
Ransomware costs jump 17 percent though insurance claims fall
A new report from risk solutions company Resilience shows in the first half of 2025, the average cost of an individual ransomware attack rose by 17 percent, while the volume of incurred claims across Resilience's portfolio dropped by 53 percent, highlighting the persistent and destructive threat of financially motivated cybercrime.
Ransomware accounted for almost all (91 percent) of incurred losses, while financially motivated social engineering, especially via tailored attacks bolstered by AI-powered phishing content, fueled 88 percent.
Ransomware attacks up by 41 percent globally
New data from Check Point Research reveals a sharp rise in cyberattacks globally, with business services, healthcare, and manufacturing among the hardest hit sectors.
Ransomware incidents in particular have surged, with 487 attacks reported in July, a 41 percent increase year-on-year. North America accounted for 56 percent of all reported ransomware cases, followed by Europe at 24 percent.

Attackers exploit old vulnerabilities as zero-day exploits surge
New analysis from Forescout of more than 23,000 vulnerabilities and 885 threat actors across 159 countries worldwide during the first half of 2025 finds 47 percent of newly exploited vulnerabilities were originally published before 2025, and zero-day exploitation has increased 46 percent.
The report also shows ransomware attacks are averaging 20 incidents per day, zero-day exploits increased 46 percent, and attackers are increasingly targeting non-traditional equipment, such as edge devices, IP cameras and BSD servers. These footholds are often used for lateral movement across IT, OT, and IoT environments, allowing threat actors to get deeper into networks and compromise critical systems.

Companies pay multiple ransoms as attackers step up threat levels
A new report from Semperis, based on a study of almost 1,500 organizations globally, shows that hackers are stepping up threat levels and ransomware is still a global epidemic.
In 40 percent of attacks threat actors threatened to physically harm executives at organizations that declined to pay a ransom demand. US-based companies experienced physical threats 46 percent of the time, while 44 percent of German firms experienced similar forms of intimidation.

MSPs put aside dedicated funds for ransomware payments
According to a new report 45 percent of MSPs admit to having a dedicated pool of money set aside for ransomware payments. This is despite increasing pressure from insurers and global governments to avoid paying ransoms to stop fueling criminal enterprises and encourage proactive resilience.
The findings, from cyber risk specialist CyberSmart, also show that 36 percent opt to protect themselves with cyber insurance instead. Worryingly though, 11 percent of MSPs say they have no dedicated budget for ransomware payments or cyber insurance, in many cases leaving them without a contingency plan.

Matanbuchus 3.0 is a serious malware threat spread via Microsoft Teams
The Matanbuchus malware loader is not new – it has been around for at least 4 years – but it has evolved into something incredibly dangerous.
Matanbuchus 3.0 has been found targeting victims as part of a ransomware attack. Described as being “highly targeted”, the cyberattack campaign uses Microsoft Teams as a delivery method for the latest version of the malware loader. The highly sophisticated attack employs a Microsoft Teams call impersonating an IT helpdesk.

Ransomware surges 63 percent in Q2
The second quarter of this year has seen a 63 percent increase in publicly disclosed ransomware attack volumes, with a total of 276 incidents compared to Q2 2024, according to the latest report from BlackFog.
This represents the highest number of attacks for this timeframe since the company began tracking ransomware volumes in 2020. All three months in the quarter set a new high compared with the same time period in previous years. June saw 113 percent increase with a total of 96 attacks. There was a 51 percent increase in April with a total of 89 attacks, and a 40 percent increase in May with 91 attacks.

Encryption adoption up but sensitive data is still at risk
Encryption adoption has soared to 94 percent, but inconsistent application continues to put sensitive data at risk, finds a new survey.
The study from secure storage maker Apricorn shows that 59 percent of IT security decision makers say encryption has increased, allowing them to better protect their data, including on lost/stolen devices.

