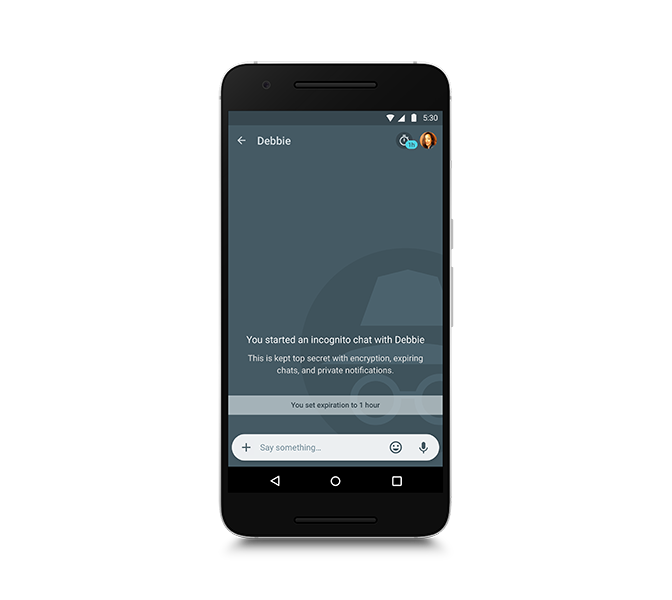
Google's new chat app Allo is a privacy nightmare
Four months ago, Google announced two new communication apps: Duo, for video calling, and Allo, for traditional WhatsApp-style messaging. Duo arrived for Android and iOS a month ago, while Allo is available from today.
While Allo is a good looking app, it has some big privacy issues that users need to be aware of.

Data lake management solution helps stop companies drowning in big data
While businesses are keen to get the benefits of big data, analysts find it hard to harness information across the enterprise and find relationships between data sets.
This can result in labor-intensive manual processes and a pool of unmanageable data that soaks up more and more resources in the quest for something useful.

Adaptiva launches serverless software distribution from the Azure cloud
Deploying software and updates to computers across a global enterprise from the cloud can be slow and expensive using traditional methods.
Systems management specialist Adaptiva is launching OneSite 6.0, a serverless option for distributing software from the cloud using Microsoft System Center Configuration (ConfigMgr) and Microsoft Azure.

Malware attacks are declining but getting cleverer
In the first six months of 2016 users were twenty percent less likely to encounter malware than in the same period last year. But although attacks are decreasing they’re getting more sophisticated and often disappear within hours having achieved their aims.
These are the key findings of the latest Webroot Quarterly Threat Report, based on information collected from millions of endpoints, released today.

Postbox 5 adds dynamic content support, anti-tracking features
Postbox, Inc has released Postbox 5.0, a major update to its Windows and Mac email client. Version 5 showcases a new look with high-DPI support in Windows, plus adds dynamic data support to responses and templates.
Other highlights include a new anti-tracking feature, Quick Post tool, new per-image scaling tool to help keep message sizes down, and global filters. There’s also 25 professionally designed email signatures and 70 business templates.

Microsoft finally removes its scummy Windows 10 nagware from Windows 7 and 8.1 systems
15 months ago, in an effort to make it as easy as possible to upgrade to its new operating system, Microsoft introduced a Get Windows 10 app for Windows 7 and 8.1 that allowed users to reserve their upgrade.
While this tool was innocuous enough to start with, it soon turned into something much more akin to malware, becoming harder and harder to kill, and employing all manner of scummy methods in an effort to trick users into installing Windows 10 against their wishes.

Businesses spend nearly $3 billion a year on mobile connectivity
The cost related to mobile connectivity through roaming, pay-on-demand Wi-Fi and free Wi-Fi is costing businesses in Europe and North America at least $2.91 billion every year. This is according to iPass, provider of global mobile connectivity.
The cost is high because, as the report puts it, mobile professionals have an "insatiable need for connectivity". When traveling and working on the go, they spend on average 6GB every month. The report has an interesting conclusion -- free Wi-Fi is not always as free as you’d think. These connections, being available to everyone, can often be slow, unresponsive and crowded. Business users are then stuck on these slow connections, which are hurting their productivity, which then reflects on the bottom line.

