
How to get regular free security updates for Windows XP and Vista
Two months ago, in an effort to fightback against the WannaCry ransomware, Microsoft took the 'highly unusual' step of releasing a patch for Windows XP, the ancient operating system it stopped supporting back in 2014 (even though, as it turned out, it was really Windows 7, not XP, that was to blame for the spread of the devastating malware).
Then just two weeks ago, Microsoft included Windows XP and Vista -- another operating system it no longer supports -- in June's Patch Tuesday updates. Despite these recent actions, neither XP nor Vista are going to receive regular security updates from Microsoft, meaning users still running either OS remain at serious risk. However, the good news is there are a couple of tricks you can use to continue receiving security updates for both XP and Vista.

Platform enhancements protect enterprise mobile data without harming usability
As companies face ever greater demands for flexible working and BYOD use, it places an added stress on the need for securing mobile data.
Mobile app management specialist Apperian is addressing this with the launch of several enhancements to its platform aimed at increasing the security of enterprise mobile app data, without compromising usability.

Comodo launches free endpoint detection for enterprises
Hot on the heels of its enterprise threat analysis tool released last month, cyber security specialist Comodo is now launching another free enterprise tool with its endpoint detection and response (EDR) solution.
The fully-featured, enterprise-class, cWatch EDR solution is being made available at no charge to customers. This move enables any size of organization to better detect malware on endpoints, and investigate and respond to security incidents.

Don't ignore DDoS protection when attack trends change
Businesses should ensure that they are still securely protected against DDoS attacks, despite the recent growth of other trends such as ransomware.
That’s the warning from Arbor Networks, which is urging organizations of all sizes to make sure they stay safe online as DDoS attacks are still rife around the world.

UK parliament cyber attack highlights the shortcomings of passwords
As we reported over the weekend the UK parliament's email system was subject to a brute force attack using passwords stolen in the 2012 LinkedIn breach.
Security experts have been quick to point out the inherent weakness in large organizations and government departments relying on passwords to protect highly sensitive data.

Thanks to Word macros, Windows 10 S isn't as secure as Microsoft would have you believe
With Windows 10 S Microsoft has made the bold claim that this locked down version of its operating system is immune to all known ransomware. This may well be true, but that's certainly not to say that Windows 10 S is completely secure. Lock up your Surface Laptop!
An investigation carried out by ZDNet found that Windows 10 S -- despite only supporting the installation of apps from the Windows Store -- is vulnerable to that old security nightmare: Word macros. The problem comes about because the macros have full access to the Windows API, opening up a potential attack vector.

Businesses spend $2,300 to deal with a malware attack
To remedy a malware attack businesses need to shell out, on average, $2,300 per attack. This is according to a new report by Arbor Networks.
The report, produced in partnership with research organization 451 Research, says spear phishing attacks are still most successful of all the different methods of entry.

Russian hackers stole and sold passwords belonging to British politicians
An investigation by the Times has found that passwords belonging to British officials have been traded by Russian hackers. The passwords and email addresses of tens of thousands of politicians, senior police officers and diplomats were sold or swapped following an attack on LinkedIn in 2012.
As well as LinkedIn, some information seems to have been garnered from MySpace. The credentials for politicians, including education secretary Justine Greening and business secretary Greg Clark, were initially put on the market for sale or trade, but were later made available free of charge.

Cyber attacks and regulations don't change businesses' digital transformation plans
Businesses looking to digitally transform won’t be intimidated by cyber-attacks or data protection regulations, according to a new report by Advanced.
Based on a poll of more than 500 senior executives in UK organizations, Advanced says organizations are concerned, but won’t give up.

Cloud-native workloads gain momentum
A new survey shows that 18 percent of organizations now have more than half of their workloads in cloud-native environments. In addition many are moving from on-premises and self-hosting toward shared environments, distributing workloads across multiple providers.
The study by cloud security and network software firm Cohesive Networks also finds 57 percent of respondents say that cloud-native workloads make up at least 20 percent of applications in Infrastructure-as-a-Service (IaaS).

Virgin Media warns Super Hub 2 owners to change their passwords due to hacking risk
Virgin Media is urging hundreds of thousands of customers with its Super Hub 2 router to change their passwords after a Which? investigation uncovered a way for hackers to gain access to the device.
If the password for the router is not changed from its default there is a risk from hacking, but Virgin Media said the risk is small. Nevertheless, as a precautionary measure a password change is the advice for more than 800,000 users.

Microsoft Edge bug bounty program now permanent
Microsoft introduced a bug bounty program for Edge last August. Originally intended as a temporary thing, it will now live on as the software giant reports that it has lead to major improvements in its browser's security.
As is the case with bug bounty programs, part of the appeal for security researchers is the financial side. In this case, Microsoft says that it has paid over $200,000 in bounties in since it kicked off.

The value of information on the dark web
We're all familiar with the concept of the dark web where information gained from hacks and data breaches is traded amongst cyber criminals. But just how much are your identity and account credentials worth?
Password manager and digital vault app Keeper Security has produced an infographic looking at how much various pieces of information trade for.
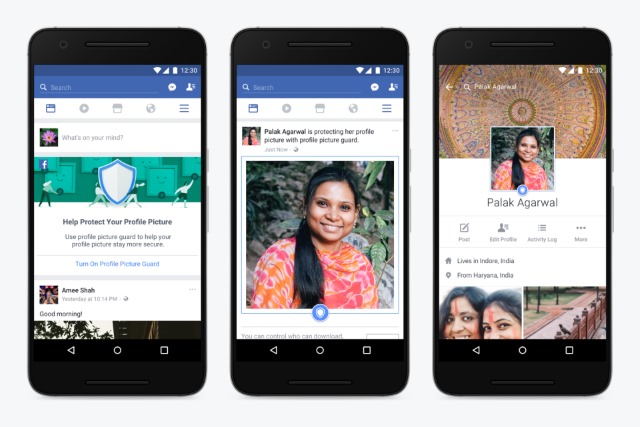
Facebook uses India as a testing ground for profile picture protection features
It's a common belief that anything that appears online is fair game for downloading and sharing, and this idea extends to Facebook profile pictures. Facebook has found that in India in particular there is great concern from users -- particularly woman -- about uploading a profile picture in case it is download and shared elsewhere.
Responding to this, the social network is trialling features that will grant users more control over their profile pictures. Facebook is not only introducing a new profile picture guard, but also encouraging people to add a design layer to their images to discourage misuse by others. If the trial proves successful, the feature will enjoy a wider rollout.

The journey from Microsoft Security Bulletin to Security Update Guides
For decades, the Microsoft Security Bulletins have provided IT administrators with a monthly list of vulnerabilities and accompanying patches. Much to the chagrin of the IT community, these Bulletins have been replaced by the Security Update Guides portal (SUG), which many administrators believe will be a lot more work for them, especially for patch management professionals who already have enough on their plate.
Moreover, the additional time to research and understand the security patches required for their unique environments will only lengthen the time to patch. While the portal is searchable by Common Vulnerabilities and Exposures (CVE), Knowledge Base (KB) article, product or release date, the change in process will impact the daily routines of IT administrators and security professionals around the world.