Do mobile operating systems provide enough protection against cyber threats?

Every year a new iPhone hits the market and there are thousands of different Android devices in circulation. Both Apple and Google are constantly adding new features and functions to incorporate emerging technologies, maintain competitiveness, and cement their reputations as innovators.
Commercial focus typically sits with the clamor of more surface-level, UI related features like Memojis, Group FaceTime, gesture navigation, the features that consumers are drawn to rather than the patching of CVE-2018-4249. It’s all a matter of priorities, people want a device with all the mod cons, a mobile device just needs to be secure enough, meeting minimum expectations. It also doesn’t help that there has been a long held misconception that mobile OSs are secure enough and users don’t need a security solution. Despite mobile OSs becoming relatively hardened, usage is very different compared to traditional form factors, and there are a number of threat vectors that an OS can’t protect against.
While mobile OSs are more secure than their PC counterparts, usage is very different and there are a number of threats that an OS cannot inherently protect against.
User Behavior
Ultimately, risk exposure is determined by a user’s behavior, with an obvious threat being jailbreaking on iOS or rooting on Android. This may not necessarily be a major issue under COPE and COBO models where configurations are tightly governed by an EMM or UEM, but it is definitely a risk that needs to be considered under BYOD.
The obvious danger with jailbreaking an iOS device is it allows third-party app downloads -- a risk that is always present on the open Android platform. Furthermore, apps on a jailbroken or rooted device can also run with escalated privileges so they can access the sensitive data of other apps on the device. One example is a fake Pokemon Go app which was found to include a remote access tool called DruidJack, enabling access to messages and contacts on a device, listen live or record audio via the microphone, install any APK as well as other malevolent features.
But, if you’re a savvy user, you may not even need to jailbreak an iOS device. The Apple Developer Enterprise Program enables organizations to test and distribute their own custom-built apps specifically for employee use only. The danger is that these apps are not held to the same standards as their more publicly available counterparts on the official App Store, and verification of businesses is lax. The Exodus spyware is an example of how Apple Developer Enterprise Program certificates have been used for malicious purposes.
The difficulty for security professionals is in ensuring that devices requesting access to corporate resources are in a secure state, free from malware and dangerous configurations. In COBO and COPE models, admins can apply hard and fast rules about a device’s security posture, but in a BYOD model, the lines between work and personal become blurred and a more dynamic approach to access management is required.
This is where Continuous Conditional Access (CCA) becomes important. CCA can assess a device, determine its risk posture and grant access to corporate applications accordingly. If a device has a risky app or an outdated OS, then a lower level of access can be provisioned to ensure that the individual can still be online, but mitigate an organization’s risk exposure.
Mobile Malware
Despite Google and Apple’s rigorous vetting processes, risky apps (intentional or not) still make it onto official app stores and accrue millions of downloads, take XcodeGhost for example.
There is a base level of security that the popular mobile OSs use to mitigate the damage caused by mobile malware once installed. Both iOS and Android use different flavors of app sandboxing to restrict communication between applications, ensuring that app data and code executions are isolated. By default, applications are given very limited access to OS features and can’t interact with other apps, permission needs to be explicitly granted by the user for further access.
But there is also a world of malware that doesn’t necessarily rely on app permissions alone to inflict damage. Take the recent example of malware on iOS where apps were found to be communicating with C&C servers used by the Golduck malware.
As well as intentionally malicious apps, there are completely legitimate apps that can also pose a threat, ranging from those that don’t encrypt data to those that behave like adware. WhatsApp’s latest app vulnerability enabled attackers to remotely install spyware onto targeted devices, demonstrating that even popular apps that are well-known for end-to-end encryption can’t be implicitly trusted.
In the case of mobile malware, there is only so much the OS can protect against. The Apple and Google ecosystems are set up with prevention in mind, stopping malicious and risky apps from ever reaching the device by using their respective official app stores as the gateway and contingency mechanisms on the OS -- unfortunately it’s not failsafe. Security professionals need greater granularity into how apps behave below the surface level interface, something an EMM or UEM doesn’t provide.