Education and government suffer most from ransomware
The highest rates of ransomware are now found in the education and government sectors according to the findings of a new report from BitSight.
The report looks at how ransomware is impacting almost 20,000 companies in six major industries: finance, retail, healthcare, energy/utilities, government and education. The findings show that the rate of new ransomware strains, such as Locky and Cryptowall, has spiked over the last couple of years, and numerous industries are beginning to fall victim to these ransomware attacks.

Microsoft's Surface Phone set to have a fingerprint sensor
Windows Phone sales are currently insignificant -- according to Gartner, during Q2 2016 Microsoft’s mobile operating system claimed a share of just 0.6 percent worldwide -- and with no new Lumias on the horizon, it seems a fair bet to say the platform is doomed.
But not so fast. Microsoft is still banking on Windows 10 Mobile, and it’s long been rumored that the company has plans for a Surface Phone. There’s nothing concrete known about it at the moment -- will it be a single device, or a whole new family? -- but one thing that does seem likely is it will have a fingerprint sensor built in.

Oracle buys cloud security company Palerra
Oracle has announced that it will purchase the cloud access security broker (CASB) Palerra, making this the company's eight acquisition in 2016.
The deal was announced at the beginning of Oracle OpenWorld in San Francisco and the amount which the company is paying for Palerra has yet to be disclosed. Oracle made the decision to purchase the company for its Loric software product as it "protects and assures compliance of applications, workloads and sensitive data stored across cloud services".

Apple releases macOS Sierra as free upgrade
Apple's Mac computers -- MacBook, iMac, Mac Pro, and Mac mini -- are works of art. Not only is the hardware beautiful, but the included operating system is visually impressive too. Today, after a series of Beta releases, the final 10.12 version of the desktop operating system formerly known as OS X -- now known as 'macOS' -- is available for download. Apple dubs the latest version of the desktop operating system 'Sierra', after a mountain range in the company's home state of California.
While Windows 10 is a great operating system for productivity, Microsoft simply cannot match the visual beauty of macOS. Still, Microsoft's latest operating system does offer some unique features, such as the voice assistant Cortana -- something that Apple's desktop did not offer. Today, this changes, as the legendary Siri comes to macOS Sierra. Best of all? As usual, this is a free upgrade for owners of compatible Mac computers!

Google brings more of its search features to Drive
Say what you want about Google, but most people love the company for its plethora of free services, like Search, Gmail, Chrome and much more. Today, the search giant brings better integration to one of its popular services -- Drive.
First up is what Google calls "search the way you talk". This means that you can simply type how you would say something and Drive will bring up the best matching result for you.

Server sales are up, but revenue is down
New research has revealed that despite increased server sales, revenue has continued to decline for the companies responsible for manufacturing and shipping servers worldwide.
The analyst firm IDC brought this information to light in its new Worldwide Quarterly Server Tracker report, which covered server market share and revenue from April to June 2016.

SanDisk announces world's first 1TB SDXC card
My first computer in the 1990's came with a 4GB hard disk drive -- very spacious at the time. When my friends saw the capacity, I was instantly the envy of the neighborhood. Nowadays, 4GB is rather pitiful. Modern memory cards, some smaller than a postage stamp, can dwarf my first computer's capacity. That's technology, folks -- everything gets better, and your current tech loses its luster.
Today, SanDisk (a Western Digital company) announces a product that is a major milestone in the technology market -- the world's first 1TB SDXC card. In other words, that is a monstrous 1,000 gigabytes. To put that in perspective, Apple only just stopped putting 16GB storage capacities in the iPhone. This card, which is only a prototype for now, will be a dream for photographers, allowing them to save more photos than ever before. Of course, if the card fails, that is a lot of data to lose...

Information Security Forum helps businesses guard their 'crown jewels'
Traditional approaches to deploying security controls don't always provide appropriate or sufficient protection for mission-critical information assets.
Aiming to support enterprises in guarding this information, the Information Security Forum (ISF) is launching 'Protecting the Crown Jewels', a series of reports based on the ISF Protection Process, to help organizations formulate a structured, methodical process to deliver comprehensive, balanced protection.


