'Easy Disk Drive Repair' is not what it seems
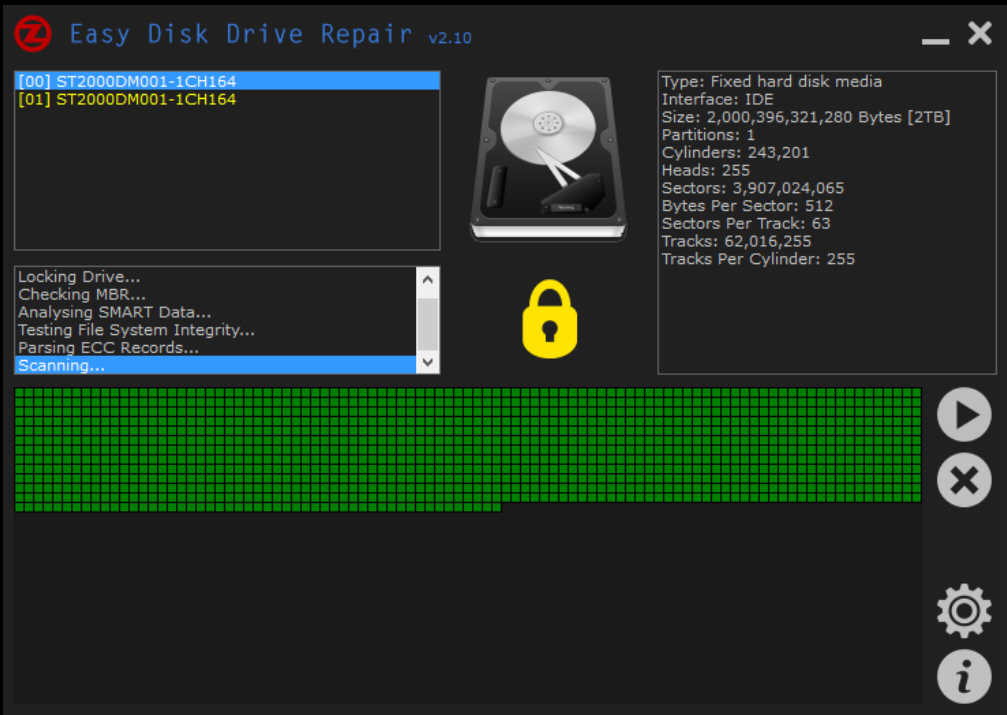
"Easy Disk Drive Repair" looked like a promising program. "An incredibly easy to use, yet powerful drive repair and maintenance tool", the developer claimed. Works with all drive types. More than one million downloads, five star awards plastered all over their product pages, and listed at big sites like Softpedia and ZDNet.
Sounded great, but we don’t like to copy and paste a developer’s description onto our own pages. We wanted to try it out, first.
Download and installation was straightforward. We launched the program, and -- what was that? A prompt -- "You must restart your computer to turn off User Account Control"?
This didn’t sound quite right, and sure enough, calling up the User Account Control Settings dialog showed UAC had been set to "Never Notify". Fortunately Windows doesn’t allow anything dubious until rebooting, so we returned UAC to its default position.
We wanted to understand this further. The excellent HxD hex editor is always useful in situations like this, so we launched it, and dragged and dropped EasyDiskDriveRepair.exe onto the program. This displayed the contents of the file in binary and hex views, and immediately we noticed the string "MSVBVM60.DLL" on the first page. That suggested it’s written using the ancient Visual Basic 6.0; not impossible by any means (VB6 can handle most technical tasks), but again a little odd.
Could VirusTotal tell us more? We pointed the site at EasyDiskDriveRepair.exe, and only 2/55 engines returned positives: DrWeb and TrendMicro-HouseCall (and the latter was only a "Suspicious_GEN"). Under normal circumstances we’d treat that as a likely false alarm.
To get a clearer view, we launched Process Hacker, found EasyDiskDriveRepair.exe in the list, double-clicked it and selected Memory > Strings. This displays more text strings the program might be using, and once more the very first page displayed something dubious: "HKCU\Software\Microsoft\Windows\CurrentVersion\DirectManipulation", something which could be used as part of an attempt to get more direct control over our Registry.
Another string showed a dubious Registry query: "C:\Windows\system32\cmd.exe" /c reg query HKCU\Software\Microsoft\Windows\CurrentVersion\Run /f "*chrome*" /d > c:\windows\temp.txt -- searching for Chrome being launched when Windows starts, and saving any hits to a temporary file.
Why Chrome? Clicking Filter in the bottom-left of the Strings box allowed us to search for Chrome references, and sure enough the program was trying to use sqlite3 to directly modify Chrome’s database: "sqlite3.exe “C:\Users\mikew_000\AppData\Local\Google\Chrome\User Data\Default\Web Data" "update keywords set url = url || ‘&tag=chrome20-20′ where url like '%amazon%' and url not like ‘%&tag=chrome20-20′;"
It doesn’t take any great expertise to realize that this looks very bad, but we wanted to complete the picture by running a complete scan with "Easy Disk Drive Repair" and using Sysinternals Process Monitor to capture what it did.
After a moment spent setting up a filter (If Process Name Excludes Repair then Exclude), we allowed "Easy Disk Drive Repair" to run a scan, and watched Process Monitor’s display.
The first thing we noticed is that, when the program claimed to be scanned our hard drive, it was actually just iterating through the same set of Registry keys and system files.
This probably isn’t too much of a surprise. Despite "Easy Disk Drive Repair" claiming it could "lock" our drive to run checks, Windows wouldn’t allow that. Even Chkdsk has to run its full scan at boot time as it can’t otherwise access the drive.
Once the scan had finished, we ran a Process Monitor text search for "Amazon", and found the program had created a file C:\Program Files (x86)\Mozilla Firefox\browser\searchplugins\amazondotcom.xml, as well as using the Chrome "update keywords set url = url || '&tag=chrome20-20' where url like '%amazon%' and url not like '%&tag=chrome20-20';" command we noticed earlier.
Our technical inspection had clearly shown "Easy Disk Drive Repair" was malware, but if you don’t have the patience or experience to try out various monitoring tools then there are other approaches to try.
The "developer" claimed over a million downloads, for instance, and to have been around since 2009, yet web searches showed hits for the last couple of weeks only.
The Downloads page claimed 5 star awards from various download sites, and all the right badges were there. But checking the individual sites showed they either didn’t list the program, or hadn’t given it 5 stars.
It can be worthwhile checking the reputation of a site, too. In this case URLVoid.com gave the developer site a clean bill of health from 30 reputation services, but it did give us another key piece of the puzzle: it had been first registered only 30 days ago.
The site itself tries to cover this by claiming the company had recently moved from "zeatronsoftware.com", but that appears to be another lie. A quick search shows the only mention of this site on the entire internet was on Easy Disk Drive Repair’s disclaimer page.
Just to complete the picture, web searches for the company’s co-founders also showed no signs of their existence.
Clearly, while technical analysis may help to conclusively identify malware, even just a few web searches will tell you a lot. We would say, keep that in mind. Don’t assume that antivirus engines will fully protect you. Be cautious, take a few minutes to check out programs which seem "too good to be true", and even a security novice should quickly pick out many scams.
