
First half DDoS attacks up 11 percent over last year
In the first half of 2021, cybercriminals launched approximately 5.4 million DDoS attacks, representing an 11 percent increase over the same period in 2020.
The latest threat intelligence report from NETSCOUT shows that in the first half of the year cybercriminals weaponized and exploited seven new reflection/amplification DDoS attack vectors putting organizations at greater risk.

September is for raising awareness of insider threats
If you haven't been paying attention you may not have noticed that September is Insider Threat Awareness month, with the aim of educating individuals and organizations on the dangers of insider threats and the forms they can take.
Almost half of organizations say they find it difficult to prevent insider attacks according to a recent study, which means it's more important than ever to understand the risk. We've gathered comments from a number of industry experts on the nature of the threat and how to tackle it.

Why quantum computing is a security threat and how to defend against it [Q&A]
Quantum computing offers incredible computing power and is set to transform many areas such as research. However, it also represents a threat to current security systems as cracking passwords and encryption keys becomes much easier.
So quantum is a security threat, but is there a solution to making systems safer? We spoke to David Williams, CEO of symmetric encryption specialist Arqit, to find out.

AMD issues warning about CPU vulnerability and releases a chipset patch
Security researchers have discovered a vulnerability in the AMD Platform Security Processor (PSP) chipset driver for multiple CPU architectures. Tracked as CVE-2021-26333, the security flaw is comparable with the likes of Spectre and Meltdown.
The vulnerability, found by ZeroPeril Ltd, can be exploited to grab data such as password from memory, and it affects a wide range of AMD processors. AMD has issued a patch which users are advised to install as soon as possible.

Office workers understand cyber risk but still don't change their behavior
Nearly a quarter (24 percent) of office workers have experienced a data breach, yet 12 percent say nothing will make them take cyber security more seriously, and a third won't take extra precautions.
A survey of over 2,000 UK office staff from BlueFort Security finds 34 percent believe cybersecurity awareness is the biggest issue when it comes to hybrid working, and 33 percent cite personal use of company devices as another significant risk.

Why SaaS security needs to have a higher profile [Q&A]
Increasing numbers of apps are moving to an SaaS model and containers, but the security of these applications doesn't always get much attention.
We spoke to BetterCloud CEO, David Politis who believes that SaaS security is an area that businesses need to take much more seriously.
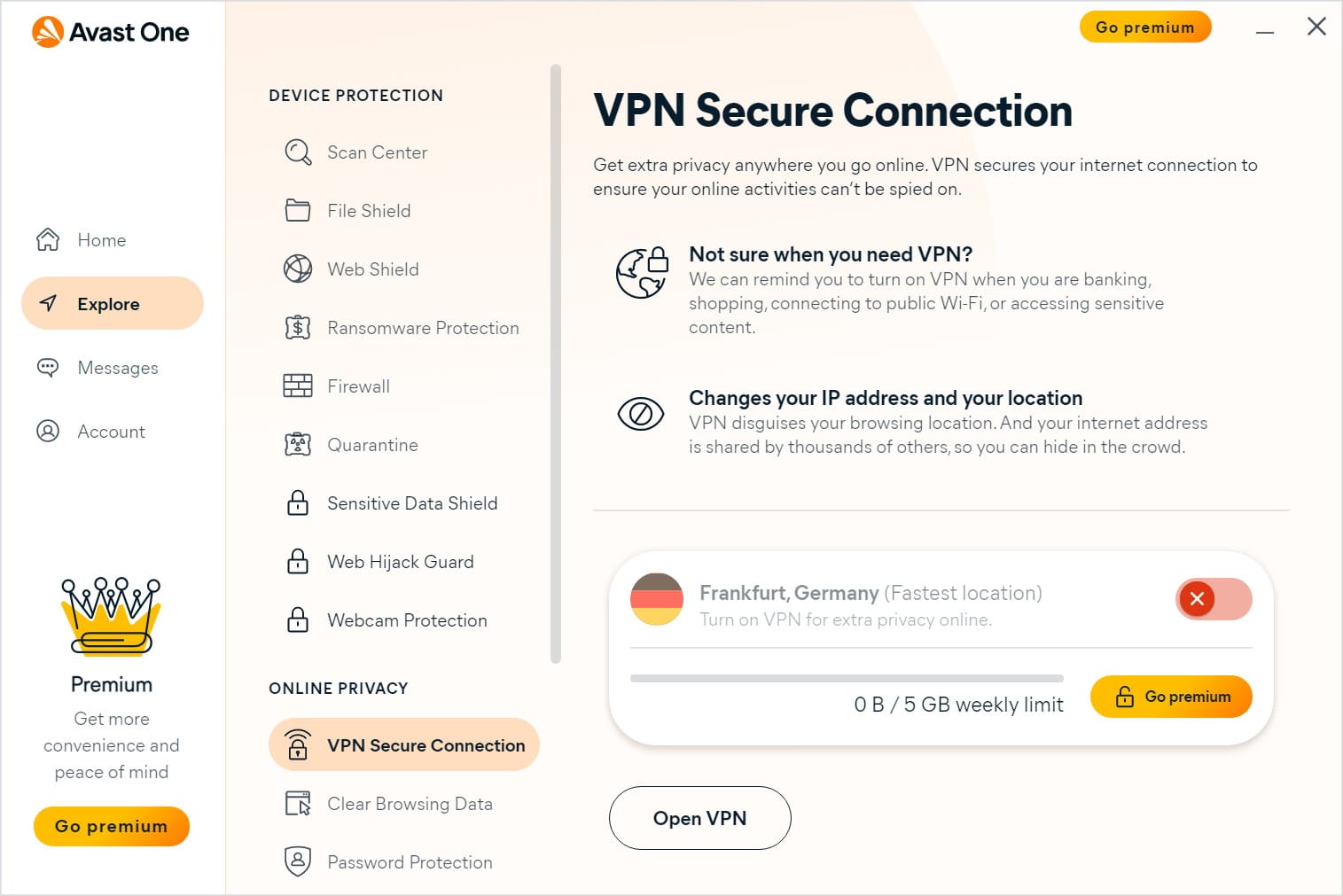
Avast One is a comprehensive privacy and security suite that includes a free VPN
Released at the same time as the company undergoes a redesign involving a new logo, Avast One is here to help keep you protected online. This is more than just an antivirus tool -- although an AV component is present -- this is a comprehensive suite of protective tools covering various aspects of security and privacy.
Things start off with Avast One Essentials, which is the free version of the security suite. For anyone with concerns about privacy, even this free version includes a powerful VPN with a generous weekly allowance. There is also protection against spyware, password theft and identity theft. And there is even more to explore in the paid-for editions.

