How to check if your Windows or Linux system is vulnerable to Microarchitectural Data Sampling (MDS) attacks

Intel yesterday disclosed a new group of Microarchitectural Data Sampling (MDS) hardware vulnerabilities that affect its CPUs.
Rogue In-Flight Data Load (RIDL), Fallout, and ZombieLoad speculative execution attacks are related to Spectre and Meltdown which were discovered last year, and allow attackers to leak in-flight data from CPU-internal buffers (Line Fill Buffers, Load Ports, Store Buffers), including data never stored in CPU caches.
SEE ALSO: Microsoft issues new patch for Windows XP to fight a dangerous 'wormable' vulnerability
You can find out more about the various vulnerabilities at CPU.fail.
The problem affects all modern Intel CPUs across servers, desktops and laptops, including the latest 9th-generation processors.
CPUs from AMD and ARM are not believed to be at risk.
Microsoft has already issued patches for the problem in some versions of Windows, and Canonical has also released updates for Ubuntu.
If your system is running on an Intel processor then you are very likely to be affected. You can check using the MDS Tool for either Windows or Linux which you can download from here.
It’s very easy to use -- just run it and it will tell you which processor you have and whether it is vulnerable to Direct Branch Speculation, Indirect Branch Speculation, Speculative Store Bypass, Meltdown, L1 Terminal Fault, and Microarchitectural Data Sampling.
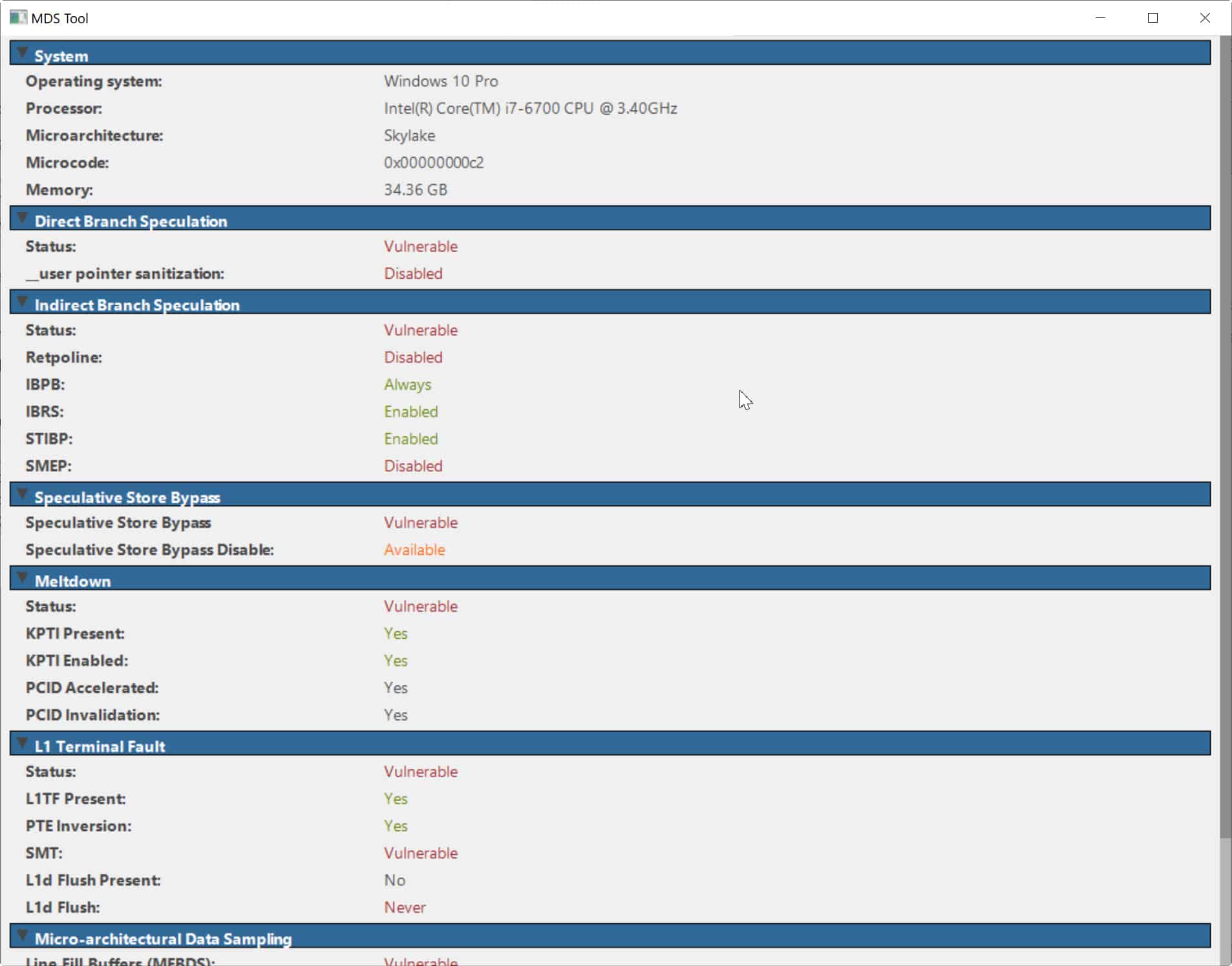
Image credit: spaxiax/Shutterstock