
Ubuntu Cinnamon becomes an official flavor, making Linux Mint obsolete
Linux Mint is a fairly popular operating system. But why do so many people use that Ubuntu-based distribution? People may tell you several reasons, but the reality is, many Ubuntu users are just not comfortable with the default desktop environment.
Because Unity, and now GNOME, are so radically different from the traditional Windows interface, some people flocked to Linux Mint and its familiar Cinnamon desktop environment. Mate and Xfce are Mint desktop options too, but make no mistake, Cinnamon is the crown jewel of the distro. Sure, there are other nice aspects of Linux Mint, but ultimately, it is familiarity with former Windows users that make the OS attractive to many.
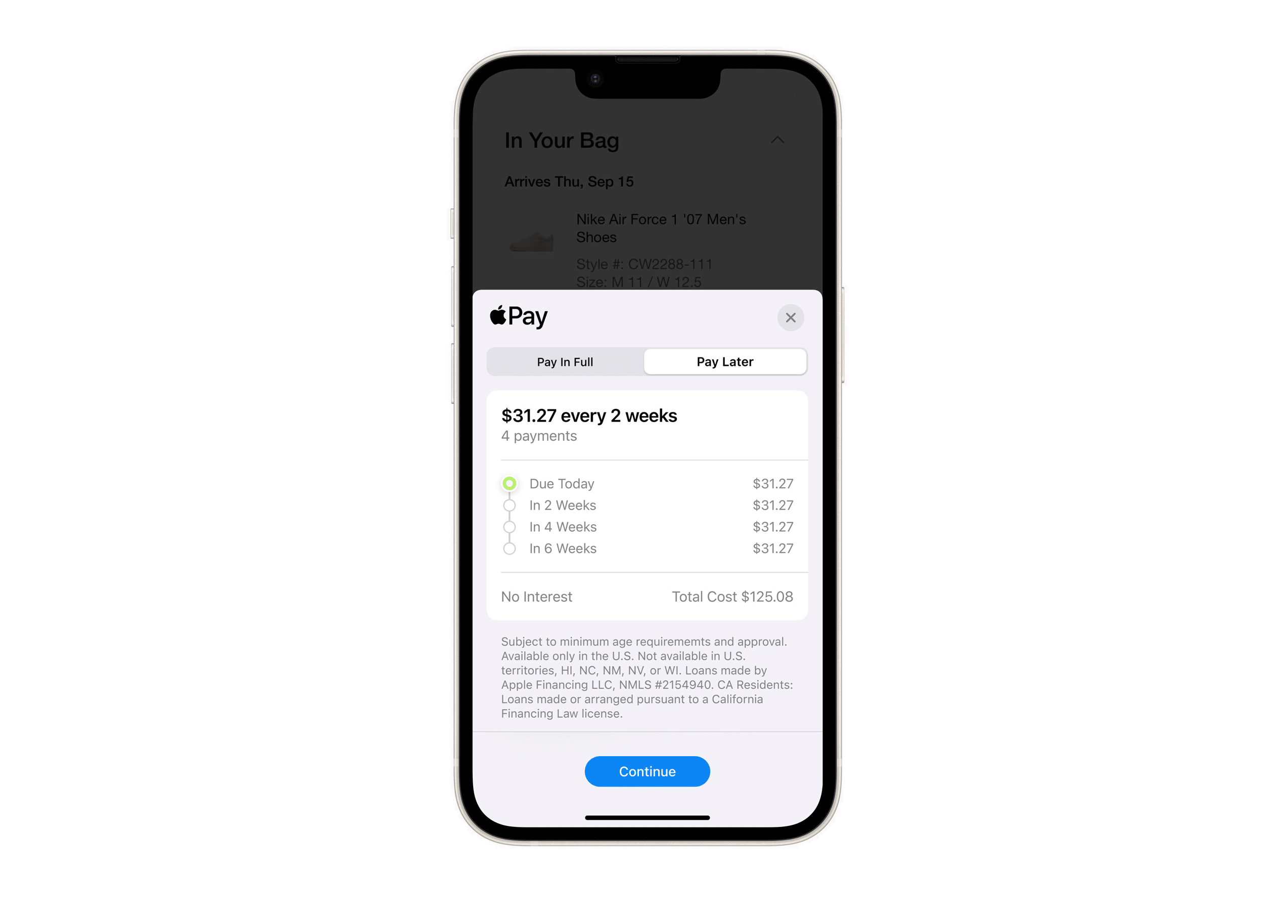
Apple Pay Later: A new way to pay for your purchases
Today, a prerelease version of Apple Pay Later is being launched. This is a new service that allows Apple Pay users to split their purchases into four equal payments -- over six weeks -- with no interest or fees. Apple Pay Later is available for purchases in apps and online when customers check out with Apple Pay.
Apple Pay Later is a convenient way to finance purchases that customers may not be able to afford to pay for all at once. However, it is important to note that Apple Pay Later is not a loan. Customers are not borrowing money from Apple or from a bank. Instead, they are simply splitting their purchase into four equal payment. Goldman Sachs is involved with the process, however.
Microsoft unveils Security Copilot, its next-gen AI-powered weapon against cyberthreats
Microsoft today announced Security Copilot, a new tool designed to bring its next generation AI to cybersecurity.
The software can quickly detect and respond to threats, and also gain a better understanding of the threat landscape. In addition, Microsoft says it "will learn from existing intelligence, correlate threat activity, and make more informed, efficient decisions at machine speed".