Cybersecurity is not a one-stop-shop
Since the start of the pandemic, the way business is conducted has changed permanently, with many workforces continuing to work remotely as restrictions have eased. As companies relax and rules have eased, life is expected to return to a form of 'new normal.' But, the issues around cybersecurity are here to stay, and the gas pedal must not be eased -- especially with the increased risks associated with continued remote working.
If anything, security should be more reinforced now than ever before to ensure all aspects of a business are secure. But this isn’t the case.
Manufacturing data at risk from over exposure
Data security company Varonis has released research based on an analysis of four billion files across 50 organisations in the manufacturing industry and finds that there’s a huge problem of overexposure of data in the sector.
Every employee can access, on average, six million files on their first day on the job and four out of every 10 organizations have 1,000+ sensitive files open to every employee.

Organizations talk a good security game but fail to deliver
Organizations are prioritizing strategic security programs but are missing the capabilities they need to make meaningful changes to their security posture according to a new report.
The study by ReliaQuest, in partnership with Ponemon Research shows that 48 percent of organizations are prioritizing implementing zero trust principles as part of their security strategy.

New risk exchange helps companies meet cyber insurance criteria
Cyberattacks continue to be a problem for businesses and it's no surprise that cyber insurers are tightening up their requirements for policyholders to obtain new cover or to renew their existing cyber policies.
But in the past cybersecurity and cyber insurance have tended to operate in silos with insufficient coordination, leading to a misalignment between the cyber threats faced by an organization and the security measures needed to prevent them.

Now everyone can make their Microsoft account passwordless
Having already given commercial users the option of adopting passwordless sign-in, Microsoft is doing the same for consumers. Starting today, users have the option of removing the password from their Microsoft account and choosing different methods of authentication.
The move means that is now possible to access the likes of OneDrive, Outlook and other Microsoft services without the need to remember or enter a password. But this does not mean having to compromise on security.

2FA use grows as consumers look for better protection
A new report from Cisco's Duo Security arm shows that 79 percent of respondents report having used 2FA in 2021, compared to 53 percent in 2019 and just 28 percent in 2017.
Only 32 percent report using 2FA on all applications where available though, so there's still room for improvement.

Software vendors should be held to account for insecure build environments
A new survey from Venafi reveals that 94 percent of executives believe there should be clear consequences -- such as fines and greater legal liability for companies proven to be negligent -- for software vendors that fail to protect the integrity of their software build pipelines.
However, most have done little to change the way they evaluate the security of the software they purchase and the assurances they demand from software providers.

Remote working needs a change in security mindset
Although COVID-19 has meant a change to remote working, six out of 10 respondents to a new survey by Thales are still relying on traditional security tools and 44 percent are not confident in their ability to scale to remote work.
The study of 2,600 IT decision makers, commissioned by Thales and conducted by 451 Research seeks to better understand the new security risks and challenges caused by the rise of remote working and cloud transformation.
