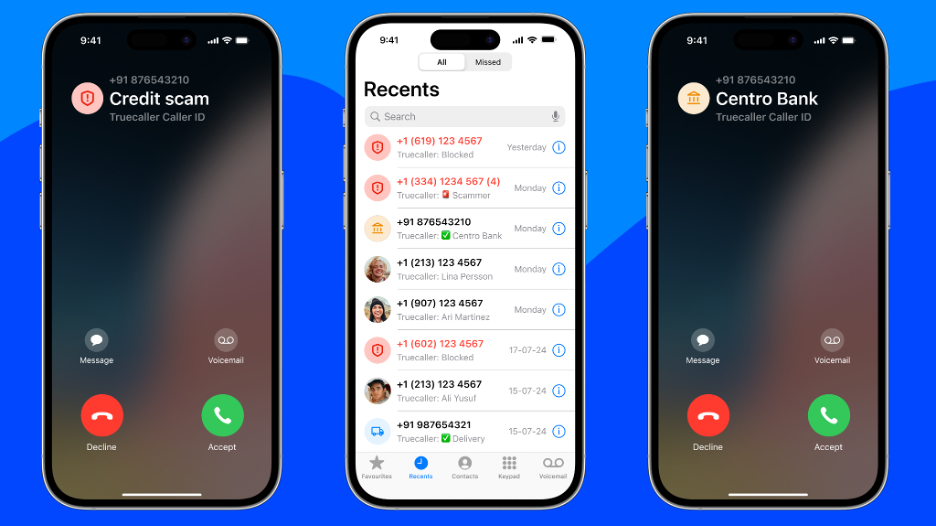
Truecaller brings Android-level spam blocking and caller ID features to iPhone
Truecaller, the popular app known for tackling spam and scam calls, just made a huge announcement for iPhone users. With its latest update, Truecaller is finally bringing the same spam-blocking and caller ID features that Android users have enjoyed for years to Apple’s platform. If you’ve ever felt like you were missing out on some of Truecaller’s best tools, that ends now.
This update is powered by Apple’s new Live Caller ID Lookup framework, a tool specifically built for apps like Truecaller to handle caller ID securely. Using advanced encryption, this framework ensures that privacy is a priority while still allowing real-time caller identification. This a pretty big win for users tired of unknown calls.

The potential opportunities and challenges of decentralized identity in mitigating AI threats
In an age where cyber threats are becoming increasingly sophisticated, the management and verification of digital identities are at a critical juncture. As various sectors rapidly evolve, decentralized identity (DCI) systems emerge as a revolutionary approach to managing and verifying user identities. These autonomous systems promise to change how we access and use online services. However, many organizations need help with adopting this promising technology.
A recent survey by Ping Identity, which included responses from 700 IT decision-makers worldwide, highlights these challenges. In the UK, 82 percent of IT decision-makers see value in decentralized identities for their customers and employees, yet only about a third (34.5 percent) currently offer this option. A significant reason for this gap is the need for more clarity about the benefits, with 31 percent of respondents unsure what advantages decentralized IDs would bring.

One IdP to rule (or breach) them all: How identity access management tools can secure -- or destroy -- your kingdom
When we want to secure something highly valuable, say, a bag of ancient Spanish coins worth millions, we think of locking it behind as many layers as possible. For example, you might put it in a safe deposit box in a bank vault, nestled safely inside the institution that is itself blanketed with redundant physical security controls.
As organizations have become increasingly complex, so too have their associated layers of security around application access. Enterprises have tremendous amounts of applications and data, as well as users and devices with differing levels of permissions trying to access that data. To provide a consistent, IT-vetted method of creating, managing, storing, and authenticating the complexity of application access, we have arrived at Identity Provider (IdP) tools. IdPs are (typically) cloud-hosted services that store unique information used to identify users, organizations, and devices ("digital identities"), authenticate access requests, add/remove users, and provide security around these functions. Popular examples of solutions often used for IdP functionality include Okta, Microsoft Azure AD, and Duo.

The future of identity is self-sovereignty
It’s no secret that Americans are becoming increasingly concerned about their digital identities.
Take the recent case in Louisiana, where a whopping 6 million public records were exposed as part of a global attack on third-party file transfer app MOVEit. The attack made users more wary of trusting their data to often-obscure third parties. A recent survey, conducted across 1,000 U.S. consumers by Thales found that 44 percent are afraid their identity will be stolen in a cyberattack, and a quarter have no confidence in the protection of their personal data.

Why IAM alone is no longer sufficient to defend against today's evolving threat landscape
It’s a fact -- today’s businesses are using multiple, fragmented identity management tools to control access; and most are even paying for identity tools that they’re not even using. A recent survey found that 52 percent of organizations manage over 10,000 digital identities and 96 percent of those organizations have multiple identity management tools in place. More doesn’t always mean better protection, as 89 percent of organizations surveyed were still hit by an identity-based cyberattack in the last year.
Identity sprawl is a real thing and it’s an obstacle that is making many organizations more susceptible and more vulnerable to attacks.

Governing the ungovernable: Why cybersecurity must adapt to identity sprawl
You may remember the Colonial Pipeline ransomware attack. Launched in May of last year, DarkSide’s attack cost the Colonial Pipeline Company something on the order of $4.4 million dollars (though the FBI was able to claw some of that money back). The attack set the stage for President Biden’s Executive Order on cybersecurity, shut down pipeline production, and caused panic buying across the Southeast.
That’s how the Colonial Pipeline attack ended. It began far more simply: with hackers breaching the company’s networks through a virtual private network (VPN) account that was no longer actively in use.

Humans are predictable, even criminals
People’s lives are built around patterns and routines. Their routines are structured. After a while, they even become predictable. A change in routine, an abnormality, emphasizes the pattern itself. When we add a non-routine activity to our lives -- our actions usually indicate it will occur. For example, before a vacation we make plans, buy a ticket or book a hotel. Before we move to a new house, we usually visit the location several times, make money transfers and sign a contract.
In their study from 2010, Albert-László Barabási and his team studied the mobility patterns of anonymous cell-phone users and concluded that despite the common perception that our actions are random and unpredictable, human mobility follows surprisingly regular patterns. Their research eventually concludes that people’s movement patterns are 93 percent predictable.

Apple finally starts selling Magic Keyboard with Touch ID for M1 Mac computers
When Apple first unveiled its all-new iMac computers, owners of other M1 models, such as the Mac mini, MacBook Air, and MacBook Pro were quite excited. Why? Because the iMac had the option of a Magic Keyboard with Touch ID. This was Apple's first-ever wireless keyboard with an integrated fingerprint reader, and the iPhone-maker promised it would sell the keyboard as a standalone product in the future for use with other M1 Mac computers (not Intel).
Many consumers, including yours truly, have been religiously checking Apple's website in hopes the Magic Keyboard with Touch ID would show up for sale, but day after day, we were left with nothing but disappointment. Apple got our hopes up and then left us hanging.