Disruptions to eCommerce cost businesses up to $1 million a month
A new survey of retail and consumer brands shows that nearly 40 percent of all respondents suffer customer-impacting disruptions, which cost up to $1 million per month.
The survey, conducted by Forrester Consulting on behalf of Catchpoint, finds 61 percent of respondents say internet disruptions have resulted in lost revenue, while 64 percent report damage to their brand's reputation that led to lack of consumer confidence.

Companies struggle to protect against insider risks
Although more than 70 percent of companies say they have an insider risk management (IRM) program in place, the same companies experienced a year-on-year increase in data loss incidents of 32 percent, according to a new report from Code42 Software.
Based on a survey of 700 cybersecurity leaders, cybersecurity managers and cybersecurity practitioners in the US, conducted by Vanson Bourne, the report shows 71 percent expect data loss from insider events to increase in the next 12 months.

Stolen credentials and the rise of the 'traffers'
Even as we move towards passwordless authentication methods, stolen credentials remain a major problem for businesses.
A new report from cyber risk management company Outpost24 highlights the increasing professionalization of the market for stolen credentials thanks to the rise of what are known as 'traffers'.
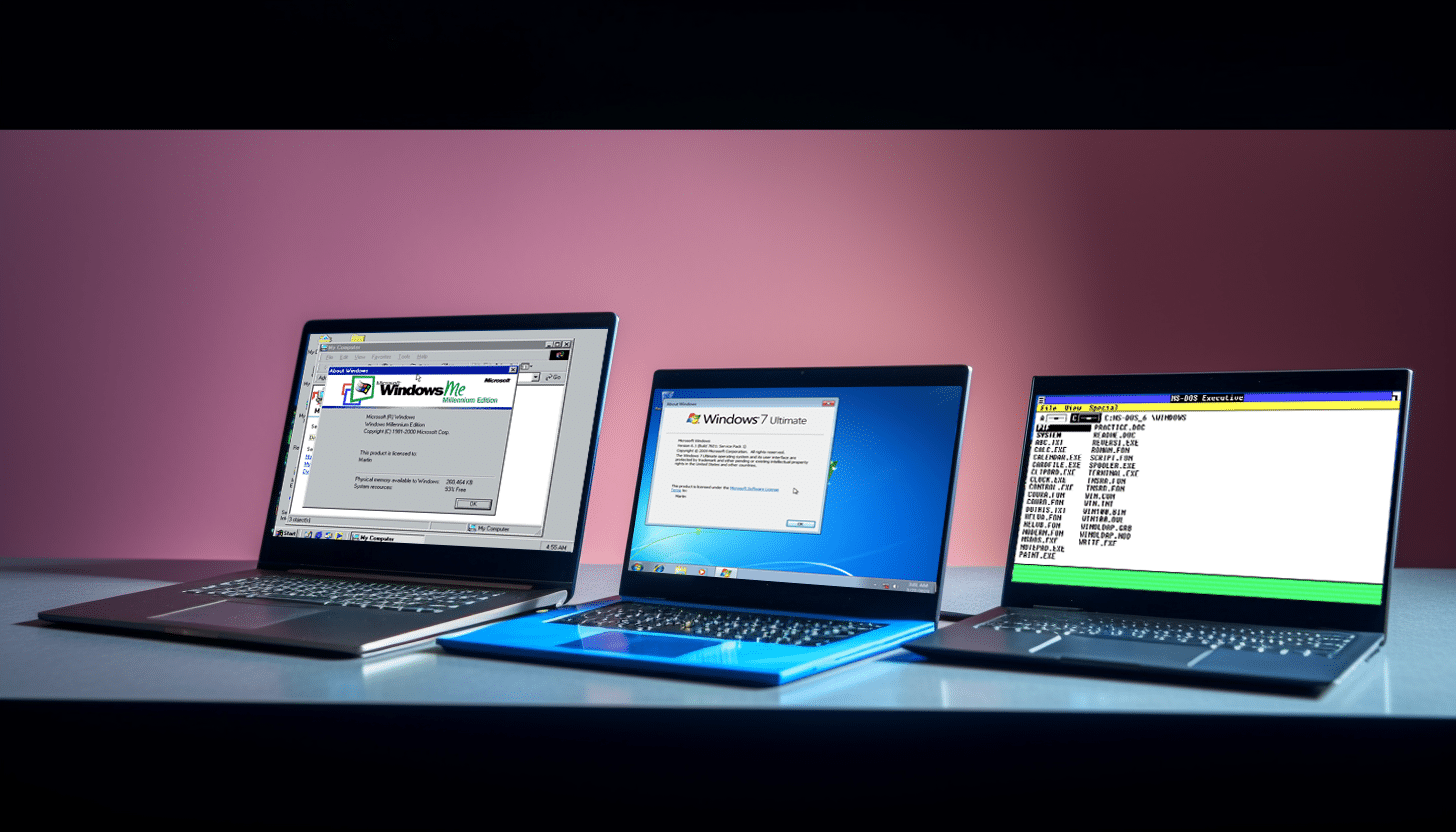
Downgrading Microsoft Windows -- from Windows 11 to Windows 1.01
From Windows 1.01, released in 1985, to Windows 11, introduced in 2021, each iteration of Microsoft's operating system has brought its own set of features and improvements.
Windows 1.01, with its simple and straightforward interface, marked the beginning of an era of graphical user interfaces for the PC. Windows 2.0 introduced support for expanded memory and improved support for graphics, paving the way for more sophisticated programs and applications. Windows 3.0 brought a more refined interface, with a greater emphasis on multitasking and performance.