Ransomware is evolving faster than it's being stopped
The number of active ransomware groups has jumped 45 percent in the past year, according to a new report from GuidePoint Security’s GRIT team.
Covering Q2 2025, the report outlines how cybercriminals are regrouping, rebranding and using recycled tools to launch fresh attacks across industries.
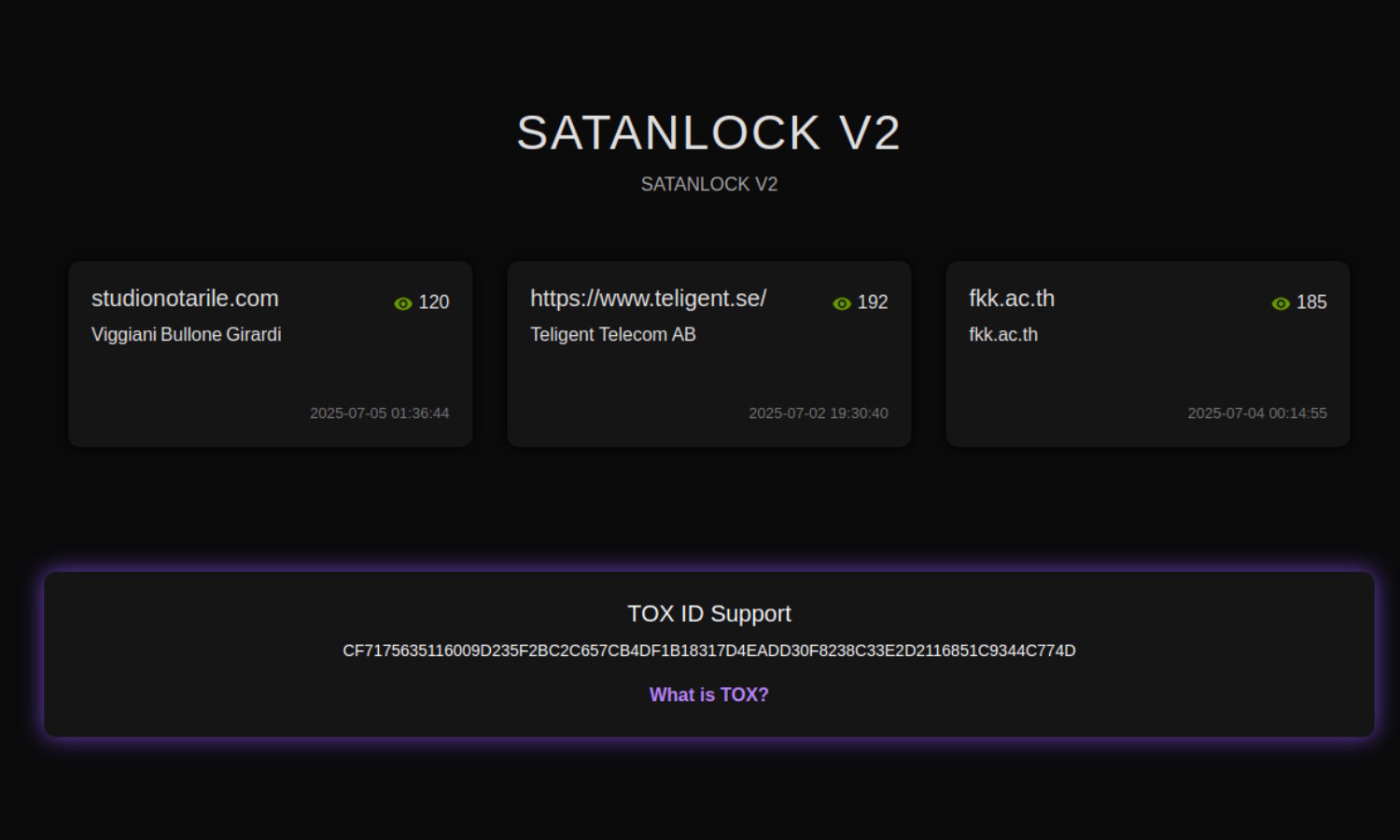
Short-lived ransomware group SatanLock to close down and leak data
There are large numbers of ransomware groups operating around the world, some of which have been conducting their nefarious work for years. There are older which are rather less long in the tooth, such as the recently formed SatanLock.
The group has been in existence for mere months, popping up in April this year. Responsible for a spate of attacks over a number of weeks, the ransomware group has announced that it is already shutting up shop. More than this, it plans to leak any data it has stolen.

Companies take an average of four months to report a ransomware attack
A new study from Comparitech, based on data collected from 2,600 attacks between 2018 and 2023, shows the average time for a US company to report a data breach following a ransomware attack is 4.1 months.
From 2018 to 2023, the average time to report a ransomware breach has increased, rising from 2.1 months in 2018 to just over five months in 2023. Healthcare has the lowest reporting time with 3.7 months, while businesses (4.2 months) and government entities (4.1 months) are similar.

Why conventional disaster recovery won’t save you from ransomware
The conventional formula for maintaining business continuity in the face of unexpected IT disruptions is as follows: Back up your data. Make a recovery plan. Test the recovery plan periodically.
That approach may work well enough if your primary concern is defending against risks like server failures or data center outages caused by natural disasters. But in the present age of widespread ransomware attacks, conventional backup and recovery planning aren’t always enough.

Ransomware attacks up over 120 percent in two years
Between April 2024 and March 2025, ransomware attacks escalated with unpredictable campaigns across a wide range of industries. The number of publicly disclosed victims also saw a 24 percent increase from the previous year.
A new report from Black Kite shows this follows a steep rise in the previous period with an 81 percent surge, amounting to a 123 percent increase over two years. Ransomware was responsible for 67 percent of known third-party breaches.

How ransomware became big business
On today's International Anti-Ransomware Day, cybersecurity company SentinelOne has publishes a blog looking at on how ransomware has evolved over the past 10 years.
It highlights how Ransomware-as-a-Service (RaaS) has matured into a scalable, profit-driven model, with revenue-sharing, affiliate recruitment, and performance incentives fuelling rapid expansion across the cybercrime ecosystem.

Ransomware attacks against government agencies on the rise
New analysis by Comparitech shows that government entities remain a frequent target for ransomware gangs.
Of the 39 confirmed attacks -- where the organization publicly acknowledges what's happened -- in April, 21 were on businesses, nine on government entities, six on healthcare companies and three on educational institutions.