Phishing
Phishing has become the number one threat on mobile. It’s an attack vector that is largely misunderstood and underestimated. There’s not much mobile OSs can do to protect end users against phishing attacks given that they’re largely based on social engineering techniques and need protection at the network level to block connection to online phishing resources.
Organizations are typically well-fortified against email phishing on traditional form factors like desktop, but these technologies seldom extend to mobile devices. More importantly, phishing has evolved far beyond the realm of just email. Companies have adopted far more flexible communication models, which has led to an increased attack surface including SMS which is often used for 2FA
Take LinkedIn for example, it’s easy to see how a phisher could pose as a recruiter, prospect, partner or even a colleague and engineer an employee into giving away sensitive information. Additionally, research from the Anti-Phishing Work Group (APWG) noted that SaaS phishing attacks are on the rise, something that companies who are increasingly using cloud services need to consider when re-assessing their security strategies.
Email phishing shouldn’t be neglected though. According to the FBI, IC3 received 20,373 business email compromise (BEC) and email account compromise complaints, with estimated losses of over $1.2 billion in 2018, compared with 15,690 complaints and nearly $675 million in losses in 2017. Email phishing is becoming far more sophisticated and targeted, especially in the context of business attacks.
As always, awareness training provides an important first line of defense against phishing and more needs to be done to help employees identify phishing attacks, both on email and beyond. But, awareness training only gets users so far and some phishing attacks can be incredibly convincing. So a safety net is needed at the network level to block users from connecting to phishing pages.
Man-in-the-Middle (MitM) Attacks
The whole concept of mobility is to help employees be productive wherever they are, and sometimes that can mean relying on whatever Wi-Fi network is available. On average, mobile devices connect to 12 Wi-Fi connections per day and 55 percent of organizations have had at least one user connect to a risky hotspot in the past month. Connectivity is a challenge of the modern work environment and there is little an OS can do to assess how secure a network is.
It is easy to be duped by rogue hotspots. For example, an employee is remotely preparing for a meeting and heads into a Starbucks to fire off a few last minute emails. Below is a list of some of the SSIDs our users encountered, all of which demonstrated some form of risk.
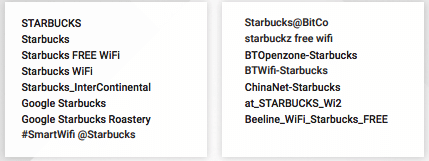
Assessing the security of a network is beyond the capabilities of a mobile OS, traditional security stacks and probably the skill set of many end users. It’s not an intuitive threat; a brand like Starbucks wouldn’t intentionally provide a risky network connection, but if improperly set up or there are bad actors snooping on the public network, then this could lead to the device and data being compromised.
Despite mobile OSs being relatively robust, they shouldn’t be relied upon as the only layer of defense. Modern security practices require a multi-layered, dynamic approach that provides granular insight into contextual signals and device behavior, an ethos akin to zero-trust. Without a mobile security solution in place, organizations will undoubtedly have blind spots in their security strategy.
Photo Credit: Voyagerix / Shutterstock
 Michael Covington is vice president of product at Wandera. He previously held leadership roles performing security research and overseeing product development at Intel Labs, Cisco Security and Juniper Networks. Dr. Covington is a hands-on innovator and has broad experience across the entire product life cycle, from planning R&D to executing on product strategy. With a diverse background as a seasoned computer science researcher, an IT professional, and an effective product manager, Michael has experienced technology from all sides, and enjoys bringing new innovations to market, specifically in the areas of security and privacy.
Michael Covington is vice president of product at Wandera. He previously held leadership roles performing security research and overseeing product development at Intel Labs, Cisco Security and Juniper Networks. Dr. Covington is a hands-on innovator and has broad experience across the entire product life cycle, from planning R&D to executing on product strategy. With a diverse background as a seasoned computer science researcher, an IT professional, and an effective product manager, Michael has experienced technology from all sides, and enjoys bringing new innovations to market, specifically in the areas of security and privacy.