75 percent of SaaS applications pose a risk to enterprises
The past few years have seen massive growth in the number of SaaS applications used by enterprises, but new research from Spin AI shows that 75 percent of SaaS applications pose a high or medium risk to data stored in either Google Workspace or Microsoft 365.
On average, 35 percent of apps with OAuth permissions to Google Workspace or Microsoft 365 are classified as high risk. For large organizations (with more than 2,000 employees) 56.91 percent of apps pose a high risk.
Microsoft has rebuilt Teams from the ground up to make it faster and less resource-hungry
Microsoft has launched a public preview of the new Microsoft Teams app for Windows. The app is the result of a "reimagining of Teams from the ground up", with the focus very much being on performance. It is being heralded as "the new era of Microsoft Teams" and sees the app not only performing better, but also being simplified to improve ease-of-use.
At the same time, the company has also started the rollout of Avatars for Microsoft Teams. The new feature gives users a different way to present themselves in online meetings -- a highly customizable 3D avatar instead of video.

Elon Musk says that only verified (i.e. paying) Twitter users will be able to vote in polls and appear on the For You tab
Having tried various tactics to get Twitter users to pay for a Twitter Blue subscription, Elon Musk is now trying something new -- confiscation.
Having tried bribing users with Blue-exclusive features, and threatening non-subscribers with stripping them of verified status, the latest announcement sees Musk promising to take features away from anyone who doesn't pay up. Specifically, he warns that non-verified users will not be eligible to appear in the suggestions on the For You Tab, and they also will not be able to vote in polls on Twitter.

The future of networking: Innovation, transparency and connectivity
As technology continues to evolve, the networking industry is experiencing significant changes that will have a profound impact on businesses worldwide. The key areas where we expect to see developments include innovation driven by the major cloud providers, accelerated connectivity, and the need for transparency into the network.
These trends represent key factors that can enable businesses to drive innovation and competitiveness, even in the face of an increasingly challenging economic environment.

Evolving vulnerabilities in the education sector: How can organizations become more resilient?
In 2022, the education sector experienced a 44 percent increase in cyberattacks. In the UK alone, six in ten higher education institutes reported experiencing at least weekly attacks or breaches. This increasing number of threats to the sector is causing major disruptions to teaching and even forcing schools and universities to shut down.
When it comes to prioritizing security and adopting latest technology, the education sector has always lagged behind other major industries. This lack of urgency is party the reason why education is such a vulnerable target. Many schools are still using outdated and unprotected technology that is easy to infiltrate. Despite not being a cash-rich target, these facilities hold a wealth of personal and financial data, which can be used in future attacks or sold on the dark web.

Okta launches identity verification for Zoom users
Many organizations have come to rely on Zoom as a means of connecting employees and customers in a hybrid environment.
But this comes with challenges when it comes to keeping meetings secure without harming productivity. Identity management platform Okta is launching a new identity verification feature that will authenticate Zoom meeting attendees in End-to-End Encryption (E2EE).

Banks lack transparency over their use of AI
Banks across North America and Europe are failing to publicly report on their approaches to responsible AI development, according to new research from Evident.
While AI is already used by banks for many critical processes, from authenticating customers to risk modeling, eight of the 23 largest banks in the US, Canada and Europe currently provide no public responsible AI principles.

Integrating security into the development process [Q&A]
Historically, security has been treated as something as an afterthought in the IT industry. In more recent years though there has been pressure to introduce 'security by design' to ensure that products are developed with best practices in mind.
We spoke to David Melamed CTO of Jit to find out about integrating security and how security tools can be used by developers not just security professionals.



